A year since Google added Restore Credentials to Android’s Credential Manager, the no-fuss utility is generating noisy results. By bringing a person’s in-app sign-in state to the new device, the feature is removing one of the momentous pain points when upgrading your phone — and numbers indicate it’s making a significant improvement on churn and frustration.
Why Login Restore Is A Big Deal On Android
It was an inconvenience: For years, changing Android phones meant going through the hassle of reinstalling apps and signing into many of them, just to get notifications, order a ride or open a file. That gap has long been a competitive advantage for iOS, which considers most app sign-ins in device migration. The impact on Android was minimal-but-huge: after delayed notifications, abandoned sessions and a flickering “reset” feeling on users who were expecting state, somehow this put a downer on the whole party.
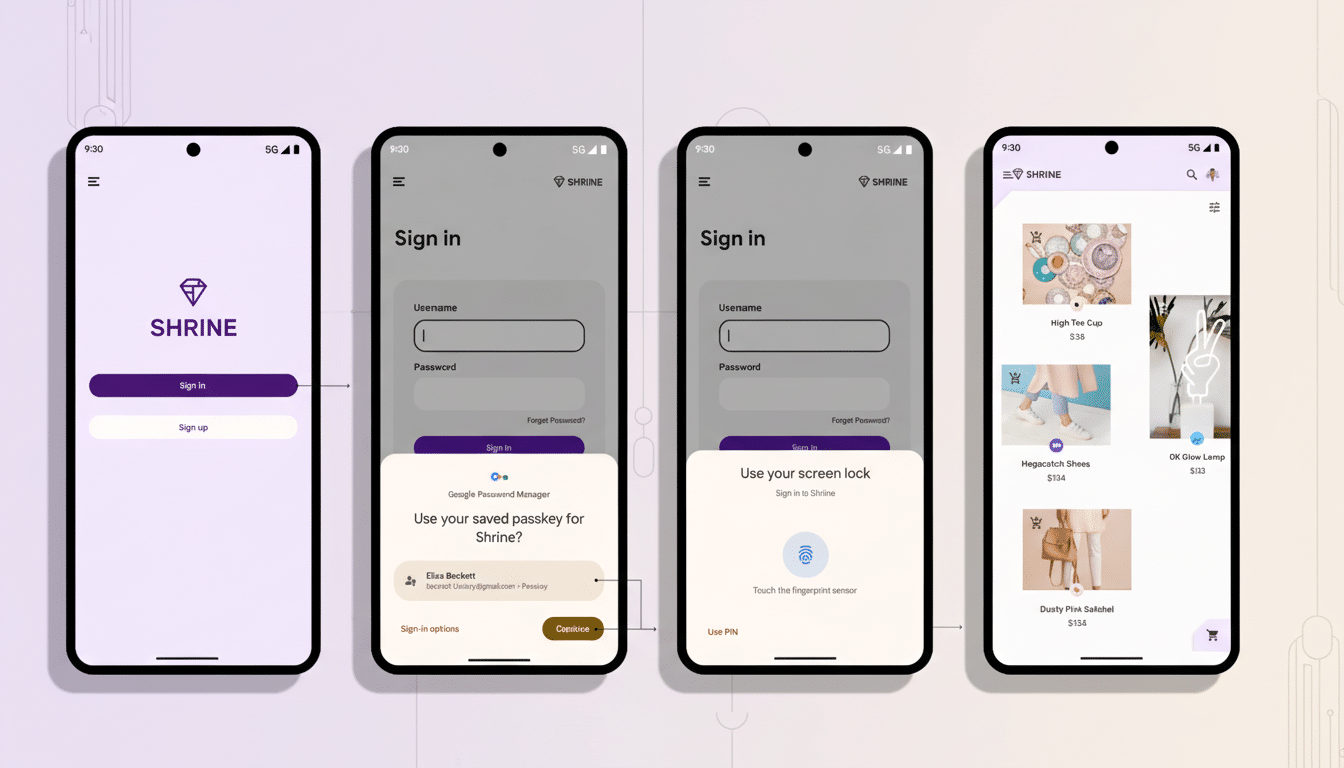
This is directly addressed by Google’s Restore Credentials, which allows developers to provide the old device with a secure, app-scoped token that can be recovered on the new device during setup. Rather than making the user re-input passwords or wait for one-time codes, the app can quietly reconnect to a trusted session — or at best provide quick-sign-in access from the first tap of launching an app. Restore is being offered as an additional option alongside passwords, passkeys and federated sign-in within Credential Manager, and the idea is designed to be opt-in per app.
How the Android Restore Credentials Flow Works
Concretely, an application on the existing device creates a restore token that is associated with that account and app signature. When a device is provisioned, the backup and restore mechanism in Android sends this token to the new device, encrypted. Upon a successful migration, the app itself can identify that token and automatically resume the session (and optionally remove that username/password info). Google’s developer guidelines advocate for scoped, time-limited tokens, not raw credentials, and align with the platform’s backup policies and hardware-backed protection.
Crucially, developers control the experience. For certain categories, like banking, opting not to preserve sign-in states is an option. Some can go farther still, with so-called completely silent background restoration that ensures notifications and deep links fire right after the setup process. This flexibility enables teams to trade off ease of use and risk, as defined by their threat models.
Uber’s Results Are A Sign Of Real Impact
Uber offers the clearest early data point on this. Indeed, based on data from Uber’s engineering team, the addition of Restore Credentials in-app removes around 4 million manual logins a year — millions of instances when a user would have been blocked at just the wrong time for them to get where they needed to go. In its staged rollout, Uber observed close to 10,000 unique daily users who restored sign-in per day through the new flow, which it expects to double as adoption grows.
(Uber’s current setup does still require the user to open the app once on the new device in order to complete restoration; even so, the savings are great.) And Google says developers also can opt into full background restore so an app could be fully prepared to send notifications and accept actions as soon as the migration is complete, without requiring the user to open it first.
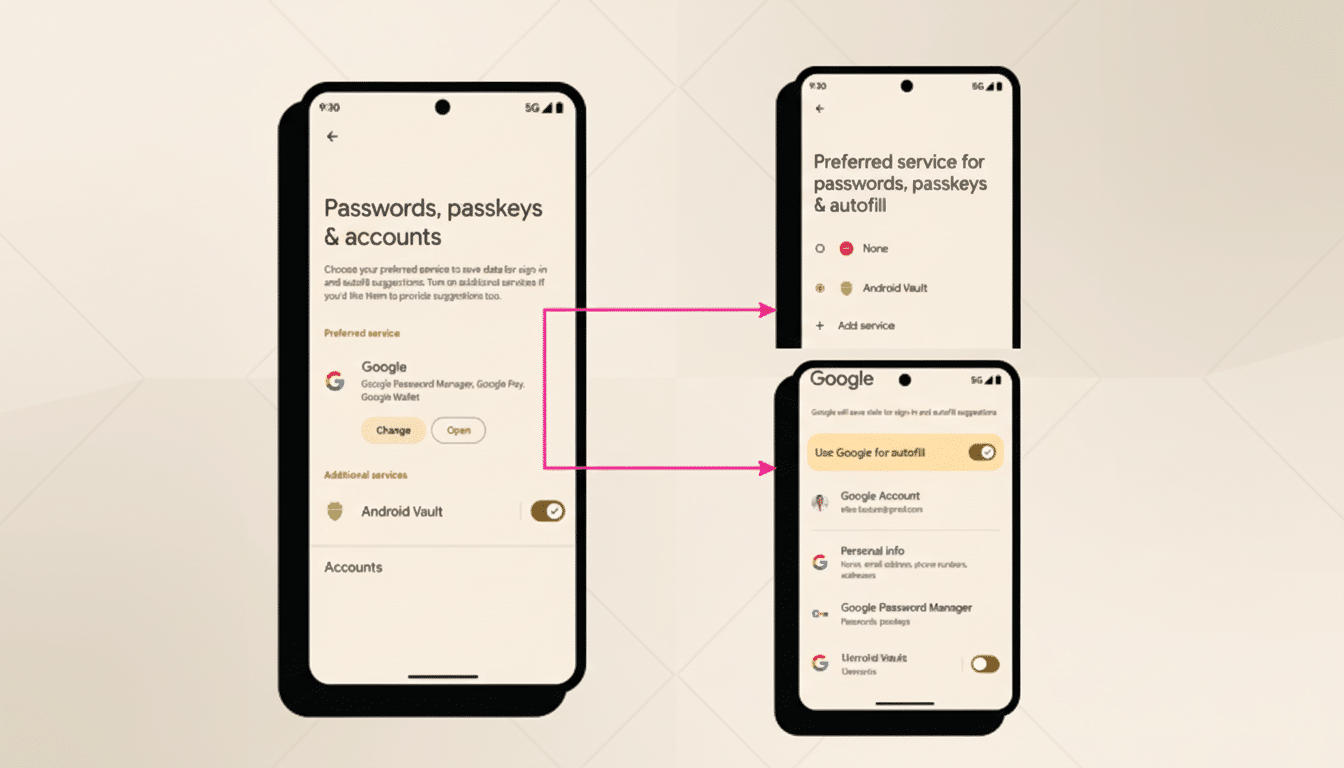
What It Means For Developers + Product Metrics
Login friction is a number-one source of drop-off in day-one retention and help tickets, so say our analytics providers and mobile growth teams, and the trend persists. Each password prompt, OTP wait or email verification in device migration is a dead end waiting to happen. Restore Credentials shortens that funnel: fewer abandoned carts, more successful first sessions, and quicker reactivation of push notifications to spur engagement.
Implementation can be quite lightweight for apps already utilizing modern session management, as there are short-lived, app-scoped tokens returned and no storage of credentials. Teams already using passkeys or federated sign-in via Credential Manager may adopt mixed strategies to get a restored state during migration, while also having a clear UX fallback in non-restore scenarios.
Playing Catch-Up With iOS on Seamless App Sign-In Restore
On iOS, the sensation of “everything just works” after a phone upgrade has long been an advantage, with iCloud Keychain and system restore preserving most app states. Restore Credentials is Google’s most explicit response for Android, and initial signs are it is closing that UX gap without hampering developer choice or risk appetite.
Security-sensitive applications can still opt out, and that is fine. But for rideshare, food delivery, productivity, media, travel and social apps, getting restore sign-in can be a low-risk/high-reward improvement that pays back in retention and satisfaction.
The Road Ahead for Android’s Restore Credentials
Google’s developer outreach and use cases it showcases, as reflected in Android Developers materials, are explicitly intended to drive adoption. The case of Uber provides product leaders with a real business use case: ditch millions in logins, reduce support load and lift day-one activation — all without taking on much (if any) UX debt.
The next milestone is scale. As additional high-usage apps support background restoration and set the session policy in synchronization logic, upgrading to a new Android device should begin to feel as smooth as users would expect. This is finally starting to pay off. For a feature that was created to be invisible, Restore Credentials is starting to become visible!

