An international law enforcement action targeting the operators of a cryptocurrency mixer service has resulted in the closure of Cryptomixer, which allegedly laundered €1.3 billion ($1.27 billion) worth of bitcoin on behalf of hackers. Investigators, who were coordinated by Europol and involved national cybercrime units as well as Eurojust, confiscated some €25 million in bitcoin, three servers, 12 terabytes of operating data and the platform’s main domain — which, at the time of writing, showed a notice saying: “This hidden site has been seized.”
Authorities say Cryptomixer is a high-volume mixing service that sought to help criminals obfuscate the source of their virtual currency transactions before depositing them into money mule accounts and/or cashing out at currency exchanges.

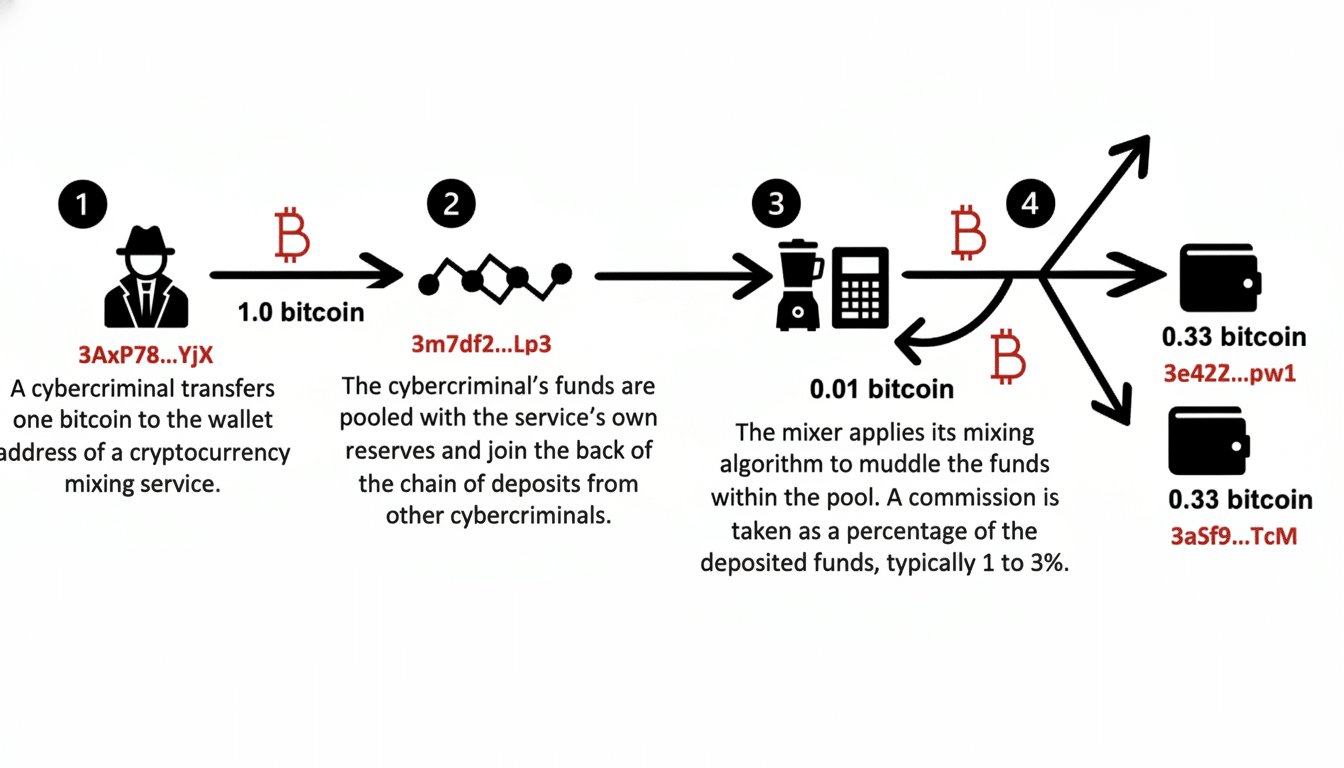
How the Mixing Scheme Operated to Obscure Transactions
Mixers aggregate the deposits of many users, mix funds for unpredictable periods and time pacing, and send outputs to new addresses in different amounts and at different times. The aim here is to break the on-chain links between transactions and thwart blockchain analysis that would otherwise follow those transactions from public ledgers like Bitcoin’s or Ethereum’s.
Cryptomixer boasted that it could help “block traceability,” according to Europol, invoking a marketing trope often matched with specific technical techniques like multi-hop splitting, time delays and address rotation. In reality, however, authorities are still able to pierce through these layers when they seize servers, logs and wallet infrastructure, which allows them to correlate on-chain flows with off-chain metadata and operational profiles.
Seized Assets Provide a Forensic Road Map
More likely, the three servers and 12 terabytes of data are, themselves, the prize. In possession of configuration files, transaction notes and user interaction elements, analysts could map service wallets to cluster-joined addresses and attribute deposits to ransomware strains as well as market accounts (and money mule networks).
Companies like Chainalysis, Elliptic, and TRM Labs provide these teams with services that combine raw blockchain data with typologies of criminality. When combined with exchange compliance records and subpoenas, seized data sets can cascade into a series of follow-on actions, from frozen accounts to the arrest of high-volume mixers’ customers and associates.
Part of Broader Crackdown on Crypto Laundering
Lawmakers in Europe and the U.S. have increasingly focused on laundering infrastructure. The U.S. Treasury sanctioned Tornado Cash amid claims it had helped enable over $7 billion in transfers since launch, including funds connected to North Korea’s Lazarus Group. Law enforcement also shut down ChipMixer and applied sanctions against Blender and Sinbad, services that have been used in ransomware investigations as well as operations by nation-states.
It mirrors moves elsewhere in the crypto world. As regulated exchanges better-hardened their know-your-customer and real-time screening, high-risk activity moved to mixers, cross-chain bridges and nested services. Ransomware syndicates like LockBit and ALPHV have repeatedly laundered their proceeds through mixers before trying new cash-out routes, public casework and industry reporting show.
Regulatory Background and Market Impact for Crypto Services
Europe is starting to clamp down on crypto money laundering in general. Through the EU’s Transfer of Funds rules, the “travel rule” is being applied to crypto, requiring service providers to send identifying information for both sender and receiver. In collaboration with MiCA and the EU Anti-Money Laundering Authority, regulators are laying down a compliance regime that leaves little space for anonymity-growing services that do not enact this control.
The Cryptomixer takedown should be a call to action for exchanges, brokers and payment firms to ratchet up wallet screening, mixer exposure thresholds and layered transaction investigations. Expect to see additional proactive offboarding for addresses displaying mixer adjacency, and higher intensity of cross-asset hops that profit from an analytics blind spot.
What Comes Next for Investigators and the Crypto Sector
Investigators will work through the seized servers and data for operator identities, infrastructure suppliers, and repeat customers moving big volumes. That can lead to sanctions designations, asset recovery and coordinated arrests by countries’ national cyber units. It can also leak into neighboring bureaus probing ransomware affiliate programs, carding forums and OTC brokers hawking “no-KYC” cash-outs.
Organized crime will evolve, passing more volume through privacy-preserving methods like cross-chain swaps and human-assisted brokers. But the Cryptomixer seizure is a reminder that once law enforcement locks down the back end, the on-chain obfuscation can unravel fast. For the crypto industry, it is another illustration that compliance and forensics are now core infrastructure — and that “anonymity as a service” looks increasingly like a legal liability.

