A Ukrainian national has been sentenced to five years in U.S. federal prison for orchestrating an identity theft enterprise that enabled North Korean nationals to secure jobs at American companies under stolen U.S. identities, with the wages routed to Pyongyang.
Prosecutors said the scheme helped place overseas workers in remote roles across dozens of firms, concealing their true nationality and violating U.S. sanctions as the earnings supported North Korea’s weapons programs. Investigators described the operation as both a sanctions evasion pipeline and a corporate security risk that exposed employers to data theft and extortion.
The defendant, identified by the Justice Department as 29-year-old Oleksandr Didenko of Kyiv, pleaded guilty after his arrest and extradition, admitting to handling hundreds of stolen identities and orchestrating technical infrastructure to make overseas workers appear to be logging in from U.S. soil.
How the identity fraud and access operation worked
According to the Justice Department, Didenko ran an illicit marketplace called Upworksell that let buyers, including North Korean IT workers, purchase or rent U.S. identities to pass employer checks and onboard with American companies. Authorities say he trafficked more than 870 stolen identities, enabling job applications, payroll enrollment, and ongoing access to corporate systems.
The FBI seized the Upworksell website and redirected its traffic to government-controlled infrastructure as part of the takedown. Didenko also recruited people in California, Tennessee, and Virginia to host racks of laptops in their homes, creating “laptop farms” that North Korean workers could remotely control. By tunneling in through U.S.-based hardware, the workers’ logins and network traffic looked domestic, defeating basic geolocation checks.
Prosecutors said the fraudulent workers blended into remote teams, often in software development and technical roles, then diverted their salaries back to North Korea through cutouts. This model stitched together identity theft, infrastructure-as-a-service for evasion, and money movements designed to avoid compliance controls.
A growing DPRK playbook for covert IT employment
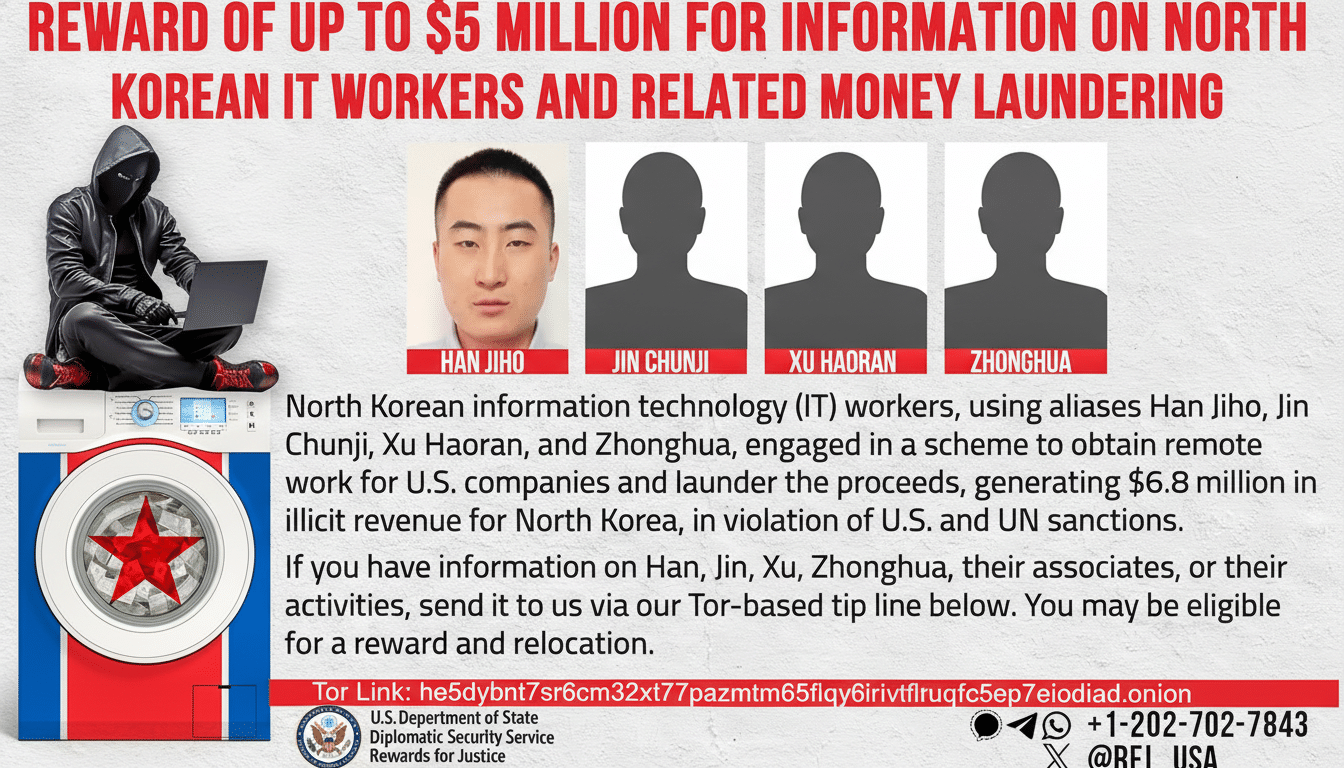
Government agencies have warned that North Korea deploys thousands of IT workers worldwide to generate revenue, evade sanctions, and position operatives inside Western networks. A joint advisory from the FBI, Treasury, and other partners details common tradecraft: borrowed or stolen identities, forged résumés, recruiters-for-hire, and U.S.-based proxy devices to mask location.
Security firms, including CrowdStrike, report a sharp rise in these placements, particularly for remote engineering and DevOps roles. Researchers note a “triple risk” for employers: sanctions exposure, insider access that can enable data theft, and follow-on extortion when sensitive material is exfiltrated.
The identity-workforce playbook complements North Korea’s broader cyber operations. Chainalysis has documented that DPRK-linked crypto theft has topped $1B in some years, underscoring how cyber-enabled revenue streams bolster the regime. The United Nations Panel of Experts has likewise flagged state-directed efforts to covertly deploy workers abroad despite international prohibitions.
What investigators uncovered inside the identity scheme
Case filings describe a turnkey service: identities for onboarding, U.S.-based devices for daily logins, and helpers for receiving mail and equipment tied to the stolen identities. The laptop farms provided a stable “digital home” for the impostors. The Justice Department said the result was sustained access to corporate tools, source code repositories, and internal communications, all while payroll flowed under a victim’s name.
Authorities emphasized that even when impostors performed legitimate work, the employment itself violated sanctions regimes and injected serious security risk. The scheme also victimized U.S. citizens whose personal information was traded, often without their knowledge, to facilitate the employment fraud.
Why it matters for companies hiring remote workers
The case is a wake-up call for employers whose remote hiring surged and whose controls haven’t kept pace. Basic IP geofencing and résumé screening won’t catch sophisticated evasion involving U.S.-based device proxies and well-crafted cover stories. Security teams and HR must coordinate on sanctions screening, identity verification, and continuous authentication.
Experts recommend the following measures:
- Multi-factor identity proofing at onboarding
- Hardware-bound authentication
- Detection of remote desktop tooling
- Velocity checks across logins and devices
- Anomaly monitoring for code repositories and data exfiltration
- Payroll and vendor systems that flag inconsistent banking details and frequent account changes
- Legal teams mapping sanctions obligations and escalation paths when red flags appear
Red flags cited by U.S. agencies include:
- Candidates who refuse video interviews
- Requests to use employer-issued hardware off-site without standard enrollment
- Time-zone and language inconsistencies
- Insistence on third parties managing their accounts
Recruiters and staffing platforms are frequent targets, as are roles that can be performed entirely off-network.
Broader enforcement momentum against DPRK facilitators
The sentence against Didenko adds to a series of actions targeting the facilitators behind North Korea’s covert workforce. The Treasury Department has repeatedly sanctioned intermediaries, front companies, and crypto wallets tied to DPRK revenue generation, while the FBI and Justice Department continue seizing domains and infrastructure used to mask origins.
For policymakers, the case illustrates how identity theft, inexpensive infrastructure, and global remote work can be fused to defeat sanctions at scale. For businesses, it’s a reminder that hiring risk is now a core security domain. The combination of stolen identities and U.S.-based device farms didn’t just fool HR systems—it bought adversaries a seat inside the corporate network.

