Salesforce said it was investigating an incident of unauthorized access to some customers’ data by commercial software that appears to have been enabled by a Gainsight “managed package,” illuminating how third-party connectors can serve as a backdoor into otherwise well-defended platforms in the cloud. The company also said it has found no evidence of a bug on its base platform — insisting activity related to Gainsight’s external workings with Salesforce is the cause.
What Salesforce Has Said So Far About the Gainsight Breach
In a notice to customers, Salesforce said the problem affected “Gainsight-published applications connected to Salesforce that are installed and managed directly by customers.” That’s a big distinction: the access seems to have come through an unauthorized app that worked with Salesforce using OAuth, rather than by hacking into Salesforce infrastructure.
- What Salesforce Has Said So Far About the Gainsight Breach
- Parallels With Previous Supply Chain Intrusions
- How Connected App Attacks Function in Salesforce Environments
- Immediate Actions for Salesforce Customers
- The Wider Risk Inside the SaaS Supply Chain
- What to Watch Next as Salesforce and Gainsight Investigate
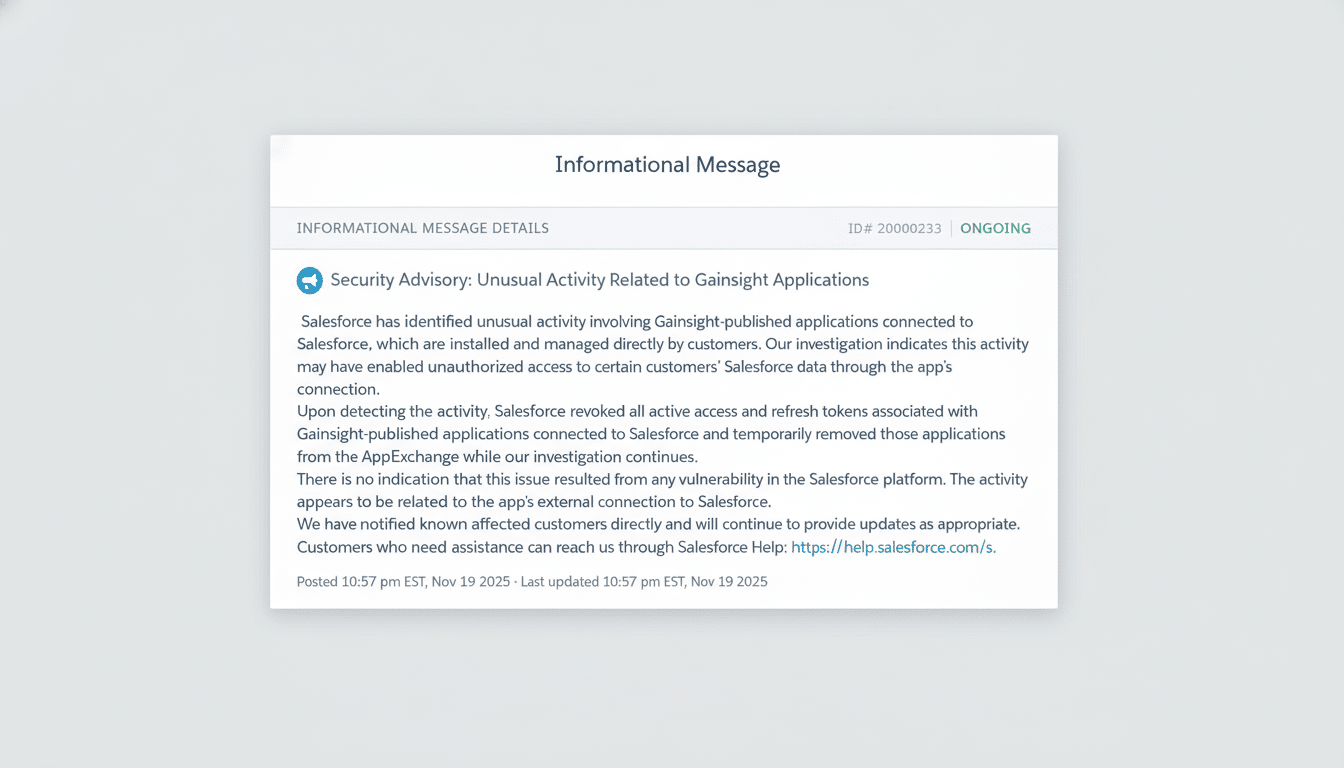
Gainsight, a company that offers customer success software that commonly links to Salesforce records, said on a public status page that it is investigating “a Salesforce connection issue.” It did not initially describe the event as a breach and said its internal inquiry continues.
The hacking group ShinyHunters took credit with the outlet DataBreaches.net and has threatened to advertise stolen data should negotiations fail, a popular double-extortion technique. The group also cited attacks against Salesloft and Gainsight and said it could access data from hundreds of organizations. Salesforce hasn’t verified those claims and the extent isn’t known.
Parallels With Previous Supply Chain Intrusions
This is a déjà vu moment of an earlier event that took place at Salesloft, which is an AI-powered marketing and sales engagement company, where the attackers pivoted from connected-app access to their victims’ Salesforce instances.
That spree also involved victims that were all major enterprises, including Allianz Life, Bugcrowd, Cloudflare, Google, Kering, Proofpoint, Qantas, Stellantis (formerly Fiat Chrysler), TransUnion, and Workday.
A group that called itself Scattered Lapsus$ Hunters, and which shares some members with ShinyHunters, took responsibility at the time and set up an extortion site advertising huge record counts. Gainsight had previously acknowledged it was compromised in the Salesloft-linked activity, but it remains unknown whether the current access is a result of that first intrusion or another compromise.
How Connected App Attacks Function in Salesforce Environments
In the Salesforce world, third-party apps generally connect over OAuth to receive a scoped token for reads/writes on given objects. Customer success platforms, such as Gainsight, frequently ingest account, contact, opportunity, and usage data for health scoring and retention use-case components. With OAuth, if (for example) an attacker pwn’d the vendor environment or token store, those tokens could be exploited to make calls against Salesforce’s APIs and pull information out without ever breaching Salesforce.
This model pools or collapses risk where licenses are wide, tokens are long-lived, or logs are slender. Agencies like CISA have continued to warn about token theft and cloud-to-cloud compromise, yet guidance from CISA emphasizes strict scoping, short-lived tokens, and ongoing monitoring as key countermeasures. Elsewhere in SaaS-land, attackers have stolen secrets, campaign lists, or sensitive metadata from large numbers of online tenants too.
Immediate Actions for Salesforce Customers
- Check inventory of apps from Gainsight and related vendors; verify who has installed them and what scopes they have.
- Invalidate and rotate the OAuth tokens and client secrets of your affected apps; enforce reconsent if necessary.
- Tighten Connected App policies: limit to set IPs, force user re-authentication, and scope down to least privilege.
- Analyze Event Monitoring (EM) logs and API logs for abnormal queries, massive exports, or unfamiliar request patterns; review Connected App OAuth usage reports and Login History.
- Turn off or uninstall unused integrations, limit the scope of data export, and add limits to reduce blast radius.
- Coordinate with Gainsight on indicators of compromise and remediation timelines, and involve legal counsel, insurers, and law enforcement if sensitive data exposure is identified.
The Wider Risk Inside the SaaS Supply Chain
Third-party SaaS connectors are indispensable to go-to-market and customer success teams, but they also represent an increased attack surface. Industry reports such as the Verizon Data Breach Investigations Report and IBM Cost of a Data Breach study have reported partner and supplier compromises as top impact pathways — whereas multi-tenant cloud tools allow attackers to scale across victims rapidly.
At a large scale, the largest issues in Salesforce estates are token sprawl and overbroad permissions. Security leadership is also requiring recertification of connected apps, centralized token vaulting, conditional access policies, and DLP controls in CASB or SSPM tools. The aim here is to make cloud-to-cloud misuse loud, short-lived, and least-privileged.
What to Watch Next as Salesforce and Gainsight Investigate
Some important questions remain: how many Salesforce orgs were accessed without authorization, which data classes were affected, and whether forced token resets are necessary. The real impact will depend on the confirmation of the threat actor, any overlap with past campaigns, and details revealed in Gainsight’s investigation. Customers should monitor advisories from each company, and be prepared to reauthorize integrations after remediation.
For now, the incident is a sobering reminder that even if the SaaS platform core itself remains uncompromised, everything in its trust chain can be the weak link. Hardening that chain is suddenly a priority at the board level.

