State-backed operators tied to North Korea are hacking into Gmail accounts by persuading targets to use rogue, malicious versions of the Find Hub service that Google provides to Android smartphones and tablets. As reported by BleepingComputer and Genians, who make it their business to pay attention to this kind of thing, the campaign uses legitimate recovery mechanisms after first hijacking victims’ credentials using malicious files distributed on the chat platform KakaoTalk.
How the intrusion unfolded and led to account takeovers
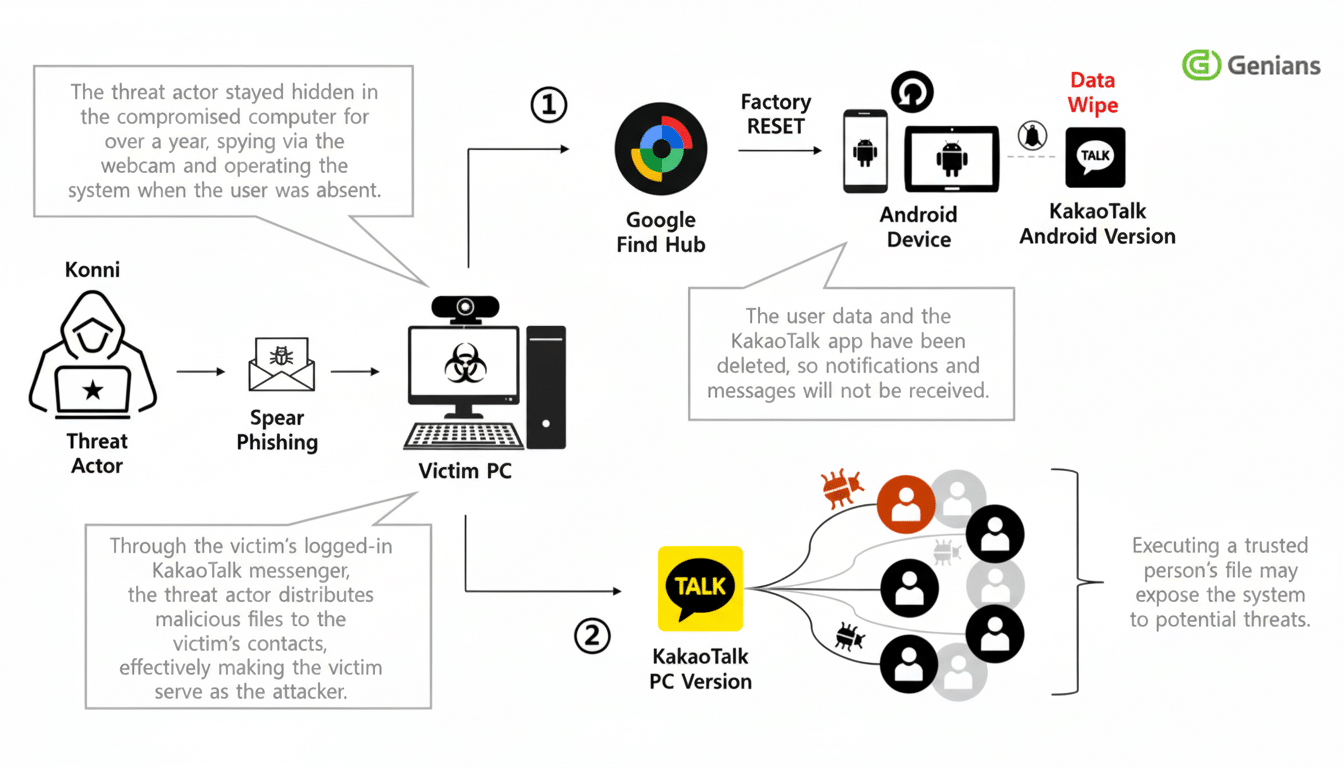
The operation can start with booby-trapped files sent through KakaoTalk, a popular chat app in South Korea, Genians said. After the package is opened, the payload triggers and unpacks scripts that stay silent while implanting itself to observe and steal. The ultimate goal is credential harvesting — namely the victim’s Google account — which gives them effective remote control.
Armed with the Google account, attackers would log in to Find Hub and then check device locations or perform multiple factory resets, in a pattern researchers described as location tracking followed by consecutive wipes, which would destroy local evidence and thwart recovery. In the meantime, the operators are said to have compromised both cameras so that they could exploit them whenever they saw their targets were not using them.
Why plans to weaponize device recovery tools are galling
Find Hub is made to help you find, lock, or wipe your lost devices. None of those features are inherently insecure; account takeover is the culprit. If an attacker can masquerade as you, they are the effective owner. “With all the recent reports,” Google said in a statement to reporters, “there has been no cut on our side that would adversely impact phone speakers.” What we have here is not an underlying product flaw but accounts being broken into farther upstream.
It’s part of a larger trend in tradecraft: adversaries increasingly “live off the land,” using built-in tools and cloud services rather than deploying raucous malware. And it’s effective because it integrates with normal behavior and piggybacks on trusted platforms. We also have industry reporting (annual breach reports, etc.) and they overwhelmingly put stolen credentials at the top of initial access vectors.
Who should be concerned about these Android account attacks
The use of KakaoTalk implies a regional focus, but the technique is portable wherever Android and Google accounts are in use. High-profile targets — journalists, government employees and activists — are among those at high risk, as are people who own cryptocurrency and corporate workers with access to sensitive systems. With Android driving more than 70% of the global market share, the attack surface is tremendous.
It also underscores cross-device risk. By hiding sensitive data in Find Hub, if an attacker takes over your (or another authorized) laptop or second phone, they can still pivot into Find Hub and take control via your primary handset. Security is only as good as the weakest device tethered to your account.
Steps you can take now to protect your Google account
- Change your Google password and turn on two-step verification immediately, opting for security keys or passcodes rather than SMS codes if possible. According to multiple industry studies and Google’s own guidance, accounts with multi-factor authentication are orders of magnitude less likely to be compromised.
- Run Google’s Security Checkup to see recent sign-ins, revoke suspicious sessions, and remove unknown devices. Audit third-party access under “Apps with access to your account” and remove anything you don’t recognize. Verify account recovery options to make sure attackers haven’t inserted their own phone number or email.
- Scan with Play Protect, update to the latest security patches, and uninstall apps you can’t remember downloading from your Android device. Inspect Accessibility and Device Admin permissions for unknown items. If you were sent unexpected files via chat before things went awry, once you’ve logged back in to your Google account from a known clean device, it would probably make sense to wipe and reset the whole device.
- People at high risk should sign up for Google’s Advanced Protection Program, a service that provides stronger security protections and restricts risky account actions. Organizations should couple identity protections with mobile threat defense and conditional access policies in order to limit what a hijacked account can do.
The policy gap and what’s next for device recovery safeguards
Genians advocated for platform-level “step-up” verification for destructive capabilities, such as remote wipe — basically a biometric prompt or PIN after you’ve been signed in. That would mitigate the usefulness of stolen passwords and session cookies, which are a popular target for today’s infostealers. It’s a sensible safeguard that works much like the way many financial apps authorize high-risk transactions.
The lesson is a straightforward but important one: Attackers no longer need novel exploits when they can hijack identities and turn safety features into weapons. Think of your Google account as the keys to your phone, your data, and your location. Lock your keys down, confirm every high-risk action, and operate under the assumption that any tool meant to help you recover a compromised device can be used against you if someone else has them.

