Artificial intelligence is changing the game on both sides of the cybersecurity chessboard: enhancing attack, powering defense; increasing chaos, propelling order.
Microsoft is moving aggressively to populate this new realm with new capabilities in its cloud-native SIEM (and now SOAR) platform titled “Sentinel,” all designed to make security operations more autonomous, more contextual, and empirically faster from the moment of detection to remediation.
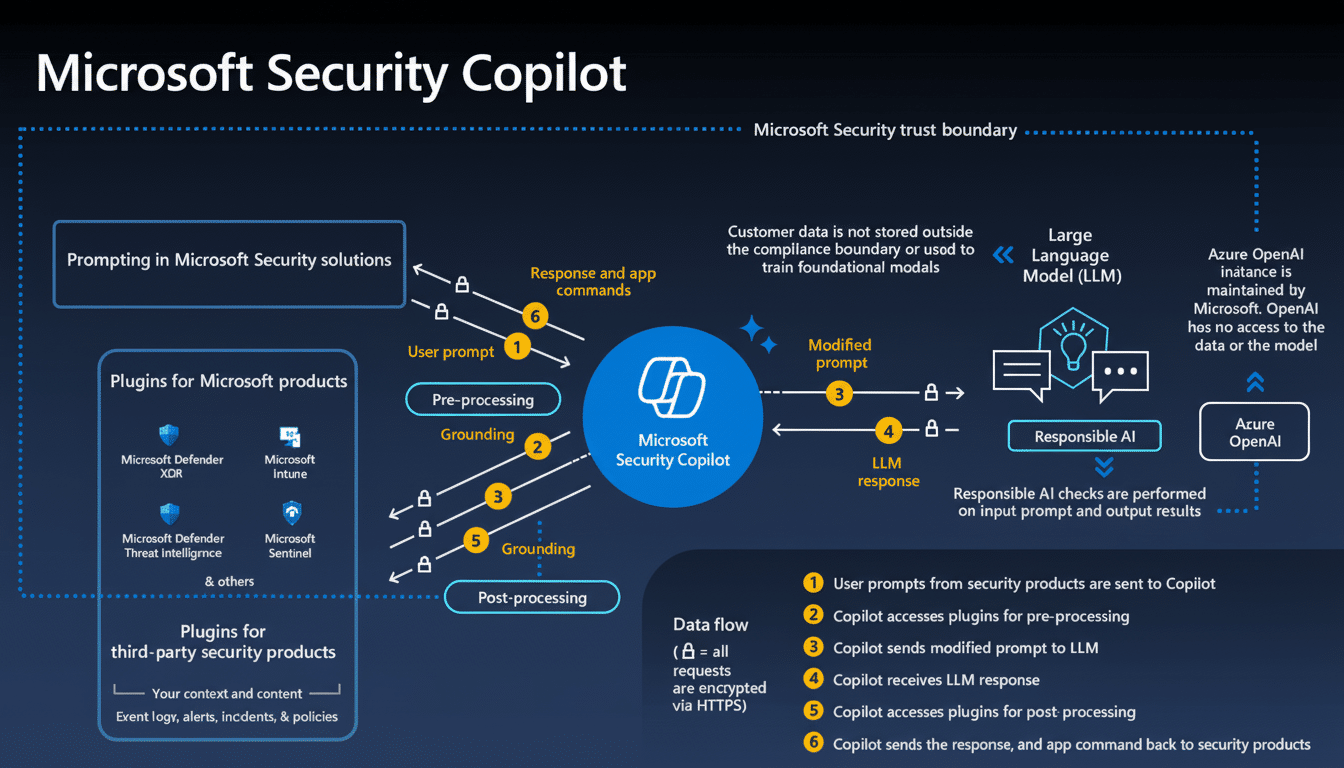
Agentic Response powered by a single security graph
Central to the update is a graph-based view of the enterprise—identities, devices, applications, data, and cloud resources as entities connected by links. Security Copilot agents leverage this context to perform probabilistic reasoning across signals, correlate alerts that seem unrelated in isolation, enrich findings with connections, and prioritize incidents by potential blast radius. Think of it as shifting from alert lists to an evidence graph explaining who did what, where, and why it matters.
In practice, that means a sketchy OAuth consent, abnormal Azure service principal activity, and an odd egress pattern in a storage account can be connected into one story. Sentinel, in turn, offers or takes action—for example, quarantining an endpoint, revoking tokens, or opening tickets—while also keeping analysts involved for approvals and high-impact calls.
Why Context Matters, As Attacks Get Smarter
Attackers are currently automating and using AI to scale credential theft, lateral movement, and social engineering. The recent Data Breach Investigations Report (DBIR) by Verizon suggests that more breaches are linked to “human involvement,” proving how swiftly phishing and identity abuse lead to incidents. Mandiant’s M-Trends research, meanwhile, consistently reports decreased dwell times that provide defenders with an ever-diminishing time to break the attack chain.
A graph-based method mitigates this by modeling intrusion chains before and after a compromise. Sentinel analytics and behavioral models combined with entity relationships surface the meaning of an alert—Is the account high-privilege? Is the device unmanaged? Is sensitive data within reach?—so that teams can parse through the noise and take action on what fundamentally impacts risk to the business.
Extensibility With The Model Context Protocol
Microsoft’s new Sentinel Model Context Protocol (MCP) server is engineered for plug-in agents made in, say, the Visual Studio Code environment, so dev teams can stitch custom tools and workflows into the SOC without duct tape.
MCP standardizes how agents access the context and tools required for safe autonomy: explicit permissions, auditable actions, and human checks when an agent requests large changes.
This is an important issue, because AI security agents are as powerful as they are dangerous. By limiting what an agent can see and do—and by recording all its decisions—SOC commanders enjoy the spoils of speed without giving up control. We also promote harmonization of blue-team playbooks across these discrete stages (some having crossover drama and data), which reduces the “time to automation” for repeated tasks.

The Security Data Lake at the Center of Modern SIEM
The Sentinel security data lake is now generally available, and it centralizes structured and unstructured telemetry from clouds, endpoints, identities, and SaaS applications. For security teams, the benefit is threefold: more cost-effective economics at scale, flexible retention for compliance, and a single substrate for analytics and AI. Kusto Query Language is the grinding wheel from hunting’s grindstone, while UEBA, fusion rules, and threat intelligence enhance the lake with behavioral information.
Importantly, the lake features heterogeneous habitats. Companies can bring in logs from Azure, AWS, and Google Cloud, normalize them, and then run cross-cloud detections using MITRE ATT&CK techniques. It leads to fewer blind spots, richer training data for AI models, and more robust automation across hybrid estates.
From Intelligibility Fatigue To Measurable Results
Security leaders ultimately care about mean time to detect (MTTD), mean time to respond (MTTR), and business impact. By moving fixed triage into agent-driven workflow and basing decisions on an entity graph, Sentinel addresses the two kinkiest bottlenecks to SOC productivity: alert volume and context gathering. In recent years, IBM’s Cost of a Data Breach study has put the average global cost per breach north of four million dollars—each hour not wasted upstream is an hour where we can reduce that downstream risk.
Picture this: A midsize bank is bombarded with lookalike phishing domains. Sentinel correlates brand impersonation signals, mail-flow anomalies, and endpoint detections and then automates domain takedown requests as well as account resets, providing analysts with a unified case for validation. What once took hours over a number of tools is now condensed to minutes through consistent, auditable steps.
Ecosystem Signals and the Way Forward in Security
The industry is becoming increasingly settled around more rigorous evaluations of AI-powered defenses. The push by large tech companies to establish baselines for automatic security agents indicates an obvious requirement for standards and safety levels. Frameworks like MITRE ATT&CK, and the nascent MITRE ATLAS for AI systems, provide teams with a lingua franca to test detections and red-team agent behaviors.
What to watch next:
- Tighter guardrails on the actions of agents
- Clearer provenance for decisions made by models
- More deeply integrated developer workflows and SOC pipelines
So long as Microsoft persists in coupling graph-native context with open extensibility and disciplined human-in-the-loop design, Sentinel will continue to serve as a bellwether for how AI transforms security operations in the wild—not just in demos.

