Google has released the Android Security Bulletin for this month, and it’s a big one. The company notes a lengthy string of platform and vendor vulnerabilities, with several rated Critical that could potentially cause devices to malfunction or increase an attacker’s privileges. Updates are being pushed through normal over-the-air security patches from device manufacturers.
What Google disclosed in the December security bulletin
The bulletin lists vulnerabilities in the Android framework, system layer, and kernel, as well as component-specific bugs affecting chipsets from Qualcomm, MediaTek, and Unisoc.
The most severe item is a framework issue that, in the worst case, can allow a remote denial-of-service attack, potentially taking down a device without privileges. Elevation-of-privilege vectors make it possible for app-sandboxed malware to break out or otherwise gain even more control by exploiting system- and kernel-level bugs.
Entries are once again kind of sorted in the order they were released based on CVSS guidance; there is a meaningful number of “High” and “Critical” entries this cycle. Most of these flaws are easy to exploit and cannot be resolved with a simple update, but require the entire operating system to be updated. In addition to Google’s own disclosures, patches are contributed by silicon vendors (variously referred to as “silicon partners”) and the larger Android open-source community.
Who is affected and when fixes roll out to devices
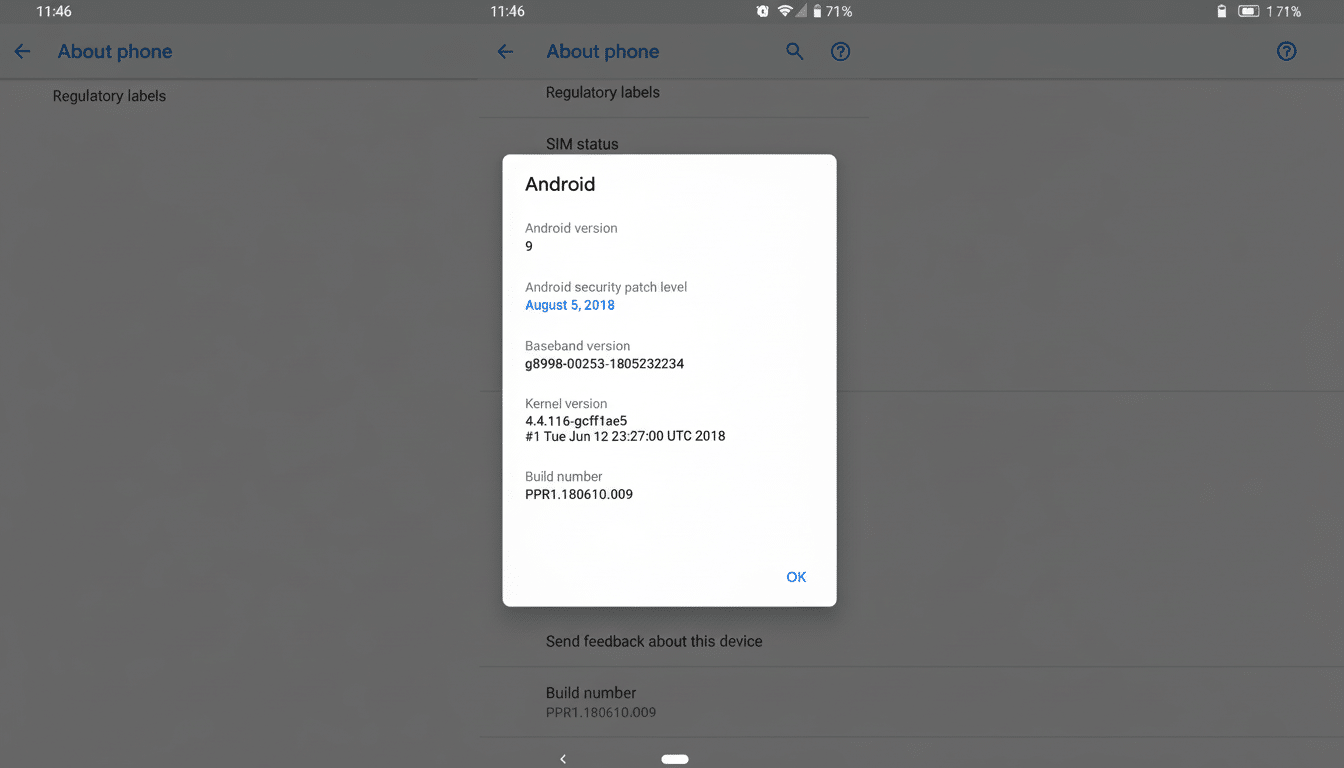
Google says these problems impact devices running Android 13 and later. Remediation is available through the manufacturer’s security update, which sets the Android security patch level on the device. Pixel phones usually get patches first, with other brands rolling them out based on model and region. To check protection, go to Settings and search for “Android security update,” and see if your device has the latest patch level installed after you’ve downloaded it to your phone and restarted.
Organizations that apply fleet management in their MDM or EMM are encouraged to enforce the handling of such non-compliant devices based on current security patch level and then gradually roll out compliance based on the updated security patch levels. As some of the vulnerabilities addressed by patches can be kernel- or driver-based, delaying deployment equals a larger area for attack to remain open, as with app-layer threats.
Why the list feels longer this month for Android
This cycle’s bulletin is much larger than those of late, a characteristic that often comes with wrapping up platform disclosures in a wider cadence and silicon partners contributing batches of fixes. Google has also updated the distinct Security Bulletins for Android Automotive and Wear OS; updates to those tracks were included but no new vulnerabilities have been added this time.
What you can do to protect yourself on Android
Upgrade your system to the latest version and reboot. Keep Google Play system updates up to date as well; they can’t take the place of full OS fixes for kernel and driver vulnerabilities, but they do harden critical modules through Project Mainline. Also enable Google Play Protect, avoid sideloading from “untrusted sources,” and ensure that always-critical apps like browsers or messaging clients are kept updated—applications in which there is a chance for vulnerabilities to be exploited.
Also, if your device is no longer getting security patches, weigh the risk carefully. There are a few mitigations available—you can use a modern browser that has site isolation enabled, and restrict app permissions—however, these do not serve as replacements for OS-level patches. Users at high risk, or users in a business-critical role, should be considering moving to an updated product with an active support status.
The bigger security picture for Android users today
The Android threat landscape is predominantly focused on elevation-of-privilege and vendor driver bugs, a pattern seen in years of statistics tracked by the National Vulnerability Database and MITRE’s CVE program. That said, this being Android and freshly disclosed platform vulnerabilities, it’s not as if weaponizing software flaws is unprecedented (we need only remember how the Stagefright era redefined patch cadences across the ecosystem). The best defense is regular updates.
Bottom line: be sure to check for the new Android security update today. If you can download it for your phone, do so as soon as possible to close the latest set of holes in the framework, system, kernel, and common chipset components.

