Google is introducing a “social” backdoor recovery measure, called Recovery Contacts in early testing today, allowing you to designate friends or family who can help you regain access to your Google account if you’re ever locked out. It’s a pragmatic response to an increasing problem: account takeovers and lockouts that traditional methods — backup emails, phone numbers or security questions — don’t always fix immediately.
How Recovery Contacts Work to Restore Your Google Access
The feature resides in the Security area of your Google Account settings. You can add up to 10 trusted people who need to agree to your request for them to be listed as a recovery contact. Critically, they don’t have any access to your account or data — only the power to help with verification when you want to get back in.
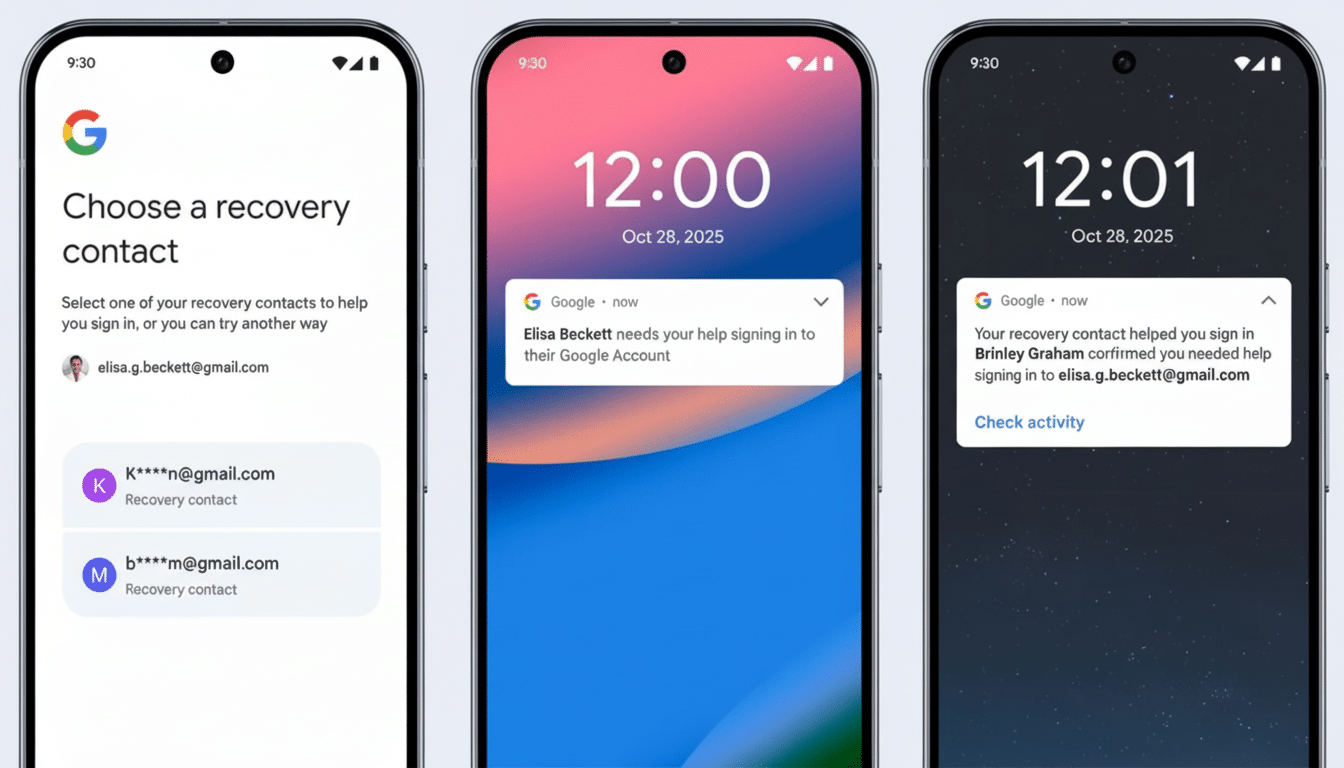
When you’re locked out — when you lose a device, forget a password, or can’t receive verification codes — you can turn to one of your recovery contacts during the sign-in flow. Google then sends that individual a brief verification number, good for 15 minutes. You tell Google the number and boom, you’re you, and thus allowed in. To mitigate abuse and reliance on any specific contact, a one-week cooldown period prevents you from using the same person twice.
This design ensures the scope of the helper remains intentionally limited. By not clicking through dangerous links or sharing personal info, they confirm who you are by sending you a code when you request it. That’s a pretty simple, human-in-the-loop safety layer in addition to (and atop) the standard automated checks.
Setup Tips and Good Practices for Safer Account Recovery
Presumably you also want more than one person to call on when someone doesn’t respond, so select people who can be reached, who are tech-savvy enough to avoid scams, and who would accept an occasional security request.
- Explain what to expect: this is a brief numeric code that you can request directly, and your friend should never provide it to anyone claiming to be “Google support.”
- Keep it up to date — drop people when they change phone numbers, and add them when you strike up new relationships.
For better recoveries, combine Recovery Contacts with strong primary protections: passkeys or password plus two-step verification, current phone numbers, and multiple on-device PIN/sign-in methods.
If you depend on your phone for codes, have a backup authenticator (either a security key or an authenticator app) so if you lose one device it doesn’t leave you in the lurch.
Google is also updating sign-in with a mobile number as recovery, which can find accounts connected to your number and allow you to confirm using that previous device’s screen lock. That dovetails with Recovery Contacts by providing a last-resort fallback when email — or even access to a current device — isn’t accessible.

Security and Privacy Considerations for Social Recovery
There is no social recovery without safe people. To reduce the risk of impersonation or pressure, when in doubt, establish a verification dance with your contacts — for example, before you’re even exchanging any code confirm you are speaking to each other via a recognized voice call. The 15-minute code window, the seven-day reuse limit, contact opt-in — all of these are smart friction that shrink the attack surface.
The larger context shows why these rails are important. The fact is that in Verizon’s Data Breach Investigations Report, year after year, the human vector is commonly cited as a source of breaches and leaked credentials often play a significant role in web app compromises. The FBI’s Internet Crime Complaint Center has said it receives billions of dollars in losses from online fraud each year, with phishing as the top-reported category. Recovery trajectories need to be resistant to social engineering while not so stiff that it bins legitimate users.
Crucially, Recovery Contacts do not leak your emails, photos or files. They merely enable a time-stamped phase of verification. That division of responsibility — humans aid decisions about identity, systems manage reauthentication — is consistent with the advice from standards bodies like NIST: that at account recovery time you want multiple layers of context-awareness rather than simple-to-guess questions or just using SMS.
How This Compares to Rivals, and Why It Matters Now
Apple rolled out Account Recovery Contacts in iOS years ago, and consumer security advocates have generally applauded the concept when it is opt-in, explicit, and not applied too broadly. Facebook had a similar concept called Trusted Contacts, but the company retired it, reflecting the tightrope platforms walk between making tools accessible and preventing misuse of them.
Google’s version combines the strongest elements of social recovery — you get friends and associates to vouch for you — but limits exposure through short-lived codes and contact approval. It is a counterpart to other momentum in consumer security: Google has reported that auto-enrolling users into two-step verification materially decreased account takeovers for those users, and passkeys remain a design feature that cuts phishing risk.
For everyone else, the takeaway is simple: establish your Recovery Contacts now rather than later. For families, pick at least two people who don’t live together. For creators and small-business people, make your lists of contacts diverse and keep a way to find emergency procedures off the cloud. Recoverability isn’t sexy, but when something goes wrong, it’s the difference between a blip and days of problems.

