Security researchers are warning that hundreds of companies running Cisco’s email security device may be vulnerable to an actively exploited vulnerability that has been linked to a Chinese state-sponsored hacking campaign, which evidence shows is targeting exposed systems. The campaign exploits a recently discovered zero‑day that is being tracked as CVE‑2025-20393 and impacting Cisco Secure Email Gateway and Secure Email and Web Manager appliances.
Cisco verifies in-the-wild exploitation and has attributed the activity to China‑nexus operators via its Talos threat intelligence group. Though the company has not specified the number of victims, independent internet‑scanning groups report that the exposed attack surface is large enough to imperil hundreds of customers — even if current activity continues to appear selective.
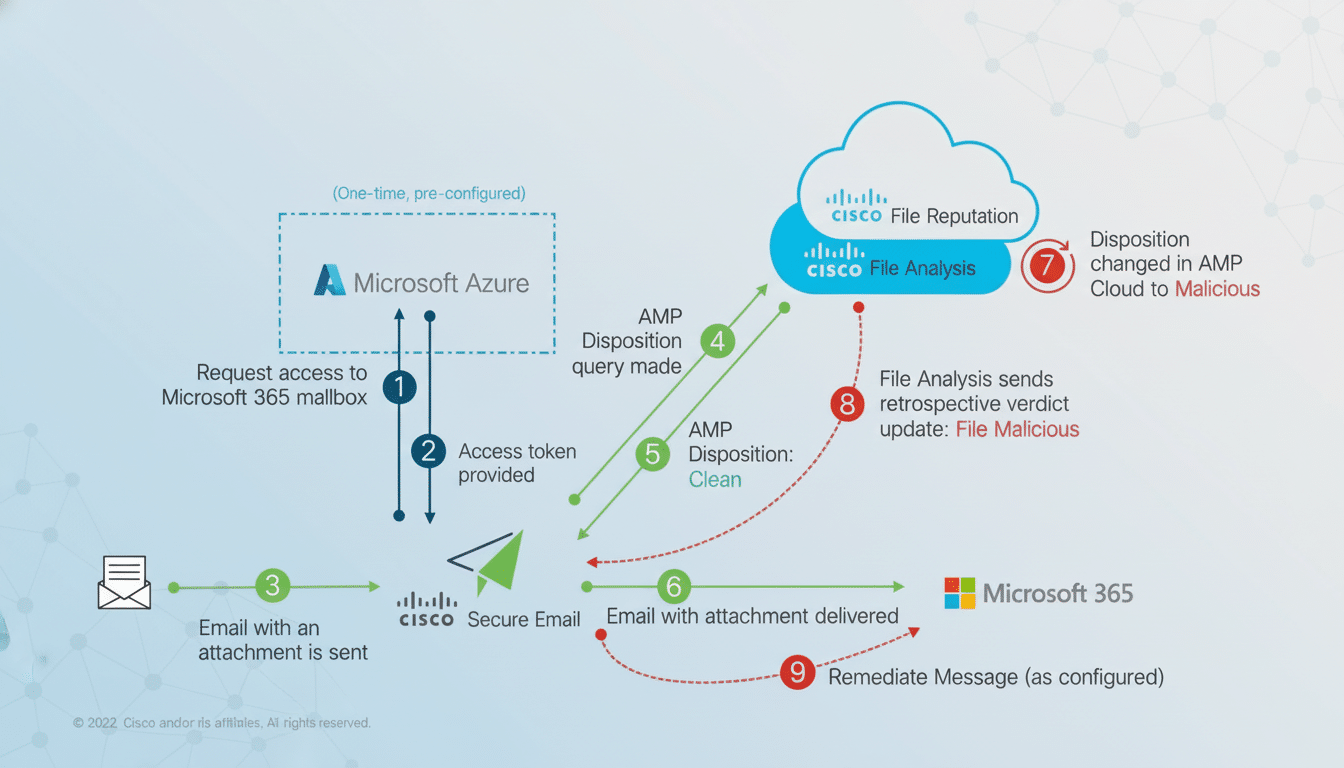
Targeted Exploitation of a New Cisco Zero‑Day
The vulnerability allows attackers to gain unauthorized control of vulnerable systems under certain conditions. According to Cisco’s warning, systems are only vulnerable if they are accessible from the internet and the “spam quarantine” feature is activated — neither setting is enabled by default. This may explain why exploitation seems targeted rather than random.
Shadowserver, which monitors global exposure, is mapping out the population of internet-facing devices at risk from CVE‑2025-20393 and reports active exposure in a range of locations including significant hotspots in India, Thailand, and the US. One of the products, email gateways by Cisco, was found being used in 220 internet‑exposed devices on public networks, according to Censys, a company that maps out services on the public internet — an indication of how far these machines are from attackers looking to test them.
These tallies represent only the hosts that were visible on the open internet at the time, researchers stress. A number of organizations run hybrid deployments or can be served by a managed service provider, so the actual number of at‑risk organizations could be greater than what scanning alone uncovers.
What Makes Email Security Appliances So Attractive
Email gateways are a strategic choke point that hackers can use to intercept messages, collect credentials, and pivot deeper into the network. Unlike endpoints, security appliances do not always receive full endpoint detection coverage and often are deprioritized in patch pipelines, which makes them interesting targets for advanced persistent threat actors.
China-aligned groups have hit perimeter and messaging infrastructure time after time; a trend that has been observed in previous intrusions into email security and VPN products from multiple vendors. The playbook is always the same: leverage a new or recently discovered vulnerability, gain discreet persistence into the appliance, and exfiltrate data or credential holders over time.
Who Is Most at Risk Right Now from This Campaign
For example, organizations with the Cisco Secure Email Gateway or Secure Email and Web Manager using the spam quarantine feature available through a public internet connection are most at risk. The most common adopters are corporations, government organizations, universities, and ISPs that send a lot of mail using these systems as delivery services.
The geographic distribution is underscored by Shadowserver’s telemetry, which reveals dozens of exposed systems in critical countries. A small number of insecure gateways may even represent downstream risk disproportionately, as a single breached device can net attackers with wide visibility and privileged access to your mail flow across an entire organization.
No Patch Is Available: What Defenders Can Do
Cisco has not issued patches for CVE‑2025-20393 yet. The company’s advice is unusually direct: if you believe or know that your device has been compromised, wipe it and restore to the state that you’re confident works. Talos cautions that at this time, rebuilding is the only certain means of eradicating the threat actor’s persistence mechanisms.
In the meantime, defenders should not delay hardening:
- Block internet‑accessible traffic for the affected products if possible.
- Disable the spam quarantine feature.
- Enforce IP allowlists and strong authentication on management interfaces.
- Increase monitoring to include alerting on suspicious behavior.
- Baseline outbound traffic from these appliances and observe anomalous connections as potential signs of data exfiltration.
Security leads also need to check the Cisco advisory and Talos analysis for detection recommendations and indicators, work with email and SOC teams to search for any suspicious quarantine activity or admin changes that should not have been made, and verify a clean backup before executing a rebuild of any systems.
Potential impact and what’s next for defenders
The behavioral effects of a successful intrusion can be dramatic: maildir takeover via credential harvesting, tampering with the routing of emails, installing new implants, and laterally spreading toward domain controllers or identity providers. These devices are used to process sensitive communications, so even just partial access can be a source of valuable intelligence for espionage‑minded threat actors.
Anticipate further reconnaissance against vulnerable Cisco gateways as attackers look for high‑payoff targets while patches are not yet available. Those that can quickly minimize their internet footprint and validate quarantine features will vastly decrease the attack base. Consider placing these appliances behind a reverse proxy or VPN, and move quarantine functionality off internet‑reachable interfaces until patches are available.
This campaign is a clear indication that “security of the security stack” is now a board‑level concern. Inventory your edge appliances, reduce endpoints that are internet exposed, and scope email security infrastructure as aggressively as you do identity and network perimeter systems. As the situation progresses, you may want to monitor resources from Cisco, Talos, Shadowserver, Censys, and government partners like CISA, who may release additional mitigations or detection signatures.

