Apple quietly pushes a major security upgrade that is aimed right at the bread-and-butter tactics used by commercial spyware crews. Dubbed Memory Integrity Enforcement, or MIE, the new feature resides on the iPhone’s hardware and software stack and is designed to block memory corruption bugs that many zero-click iPhone hacks and forensic tools rely on.
What MIE actually does
MIE makes the iPhone memory handling more secure by secretly tagging each allocated chunk of memory. Later, only code bearing the right tag can touch that memory. If a tag does not match — for instance, because an exploit is trying to do a buffer overflow or a use-after-free, the system denies access and crashes the offending process while recording a debugging trail.
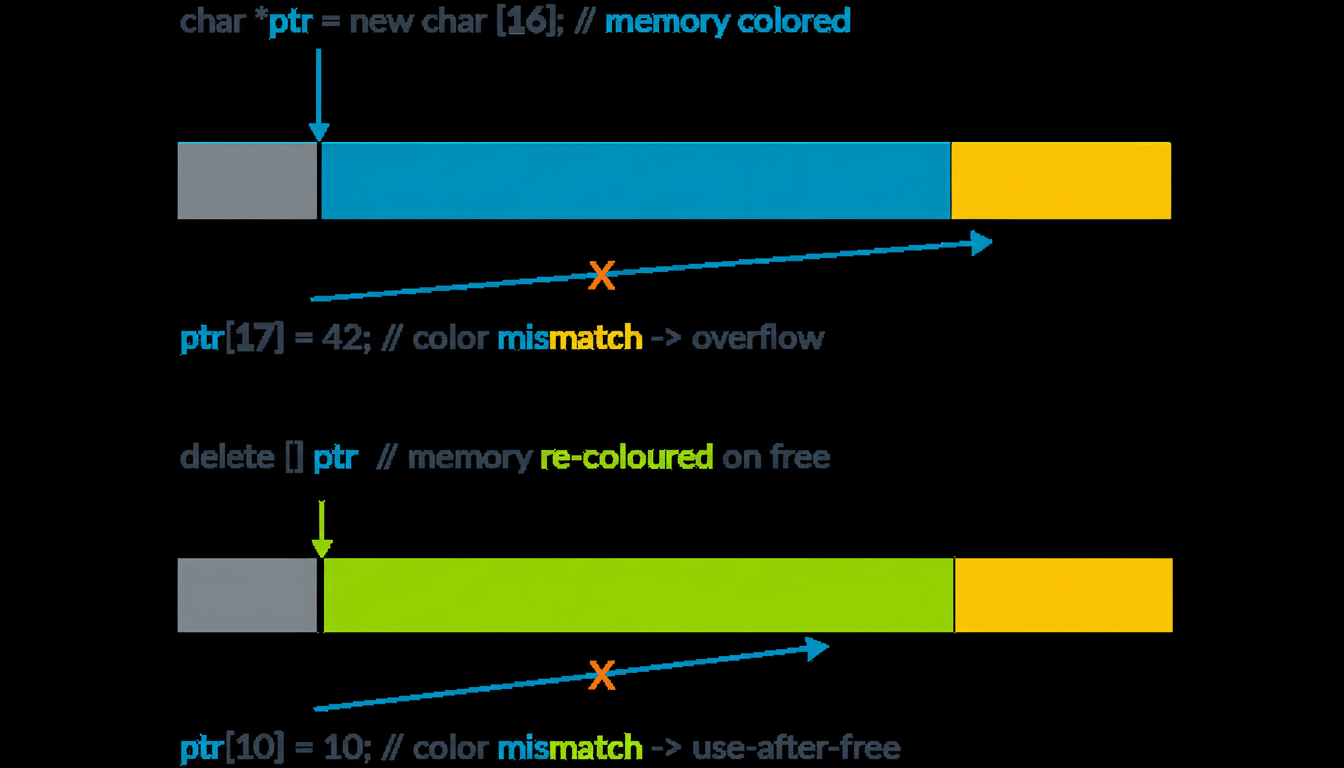
In practice, what this means is that classic forms of memory corruption—buffer overflows and type confusions and other temporal or spatial bugs—are much more difficult to weaponize reliably. The feature narrows the attack surface from which many of these exploit chains start, particularly those that rely on precision reads/writes to do their damage.
Built on Arm tagging, pushed even further by Apple
Under the hood, MIE leverages Arm’s Memory Tagging Extension, a hardware-assisted protection that fingerprints memory regions. This has been developed over years in collaboration with Arm to become Enhanced MTE (EMTE), and this is now wired end-to-end into iOS and Apple silicon, according to Apple. That vertical control — chip design, kernel and app frameworks — allows Apple to institute the protections widely and with performance tuning that’s hard for fragmented platforms to replicate.
Android devices including Google’s Pixel, and security-focused distributions like GrapheneOS, also have MTE support. But some offensive security experts say Apple’s integrated strategy might make the newest iPhones among the hardest mainstream phones to exploit for memory corruption alone.
Why this squeezes spyware makers
Mercenary spyware often relies on chains of memory bugs to gain access to messaging apps and browsers without the need for interaction from a target. Citizen Lab has documented a number of zero-click attacks against iMessage and Safari employed by commercial vendors, and memory corruption is at the core of those intrusions. Microsoft has recently claimed that about 70% of the security vulnerabilities it fixed over time were due to memory safety issues, and Google’s Project Zero said more than once that most vulnerabilities observed in the wild are based on those very bug classes.
Enabling MIE at the system, even if only in a limited number of CVEs, makes reliable exploitation significantly more expensive. A few working iOS exploit chains will suddenly cease to work on the latest models. Researchers who work on iOS, like Jiska Classen of Hasso Plattner Institute, believe some vendors could be left without a reliable iPhone entry point while they rework their products.
Crashes become clues for defenders
And there is another sting in the tail: observability. MIE’s tag checks aren’t just about preventing malformed memory access — they cause things to crash and fail loudly. This means clandestine exploitation attempts are more likely to leave a breadcrumb trail. Such artifacts can expedite incident response, helping assign the origin of attacks — raising risk and expense for operators that deploy zero-days, according to security teams including those at firms such as iVerify.
Default protections, with room to build
(MIE is turned on by default for core system components, which includes high-value targets such as Safari and iMessage — the same apps often targeted in zero-click entry attacks.) Apple is also delivering EMTE tooling so third-party developers can implement memory tagging in their own apps. The more developers that choose to participate, the fewer haven of exploitation remain.
For people at higher risk, from journalists and human rights defenders to executives and political staff, upgrading to the latest iPhone hardware substantially reduces that exposure. Combing MIE with things like Lockdown Mode, regular updates, and strong account hygiene is an added bonus.
Not hack-proof, but the economics change
No platform is immune. Adversaries can shift tactics to logic flaws, baseband components, supply chain vulnerabilities or social engineering. But by degrading the most durable exploit primitives, MIE compels adversaries to invest more in research, consume more vulnerabilities and bear more operational risk. But as macOS security expert Patrick Wardle has noted before, the optimal course of action for high-risk users is to use the latest hardware, not only because it pushes attackers into more expensive and esoteric techniques but also because iOS zero-click attacks are a limited pool that could soon become too shallow.
And the industry takeaway is that memory tagging at scale is no longer an experiment. With Apple insisting it on its newest iPhones, spyware makers now have a tougher mountain to climb, fewer quiet victories and a better odds of being caught in the act.

