Digital sovereignty has shifted from policy talking point to boardroom mandate, and a major open-source vendor just put numbers to it. Red Hat has released an open, self-service Digital Sovereignty Readiness Assessment that helps governments and enterprises quantify how much control they truly wield over data, infrastructure, and operations—at a moment when cross-border cloud risk and regulatory pressure are intensifying.
Why Sovereignty Is Now A Board Priority
The governance stakes have risen sharply since the Schrems II ruling invalidated the EU–US Privacy Shield, forcing organizations to reassess data transfers and vendor exposure. Regulators have turned up the heat: multiple European data protection authorities, including France’s CNIL, have challenged the use of certain US analytics and collaboration tools when safeguards fall short. Meanwhile, the EU’s Data Act, NIS2, and ongoing work on ENISA’s EUCS cloud scheme are reshaping compliance baselines across sectors.
In practice, this means procurement teams are scrutinizing where data lives, who holds encryption keys, and how quickly operations can decouple from overseas control in a crisis. Several ministries and public bodies in Europe have already moved toward domestic or open-source alternatives for messaging, file sharing, and video conferencing. The trend is not isolationism—it’s risk management.
Inside Red Hat’s Assessment for Digital Sovereignty
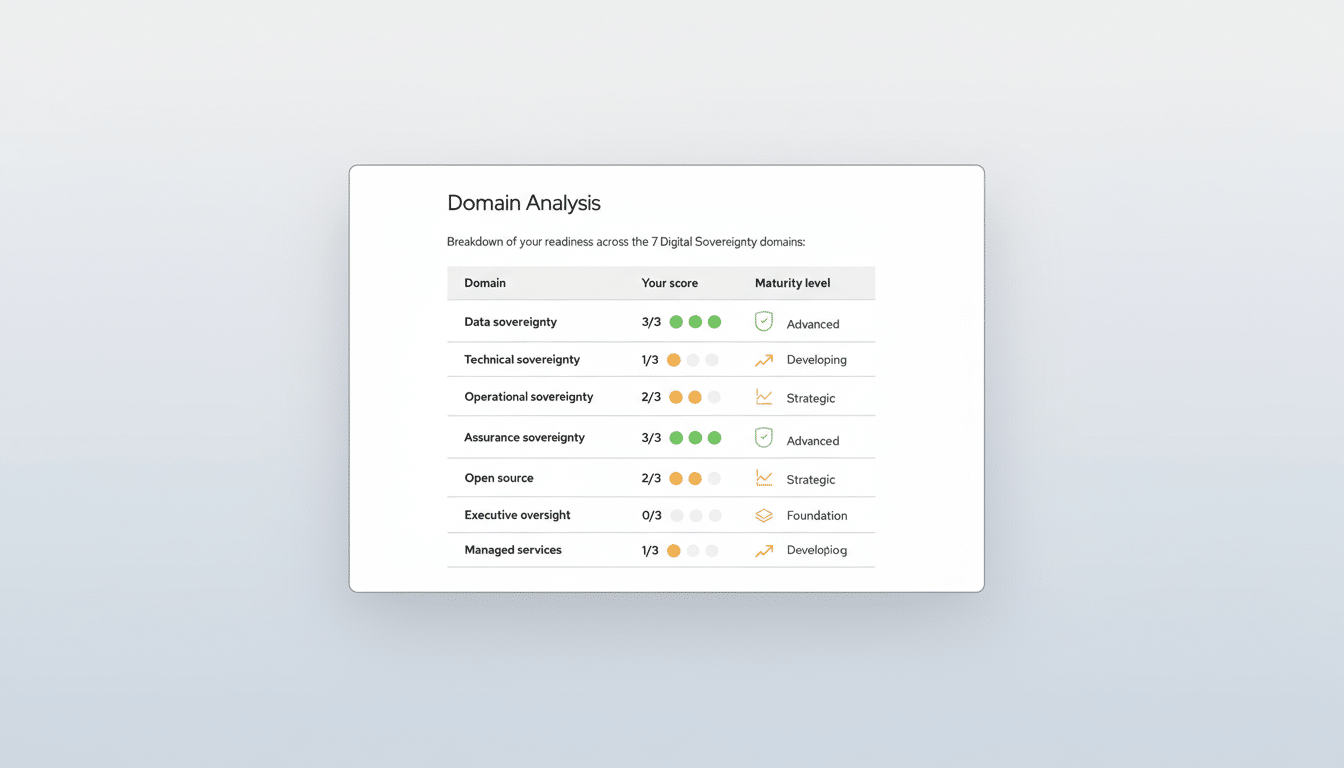
The new web-based assessment is a guided, 21-question survey that takes about 10–15 minutes if stakeholders have facts at hand. It probes concrete controls: data residency and classification, cross-border transfer prevention, customer-held key management, disaster recovery planning for geopolitical events, and how managed services align with sovereignty requirements.
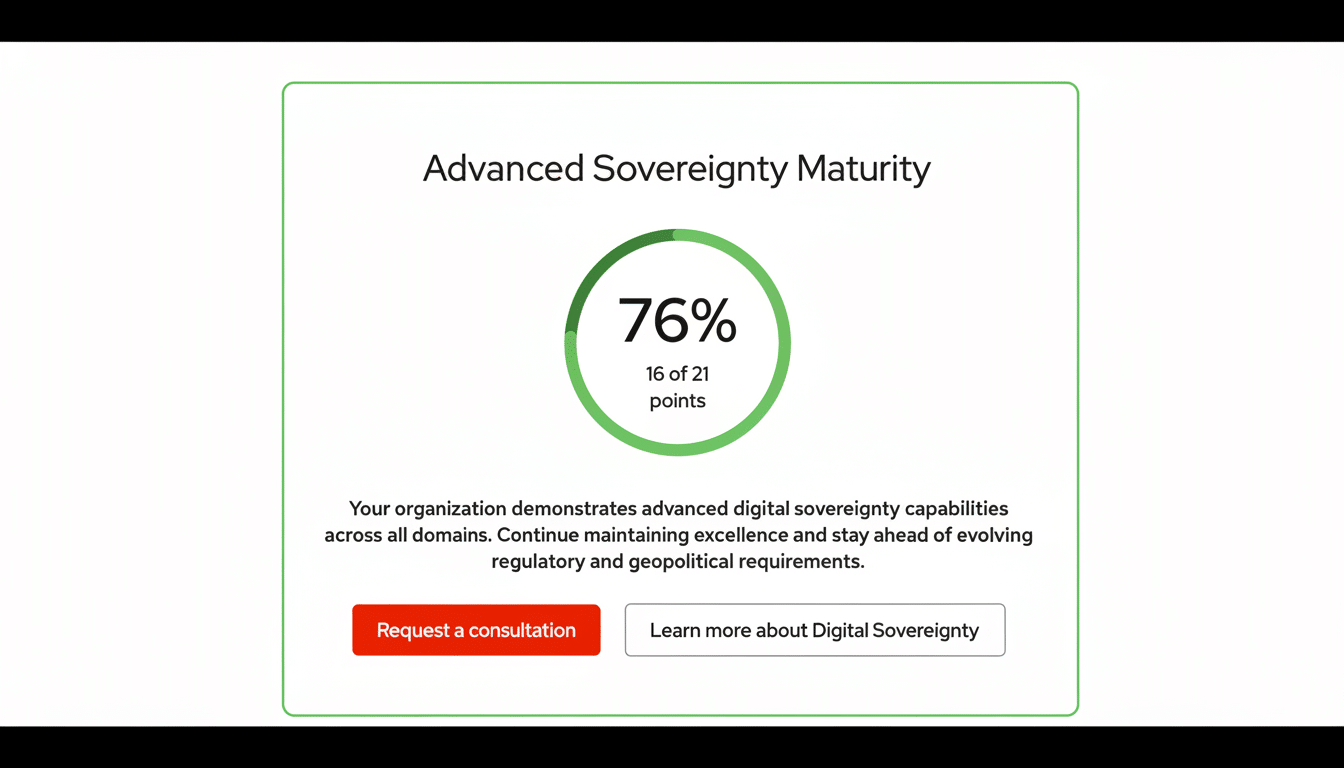
Results are mapped across seven domains—data, technical, operational, assurance, open-source strategy, executive oversight, and managed services—and scored against four maturity stages: foundation, developing, strategic, and advanced. The output includes a tailored roadmap, highlighting immediate gaps and longer-term investments, so CIOs, CISOs, and DPOs can align remediation with budgets and audits.
The assessment complements Red Hat’s EU-focused Confirmed Sovereign Support program, which aims to ensure critical operations remain under EU jurisdiction. But the scoring framework itself is intentionally vendor-neutral, designed to benchmark any stack or provider mix.
Open Criteria and Local-Only Data Protection Approach
In a field often dominated by proprietary checklists, Red Hat has published the tool’s criteria and code under the Apache 2.0 license. That transparency lets governments, partners, and even competitors audit the logic, extend it to national schemes such as France’s SecNumCloud or Germany’s C5, or fork it to reflect sector-specific obligations in finance, health, and critical infrastructure.
Privacy posture matters as much as scoring. Assessment responses stay in the browser and are not transmitted to Red Hat or third parties. Organizations can also self-host the code. As Hans Roth, who leads the company’s EMEA business, has argued, sovereignty claims should be verifiable—moving the industry away from marketing assurances toward testable controls.
How IT Leaders Can Put It To Work Across Teams
For many teams, the first run will surface familiar tensions: cloud agility versus residency mandates, managed services convenience versus customer-controlled keys, or federated operations versus centralized auditability. The assessment provides a common language for legal, security, and procurement to prioritize fixes—such as migrating to customer-managed HSMs, enforcing regional failover patterns, standardizing Kubernetes policies, and tightening data classification tied to export controls.
It also helps evaluate “sovereign cloud” offers from hyperscalers. Major providers now market EU constructs with local support boundaries and key management options. A measurable baseline lets buyers test those claims against their own thresholds and regional certifications, rather than relying on generic promises.
Context From the Field: European Cloud Governance
European authorities continue to nudge organizations toward transparency and control. National guidance from data protection regulators has scrutinized telemetry-heavy apps, and several public bodies have moved to state-run or open-source services for sensitive collaboration. Industry groups behind initiatives like Gaia-X have kept the conversation focused on interoperability and portability to avoid lock-in while meeting local rules.
Enterprise cloud use keeps climbing across the region, according to Eurostat, which makes repeatable governance even more urgent. The organizations that fare best are those treating sovereignty as a living maturity model rather than a binary goal—tracking practical indicators such as the share of workloads with customer-managed encryption, the proportion of data stores with enforced residency, and the number of critical services with exit plans tested in real drills.
What To Watch Next For Digital Sovereignty Efforts
The assessment is not a certification; auditors and regulators will still expect evidence mapped to laws and standards. But an open, testable model is a useful compass. Start with a cross-functional run-through, validate assumptions with security and legal, then rerun quarterly as projects land. In parallel, align vendor roadmaps—whether hyperscaler, regional provider, or on-prem platforms—with the gaps the tool reveals.
The bottom line: sovereignty is no longer an abstract value; it’s an operational discipline. By making the criteria public and the data private, this assessment gives leaders a pragmatic way to measure, improve, and defend their strategy when the next audit, RFP, or geopolitical shock arrives.

