Nine security startups were highlighted at Disrupt Startup Battlefield, which shows where enterprise security is heading as AI‑fueled attacks emerge, deepfakes and sprawling cloud estates alter risk entirely.
The lineup combines autonomous testing, AI model guardrails, ransomware recovery and real-time content integrity, signaling a wave of tools constructed for the modern SOC workflow.
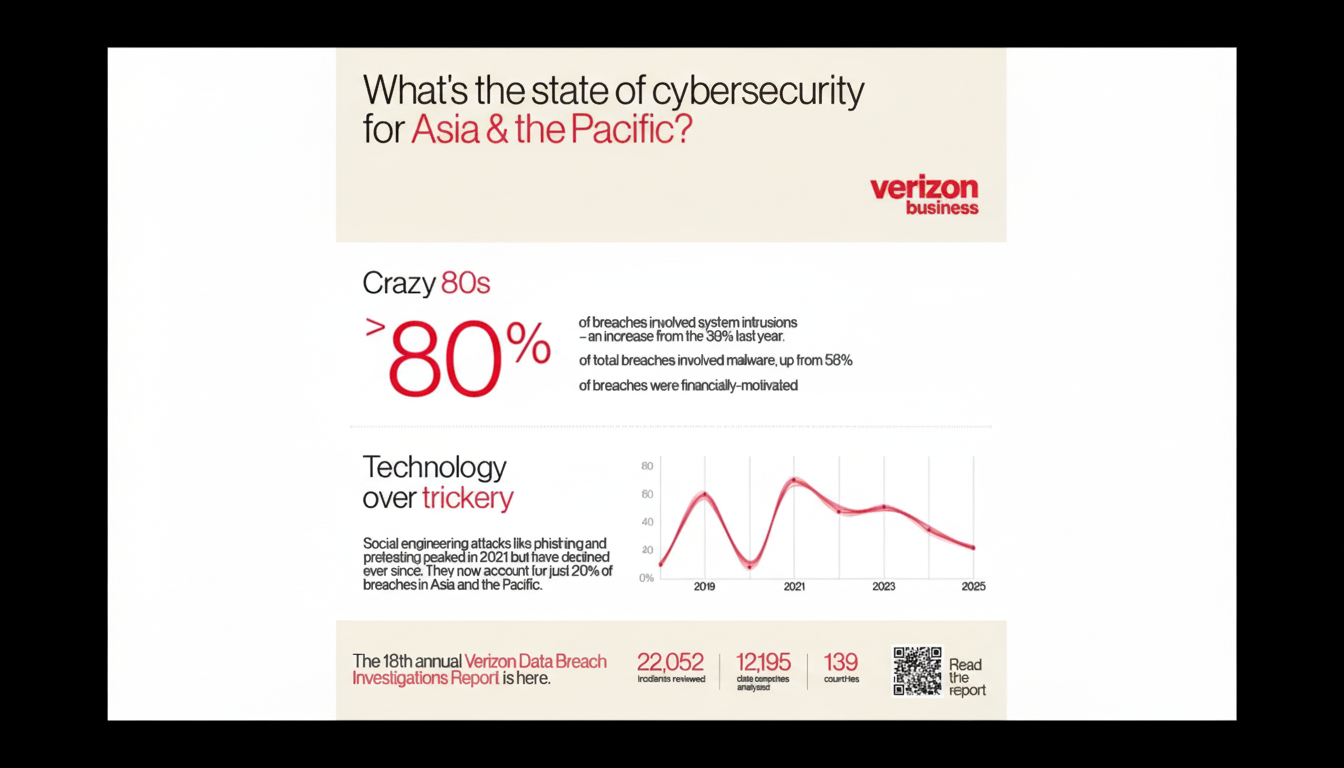
The timing coincides with a growing urgency among security leaders. (Specifically, Gartner puts global information security spending beyond $215 billion last year, and the most recent Verizon Data Breach Investigations Report ties some 74 percent of breaches to human error, from late or improper security configurations to misdelivered emails.) (Check out IBM’s Cost of a Data Breach study, which put the worldwide average at around $4.88 million, demonstrating why “quick remediation” and “resilient recovery” are no longer nice-to-haves.)
Here are nine to watch, and what their eruption says about the next stage of cybersecurity.
AI security takes center stage on the Battlefield
Attackers are already using generative AI for realistic phishing, fast expertise building and social engineering. Backlash: The standout startups there are focusing on AI red teaming, model guardrails, small language models optimized for security purposes and identifying “shadow AI” within enterprises. Anticipate these approaches to align with the NIST AI Risk Management Framework and further clamp down on policy guidance we are seeing globally (for example, around model provenance and content authenticity requirements).
Nine cybersecurity startups to watch right now
- AIM: Sits in the middle between offensive and defensive AI. The platform leverages AI-powered red teaming to model LLM-aware attack paths and applies custom guardrails to company AI apps that limit prompt injection, data leakage and jailbreak risk. Teams with pilot generative AI solutions can also leverage AIM’s safety-planning tooling to drive from policy to technical controls.
- Corgea: Specializes in secure-by-default coding and AI agents that scan and automatically remediate flaws across popular languages and frameworks. Specifically, it searches for broken or incomplete security logic — such as those brittle bits of authentication and authorization code that commonly sneak by traditional scanners. In real-world deployment, this may speed up code-review cycles and decrease toil for AppSec and platform teams.
- CyDeploy: It maps every application and device on your network and then builds digital twins of them to safely test patches and policy changes or updates before deployment. With asset lists that are perpetually incomplete, this approach enables teams to run what‑if experiments at scale with the ability to automate change validation — a common audit and uptime hassle in complex fleets.
- Cyntegra: Targets ransomware resistance by using a hardware‑plus‑software architecture for isolating a clean image of the system. Should adversaries encrypt production assets, Cyntegra guarantees the rapid restoration of OS and applications from data and credentials in minutes to reduce potential downtime and blast radius — lessons learned the hard way by high‑profile breaches, including those across healthcare and hospitality.
- HACKERverse: Exercises autonomous AI agents which emulate known adversary techniques in a contained environment to validate that deployed security tools work as advertised. Consider that as constant control assurance — proof that your EDR, email security or API gateway is really catching what the datasheet claims. That feedback loop can tune configurations and also justify spend.
- Mill Pond: Tackles “unmanaged AI,” the deluge of employee‑introduced tools and browser extensions that secretly process your sensitive data. The product uncovers unreported AI usage, flags dangerous data flows and helps security teams establish policy guardrails. As data residency, model‑training opt‑outs and privacy mandates tighten, the shadow AI problem becomes table stakes.
- Polygraf AI: Creates small language models optimized for cybersecurity applications like policy enforcement, data protection and deepfake detection. The better latency, lower price and finer control that these SLMs provide will make them compelling for high‑throughput SOC triage or on‑device inference use cases where privacy and determinism are concerns.
- TruSources: Specializes in real‑time deepfake detection across audio, video and images for identity verification and fraud prevention. Given the involvement of synthetic media in scams used to commit payment fraud, account takeover and social engineering attacks, instant signal analysis — voice‑dynamics integrity measurement, facial liveness and artifact scoring — may become a precondition for fintechs, gaming companies and online marketplaces.
- Zest: AI‑based platform to streamline vulnerability management across clouds and application stacks. With a focus on correlating exposures, ordering by severity and business context, and auto‑populating remediation work, Zest takes aim at the gap that often exists between scanners and patching, which is where MTTR seems to slip despite timely alerts.
Why these cybersecurity bets matter for enterprises
Ransomware is the No. 1 threat in both European and U.S. reporting, median detection times have decreased, and operational technology, cloud and SaaS are expanding the footprint. In the meantime, content authenticity is becoming security‑critical as deepfakes set their sights on payments, KYC and remote onboarding. The startups above address those realities: build AI‑natively but safely, continuously verify controls, see all the assets and recover quickly when prevention doesn’t work.
Equally important, many teams fall in line with regulatory expectations: proof of control effectiveness, data minimization in AI workflows and speedy incident response. That compliance‑by‑design stance mitigates audit fatigue and fosters actual resilience.
What to watch next as AI reshapes enterprise security
When pilots respond, expect them to focus on hard versus soft measures of results — decreased phishing success rates, fewer false positives in the environment and less time to patch at one end, and measurable recovery SLAs on the other. I’ll be watching for ISV collaborations with cloud providers and identity platforms, and support for standards such as SBOM, MITRE ATT&CK and CISA’s Secure by Design principles will also prove interesting. And if these nine can convert early traction into repeatable wins, they will shape how AI‑era security is actually realized inside the enterprise.

