Microsoft is putting additional security hardening around how Internet Explorer Mode functions inside Edge after new attacks abused long-standing components in Internet Explorer to attack Windows systems. The company says it has reason to believe that threat actors are persuading users into loading malicious sites in IE Mode and then chaining two different vulnerabilities, which are under active exploit, for full device takeover.
What Microsoft Changed in Edge’s IE Mode
IE Mode is sticking around in Edge to keep legacy, IE-only sites working, but Microsoft is stripping out casual entry points for non-business users. The explicit IE Mode toolbar button, right-click context option, and hamburger menu options are being removed, making it more difficult to quickly flip a page into legacy rendering with the click of a button.
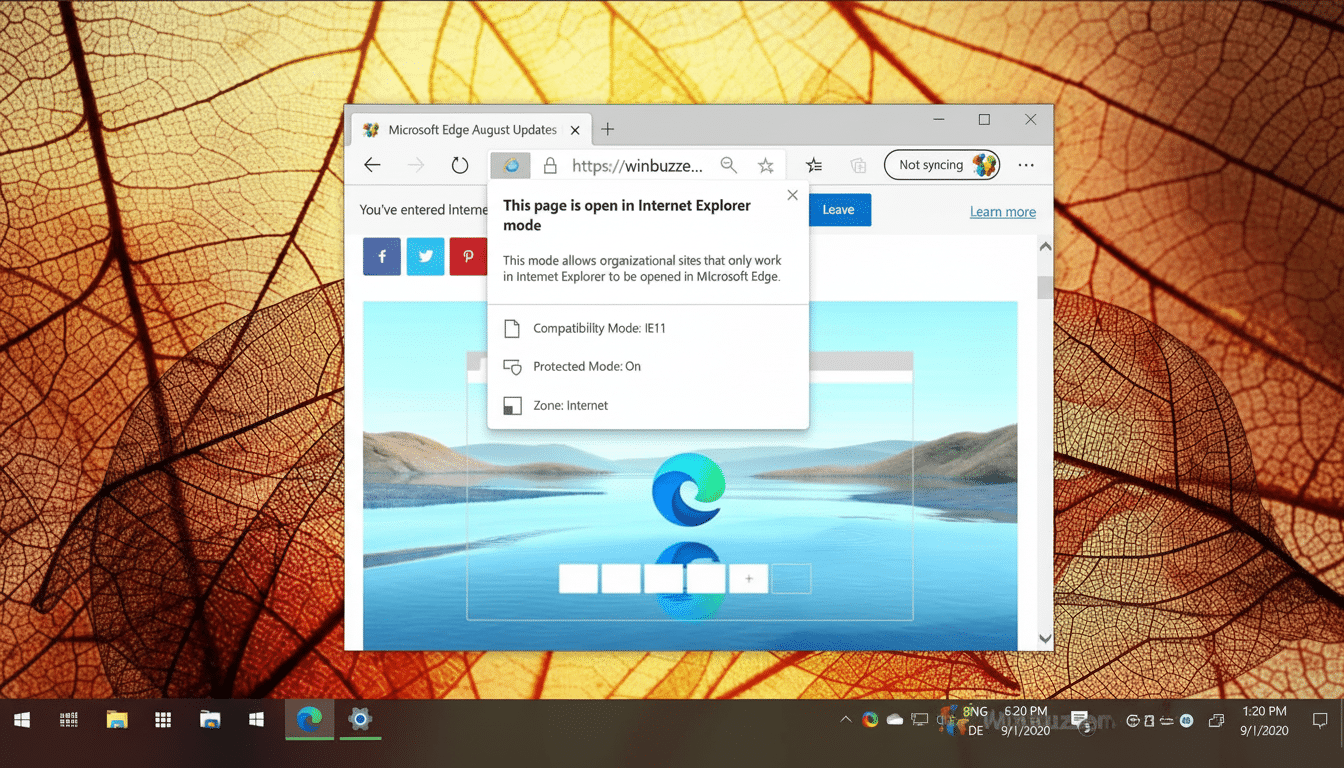
Instead, home users will need to explicitly add sites through Edge settings on a per-site basis before IE Mode can load. Microsoft’s aim is to force a conscious decision, preventing speedy switches back to outdated technology that attackers have mastered in many cases through simple social engineering.
Crucially, Microsoft emphasizes this isn’t a security patch; it’s an increase in friction. IE Mode enterprise logic (based on centrally managed site lists and group policies) will not change, to avoid potential disruption of existing line-of-business applications.
How Attackers Are Using IE Components for Exploits
Nudging users to reopen pages in IE Mode has leveraged convincing, official-looking websites and prompts, according to Microsoft’s security team. Attackers then use an exploit to achieve remote code execution via Chakra, Internet Explorer’s JavaScript engine. They are then able to use a second vulnerability to escape the browser and elevate privileges — high enough so that they can drop malware, travel laterally through the network, and siphon data.
It’s a trick that is well known to the people whose job it is to contain incidents. In recent years, Microsoft researchers and Google’s Threat Analysis Group have linked similar chains to state-backed actors, including North Korean teams that turned memory corruption bugs in Internet Explorer into a tool for compromising targets. IE was retired and disabled in Windows, but core components — MSHTML, ActiveX, and Chakra — are still available when IE Mode is enabled, maintaining a legacy attack surface.
The U.S. Cybersecurity and Infrastructure Security Agency has consistently recommended organizations patch or ditch old browser tech, pointing to the long tail of vulnerabilities in components such as MSHTML that still turn up on the Known Exploited Vulnerabilities chart. These doors remain, which means social engineering still makes its mark as the on-ramp toward high-impact intrusions.
Why IE Mode Remains And Who Is The Most At Risk
Because it’s old, IE Mode has in practice been a bridge for critical legacy web apps — government sector, industrial operators, healthcare services, and financial services among others. Migrating complex, internal applications takes time — often years, especially when the applications depend on ActiveX controls, document modes, or custom authentication flows baked for Internet Explorer.
The risk profile is uneven. However, there are few, if any, consumers in 2025 who need IE Mode; therefore the net effect of reducing one-click access is to increase convenience. Enterprises, meanwhile, concentrate risk on certain legacy sites. That makes governance possible — but only if organizations proactively manage site lists, watch usage, and strictly enforce isolation for IE-reliant workflows.
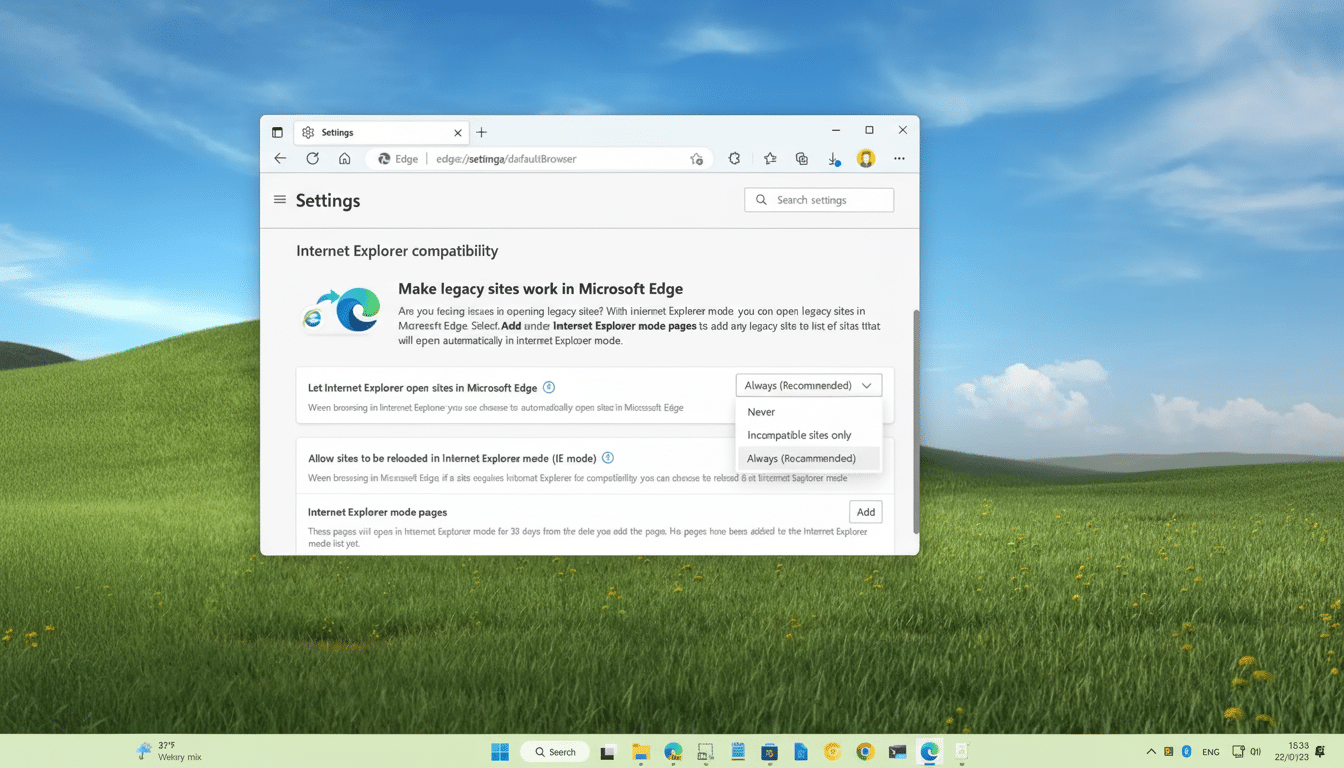
What Security Teams Can Do to Reduce IE Mode Risk
So, for individuals the guidance is easy: if you don’t need IE Mode, keep it turned off. Be cautious about any prompt that requests you to reload a page in another mode, and make sure Edge is up to date as well as your Windows OS. Microsoft Defender SmartScreen and reputation-based protections can go a long way in blocking known-bad pages, but they won’t prevent a user mode switch on a spoofed site.
However, enterprises will want to have more governance around this feature than Microsoft’s new friction provides. Mitigation steps include:
- Restricting IE Mode to a list of allowed internal domains
- Segmenting networks so internally hosted sites that rely on the IE browser have limited access
- Applying Windows Defender Application Control to limit which code can execute if a browser sandbox is circumvented
Attack Surface Reduction rules in Microsoft Defender for Endpoint can help offset common post-exploit behavior, and modern EDR signals should be monitored, specifically:
- Anomalous process chains (ie_to_edge transitions)
mshtml.dllinvocation- Unexpected PowerShell spawning from Edge
Security teams should also evaluate conditional access and device compliance policies to ensure that legacy browsing doesn’t become a black hole.
A Step Forward for IE Mode Security, But No Cure
Microsoft’s restrictions on casual IE Mode use are, in that light, a sensible decision — less convenience for attackers who are powered by fast clicks. But it is only a speed bump, not a repair. Long-term risk only goes down as organizations retire their legacy web technologies or wrap them in strong isolation and policy controls.
The real lesson here is clear: legacy elements do not die gracefully. So long as Internet Explorer’s plumbing is exposed, motivated actors will search for seams. Closing those gaps — by deprecating, isolating, and governing with discipline — is as important as any single Chrome update.
One based on the same story Microsoft’s security team has told, and incident responders have verified, for years: attackers follow the path of least resistance. Today, that journey leads to IE Mode. The fewer doors that remain ajar, the less chance they have.

