Francesco Nicodemo, an influential adviser to center-left figures in Italy, says that he was put on a Paragon spyware watch list as well, further enriching an ever-more-intricate surveillance scandal with a politically sensitive chapter. And he revealed that WhatsApp told him it suspected potential state-sponsored hacking and has since publicly demanded an explanation for why a private citizen, in his capacity as a political consultant, would be engulfed by high-end surveillance.
His account widens a controversy that has already embroiled journalists, immigration advocates, and business leaders in Italy, challenging longstanding assertions by governments and vendors that commercial spyware is only available to pursue terrorists and serious criminal networks.
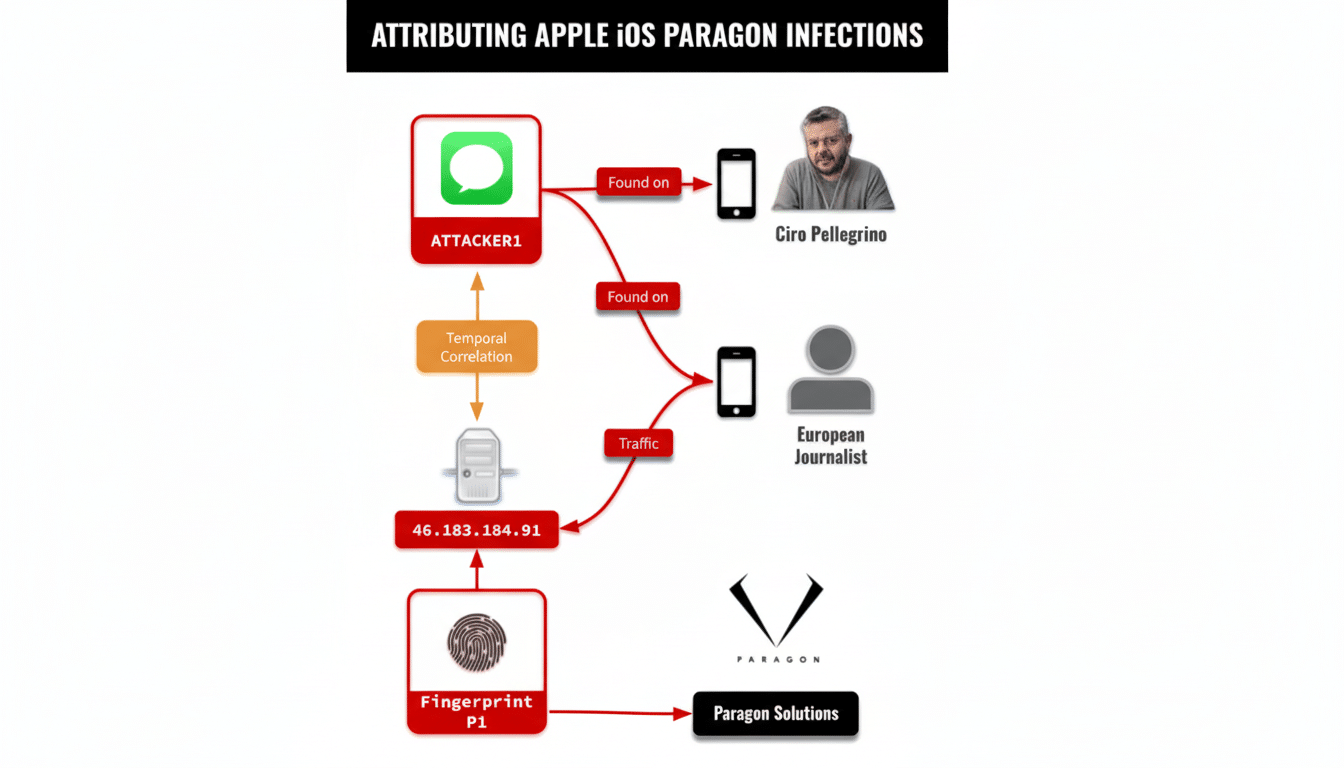
What Nicodemo Says Happened in the WhatsApp Spyware Alert
Nicodemo tells me that he got a WhatsApp message warning of an advanced, most likely government-backed targeting effort. He initially held onto the tip to avoid having it become a political cudgel, but is now calling on authorities to explain who ordered the operation and what legal basis it was based upon. A senior researcher at The Citizen Lab, which has documented abuses of mercenary spyware around the world, confirmed that Nicodemo received the WhatsApp alert and called on Italian authorities and the vendor to provide transparency.
Although no public forensic report has been divulged outlining the mechanics of the intrusion on Nicodemo’s phone, the notification does line up with how platforms notify high-risk users. Messaging applications and other Meta platforms have also offered targeted notifications in the past when their threat intelligence teams identify patterns indicative of commercial spyware operations.
Paragon Under Scrutiny Amid Italian Surveillance Allegations
Paragon, an Israeli spyware vendor recently taken over by U.S. private equity following its acquisition by AE Industrial Partners and merger with cybersecurity company REDLattice, has come under increasing scrutiny for use of its tools.
As with other mercenary tools, Paragon’s technology seems to have been built for stealthy, full-device access—including capturing messages, calls, files, location data, and potentially data from the microphone and camera.
In the first wave of revelations involving Italian targets earlier this year, Paragon took steps to discontinue doing business with government customers in Italy, including the intelligence services AISI and AISE, according to people familiar with the matter. The officials were granted anonymity because they could discuss a closely held intelligence program named in the indictment. The company did not comment on the newest accusations, and the key questions, such as who ordered the targeting and under what legal authority, remained unanswered.
Who Ordered the Targeting and Under What Legal Authority
The central unknown is attribution. The parliamentary oversight body, COPASIR, previously said that Italian intelligence agencies were responsible for some spyware operations that had come to light and claimed some cases—like those of immigration activists—were carried out with lawful authority. Meanwhile, the committee also found no evidence linking targeting of a leading newsroom director to AISI or AISE, and some related cases were still not included in its purview.

The incident bears unavoidable political weight, too—Italy’s intelligence services report to the office of Prime Minister Giorgia Meloni. NYT >
If the consultant’s claims are borne out, it will be left to investigators to judge whether legal warrants existed, if the operation was proportionate, and if any abuses were carried out against political activists or civil society figures.
A Wider European Pattern of Abuses Involving Commercial Spyware
Italy’s struggles are part of a broader European reckoning over commercial spyware. Reports by The Citizen Lab and Amnesty International’s Security Lab have found repeated abuses of such tools from Greece to Spain and Poland. Europe’s Parliament has already opened inquiries into spyware governance, and data protection authorities have cautioned that uncontrolled powers can silence speech, undermine press liberties, and erode democratic oversight.
Technology platforms are also now the barometer of abuse. WhatsApp’s state-sponsored threat disclosures and Apple’s threat notifications have targeted journalists, politicians, and activists across the globe, evoking the watershed moment in 2019 when WhatsApp informed about 1,400 users that they had been attacked with a different mercenary tool. The pattern keeps repeating itself: Commercial spyware can and does leap from the marketplace into the public square.
What Transparency Might Look Like in Italy’s Spyware Probe
Meaningful clarity requires three steps, experts say: an explanation by the Italian government of lawful authorizations and scope limits; vendor auditing and client accountability, such as logs that identify which customer ran which operation; and independent device forensics done by trusted labs to verify infection chains and exploits. Italy’s data protection authority could also rule as to whether or not surveillance, if it was carried out, was necessary and proportionate.
Nicodemo isn’t wasting any time: The first question is straightforward: Who ordered the operation and why? Unless and until the authorities or the vendor come up with a credible explanation, Italy’s spyware debate will continue to be unresolved—and both government oversight of, as well as commercial safeguards against, spyware will be called into question.

