Being locked out of a Google account can be very frustrating, will turn your day upside down and may cause some financial damage. To help with that, Google has started releasing a feature called Recovery Contacts, which is a new way for trusted friends or family members to assist in proving your identity when you cannot sign in. It’s fast and easy to establish, invisible until you need it, and could be the difference between a five-minute fix and a draining few days grinding out the solution.
Why Recovery Contacts Matter for Google Account Security
There are common reasons people get locked out: They forget a password, lose their phone or perhaps try to do an ill-conceived reset. And there are the extraordinary reasons, kamikaze ones that change how account security works, such as account hijacking. The Identity Theft Resource Center recorded a record 3,205 data breaches in 2023, reflecting the fact that even cautious users can tumble into front-page disasters. When locked out, every second matters.
- Why Recovery Contacts Matter for Google Account Security
- How Recovery Contacts Work to Help Restore Access
- Set Up Recovery Contacts: A Simple Step-by-Step Guide
- Eligibility and Limits for Using Google Recovery Contacts
- If You’re Locked Out of Your Google Account, What to Do
- Other Protections You Should Enable for Stronger Security
- Bottom Line: Set Up Recovery Contacts to Save Time Later
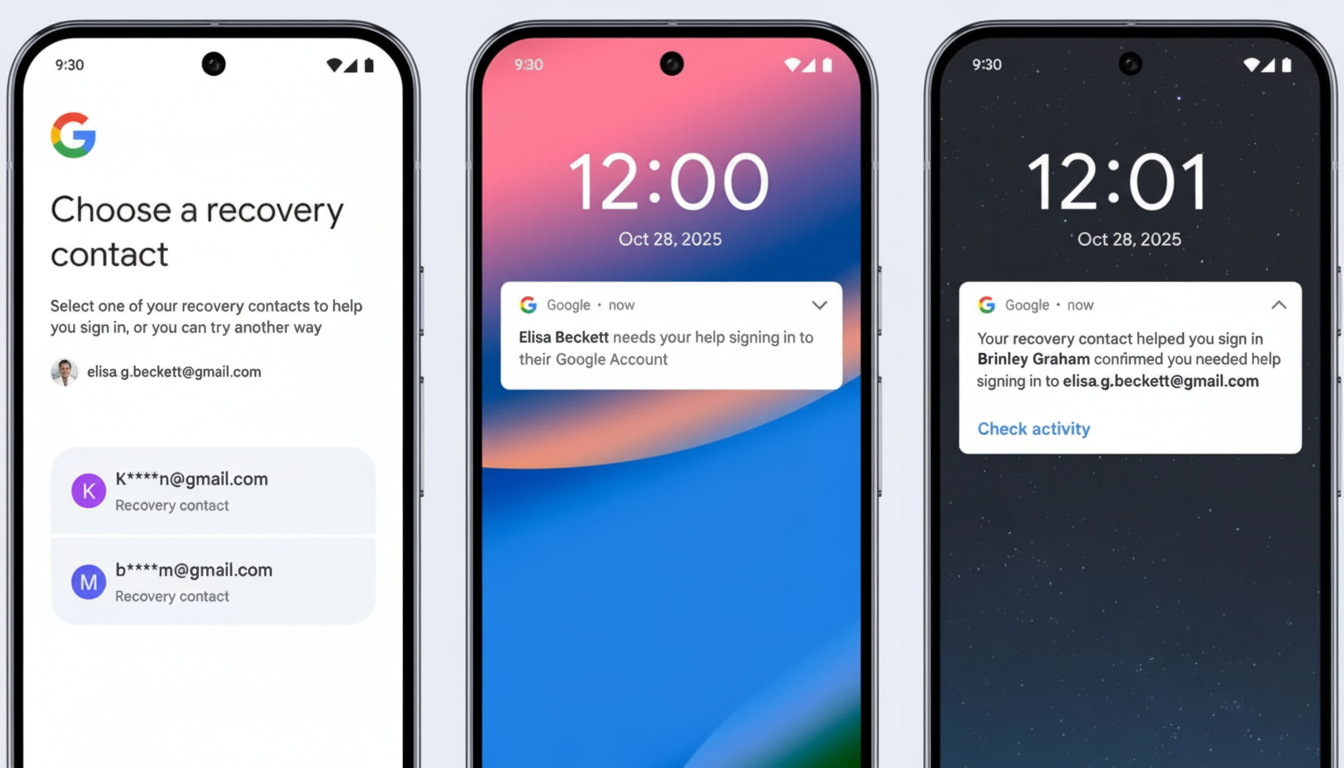
Google’s answer is simple: allow you to preselect people who vouch for your recovery. It serves to minimize the friction, while allowing you full control. Studies Google has conducted with academic research partners show that layered protections significantly increase the barriers that attackers face, and Recovery Contacts adds a human‑verified layer that’s hard for scammers to spoof.
How Recovery Contacts Work to Help Restore Access
You pick up to 10 trusted contacts. They receive a plea and also must accept before helping. Should you ever be locked out — for example, if you forget your password or lose access to your passkey device, or have reason to believe they may have been compromised — a standard recovery flow will be available that includes the “contact‑assisted” option.
Google gives you a one‑time code. You call your trusted person and read the code to them. They verify it on their side, signaling to Google we really are who we say we are. After we verify, you can regain access and protect your account. Crucially, contacts don’t get to see your emails or photos or files, nothing private — they just verify a code.
Set Up Recovery Contacts: A Simple Step-by-Step Guide
- On desktop or mobile, sign in to your Google Account and then open Manage Your Google Account. Go to the Security tab.
- Scroll down to the “How you sign in to Google” section and click Recovery Contacts.
- Select Add Recovery Contact, search for the person using their name or an email address and then send your request. Tell them they should accept it immediately.
- Do the same for a second or third trusted person. Go for diversity — the more households and carriers the better, so your internet isn’t blocked by a single outage. Schedule an annual contact-check as a reminder.
Eligibility and Limits for Using Google Recovery Contacts
- Maximum of 10 contacts can be added.
- Child accounts aren’t able to add or be recovery contacts.
- Google Workspace accounts and accounts with Advanced Protection can be contacts for other people but can’t add their own.
Choose people with a track record of answering calls, holding steady phone numbers and using good security discipline.
Keep your call list relatively small, so it isn’t unwieldy to manage.
Tell them you won’t write your password or 2‑Step Verification anywhere — only the one‑time recovery code Google gives them to enter during this process.
If You’re Locked Out of Your Google Account, What to Do
- On the account recovery page, enter your recovery contact information.
- After a failed sign‑in, you can use the instructions above to help us help you regain access. You will get a one‑time code from Google.
- Directly call your chosen contact, if you can, instead of texting the code over unencrypted routes. Read them the code; they’ll verify it on their device.
- After you’re verified, follow Google’s on‑screen steps to get back into your account and be sure to update your password, passkeys or recovery methods right away.
Be alert for social engineering. Google or your contacts won’t ask you for your password, 2FA codes or backup codes. Only get to share the one recovery code you were shown during that session.
Other Protections You Should Enable for Stronger Security
Google is also bringing Sign in with Mobile Number for new Android device setups. If your old phone was lost or broken, the service uses your phone number to identify your account on the new device and relies on your previous device’s lock‑screen passcode as well as an additional code from iCloud — in other words, something you know plus something you have. It is designed to fill that vulnerable transition from one device to another.
In Messages, Google is now enabling automatic scam and phishing protection by default, and has introduced Key Verifier – a way for you and an interlocutor to compare encrypted QR codes to verify end‑to‑end encryption keys. Security folks have been telling for years that there should be more visible key verification, and now you get it as an ordinary user in Android 10 and above.
Cover your bases with passkeys or 2‑Step Verification, strong unique passwords and the current recovery email and phone information.
The consumer guidance provided by the Federal Trade Commission is a constant reminder that layered controls will help mitigate your risk, and that adding modern sign‑in protections with Recovery Contacts improves things substantially.
Bottom Line: Set Up Recovery Contacts to Save Time Later
It took minutes to set up Recovery Contacts, but it could ultimately save you hours — or years of access to email, photos and files. Set it up today, tell your contacts what to expect and consider it a fundamental piece of your Google security toolkit.

