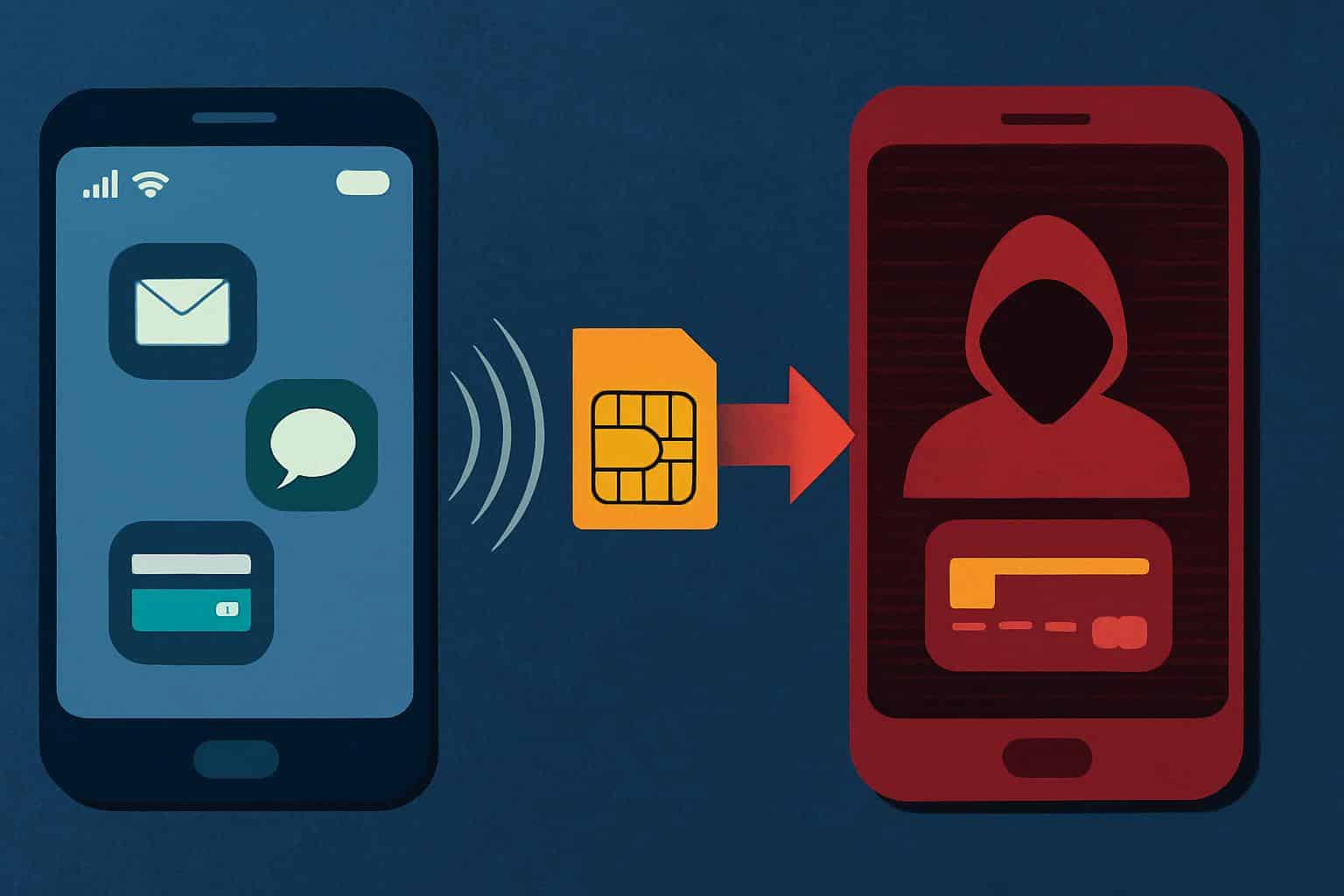
Phone cloning isn’t the most cinematic, but it’s still a security risk. Attackers copy your mobile line to a new SIM or hack your device to take data and codes. The F.B.I.’s Internet Crime Complaint Center has linked SIM-swap fraud to tens of millions of dollars in losses a year, and regulators like the F.C.C. warn that number hijacking can unlock bank accounts and email in minutes. Here’s how to spot the signs early — and what to do next.
What “cloning” really means
There are two primary threats. The former is line cloning: A criminal tricks your carrier into believing it’s your number on a SIM card they control (a “SIM swap”) and/or extracts the credentials from your SIM card to impersonate you, then intercepts texts and calls, including one-time passcodes. The second is data cloning: malware or spyware copies your messages, your photos and even your keystrokes from your phone. Some schemes are even capable of spoofing your device’s IMEI, a unique identifier that is established by the GSMA, to pass themselves off as your hardware on the network.

How to tell if your number was hijacked
And the classic tell: sudden loss of service. If calls are going straight to voicemail, texts are no longer coming through, or you receive a “No SIM” alert on your phone (even when you have a good signal), assume your number is being ported over to another SIM and call your carrier immediately.
Look out for unexpected “restart your phone” messages, particularly if they claim to be from support. Attackers will occasionally tap a swap and goad you to power cycle so that their activation finishes before you realize.
Review your bill and account portal for unfamiliar calls, international or premium-rate fees or a new line/device you don’t recognize. Recent SIM changes or number transfers are a leading indicator for most carriers, so review those logs monthly.
Unsolicited security codes are another alarm. If you get 2FA texts for services you didn’t try to sign into, it’s possible that somebody’s testing access with your number.
Signs your actual device was cloned or compromised
Performance that falls off a cliff — your computer is hot at idle, your battery is being drained at incredible speed, maybe your system crashes at random — is another sign that there might be something restrainedly evil happening in the background. Bugs can do these as well, but malwareslørt slowness is pretty relentless, and it comes with weird pop-ups or permissions requests.
Look through your installed apps for anything new, especially with wide access to SMS, Accessibility, or Device Admin. If an app refuses to be uninstalled, it could be a sign that spyware is hard at work; you may need to do a factory reset.
Account clues help, too. Check your Google or Apple account for new logins or devices. A Find My Device or other such service showing activity where your phone is not can show that someone is misusing your account identity or identifiers.
Fast, commonsensical tests to settle questions
Call your own number from a different phone. If it rings somewhere else or you get a random voicemail greeting, escalate to your carrier’s fraud team.
Log in to your carrier account and check recent SIM activations, number ports and devices on the account. Assign or verify a port-out PIN, if your account offers that feature.
Look over your phone bill’s itemized calls and data usage. In line cloning, it is common to see unexplained spikes or destinations that you have never visited.
Check your IMEI against the label in Settings or the box that came with your phone.
To check your IMEI, dial *#06#. Differences are few and far between, and can also suggest shenanigans or refurb problems you may want to take up with your carrier or manufacturer.
What to do if you believe you’ve been cloned
Contact your carrier first. Ask them to lock down your account, reverse any number transfers, get a new SIM or eSIM, and place a port freeze or transfer lock. A separate pin number for number changes Many providers will stick a separate pin number on number changes — whip one on straight away.
Secure critical accounts. Change email and banking passwords, log out active sessions, and change 2FA from SMS to an authenticator app or hardware key. Banks can add additional verification if you advise that a regularly used number has been compromised.
If you suspect malware, back up the essentials and do a factory reset, then restore only from known good sources. Update your operating system and security patches, and reinstall apps selectively, paying attention to the permissions those apps request.
Report the incident. If funds moved, the F.B.I.’s Internet Crime Complaint Center, consumer protection groups and local police can record the case. The fraud department of your carrier should also record the attack to avoid future occurrences.
Protect yourself and others
Lock the front door: enable the strongest screen lock and a SIM PIN so that a thief can’t move your card to another phone unnoticed.
Don’t leave your device unattended, and try not to plug into unknown charging stations.
Strengthen your carrier account with a distinct port-out PIN, and inquire about number transfer locks. Other providers will block all ports unless you get an ID in a store.
Be choosy about apps. Download from official stores, turn off unknown sources and check for Accessibility or Device Admin permissions time to time. Be diligent with systems and app updates.
Rethink recovery. Wherever possible, replace SMS-based 2FA with authenticator codes, and make sure the emails and phone numbers you rely on to recover the account aren’t easy targets for an attacker.
When it’s likely not cloning
Some symptoms can be caused by network outages, billing problems, or a busted SIM. If service resumes following reseating your SIM card, a restart, or getting in touch with support about a local outage, then you probably have a benign problem. (But if you have several warning signs — no service plus weird charges or unwanted codes — consider it a cloning case and respond quickly.

