A pseudonymous hacktivist who goes by the name Martha Root claims to have remotely wiped three white supremacist websites from the internet using backdoor vulnerabilities live onstage while giving a talk at this year’s Chaos Communication Congress in Hamburg; their announcement was met with a roaring ovation, cheers, and applause from the audience on site at CCC, as well as immediate denial, downplaying their impact, by the still-anonymous sites’ admin. Days later, the domains are still offline, stoking new controversy in a long-standing debate over “hack back” tactics and the ethics of attacking eXtremist infrastructure.
Live takedown at CCC hacker conference during talk
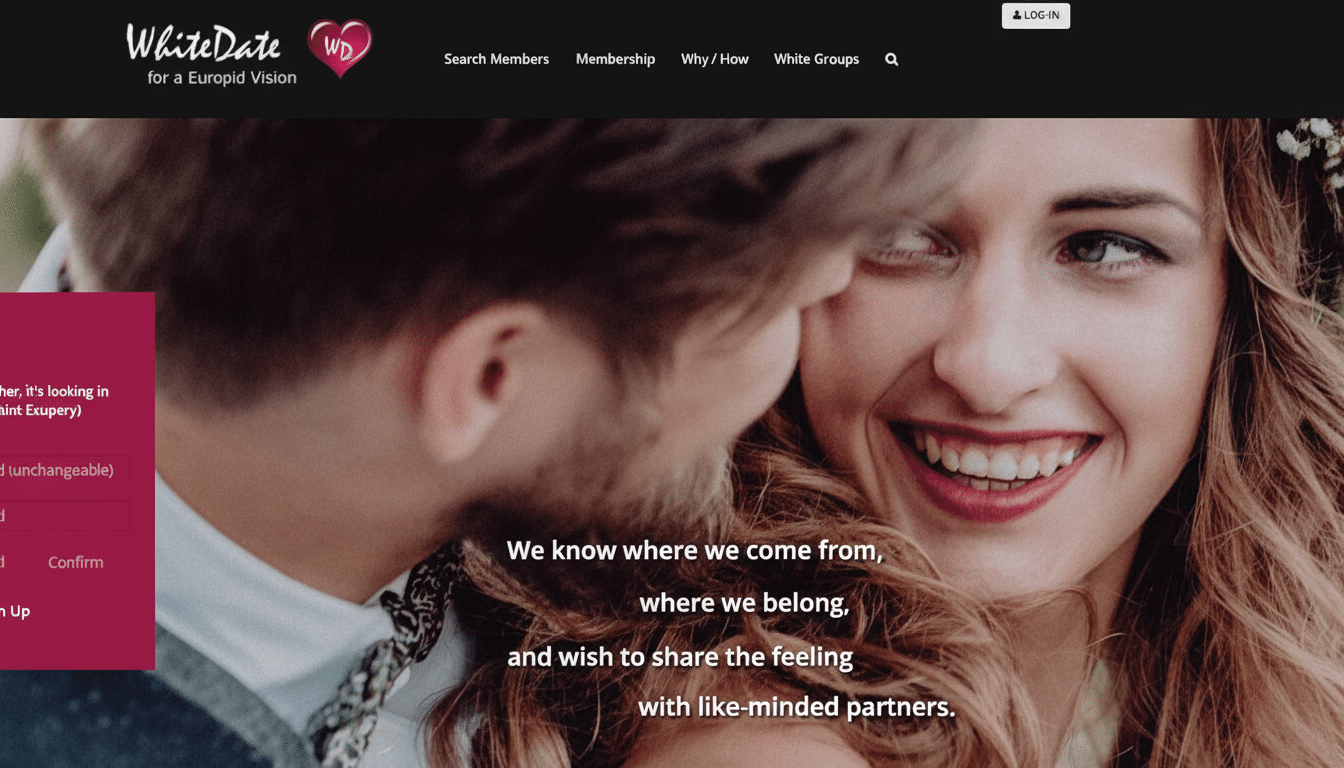
Root, donning a Pink Ranger costume, ended a presentation with journalists Eva Hoffmann and Christian Fuchs by triggering the takedown of three services—WhiteDate, WhiteChild, and WhiteDeal—that provided matchmaking for white supremacists along with reproductive coordination and gig surfing.

Hoffmann and Fuchs had previously written about the network for the German weekly Die Zeit, helping to establish how the ecosystem functioned.
The administrator of the sites admitted on X that he had been breached, called the attack “cyberterrorism,” and warned that he would respond. The admin also said that his personal social media account was deleted and subsequently restored. The sites have not resurfaced at time of writing, and the hosting footprint looks pretty lifeless.
What the data reveals about the three targeted sites
Prior to going offline, Root had described scraping publicly available content from WhiteDate, mentioning low-level security measures and sloppy operational security. User-generated images also contained specific geolocation metadata that can be used to determine home addresses and daily schedules when the platform fails to strip it away.
Root’s figures detail that there were over 6,500 profiles, with a gender split of 86 percent men and 14 percent women. The scraped data includes:
- Names or handles
- Profile photos
- Video slideshows and descriptions
- Country of origin
- Number and age of followers (if visible)
- Language
- Self-reported location
Root said that emails, passwords, and private messages were not included “for now,” though the assertion has not been independently confirmed.
DDoSecrets, a nonprofit group that publishes classified or restricted materials in the public interest, said it received a large collection of files from all three services named “WhiteLeaks.” The group is also vetting access requests from journalists and academics instead of dumping the entire 100GB trove all at once — a routine stopgap toward transparency that weighs against maximum harm.
Root also made the claim that they thwarted account-verification gates by using an AI chatbot known as “Tony,” which managed to navigate screenings meant to ensure members were white. The disclosure serves as a reminder of the ways that low-cost automation can bypass superficial gatekeeping and expand the attackable surface for sites that are not well defended.
Security and ethics in the spotlight after onstage hack
The onstage takedown pulls hacktivism back into the spotlight of one of the world’s most influential hacker meetups. Within the security world, there’s long been a tension between direct-action operations and norms that oppose vigilante tactics. Civil society groups such as the Electronic Frontier Foundation have long cautioned that hacking back can put bystanders at risk, make investigations more difficult, and fall afoul of computer misuse laws.
Germany’s cybercrime laws, like those in most jurisdictions, make unauthorized access and data interference punishable crimes regardless of the targets’ ideological affiliations. Lawyers say liability can reach beyond national borders if infrastructure, or victims, are elsewhere. There would be actual civil liability for publishing personal data that could result in harassment or violence, a risk DDoSecrets and other archival groups try to mitigate by vetting requesters and redacting sensitive fields when appropriate.
Impact on extremist networks and their regrouping efforts
Shutting extremist sites off forces them to rebuild, but society has found it impossible to prevent communities from reconstituting on new infrastructure or moving to invite-only channels. The impact when an account is banned isn’t just that people pile on to try to get them kicked off—leading Mr. McEwan and others to try gaming the system in return—but it also often has little impact on getting more fighting-style content taken down. Monitoring groups such as VOX-Pol, George Washington University’s Program on Extremism, and Moonshot have documented how repeated bans can splinter audiences, drive up operational costs, and reduce scale—even as hard-core adherents regrouped elsewhere.
Wider context hints at why these ecosystems attract attention. Watchdogs like the Anti-Defamation League have reported record levels of white supremacist propaganda over the last few years, signaling longstanding attempts to recruit and normalize extremist messages on social media. There’s been increasing pressure on infrastructure providers to police terms of service, and recent flashpoints around these sorts of decisions—from delistings by domain registrars to hosting bans—have made it clear that such enforcement can make a tangible difference in toppling organizing capacity.
A cautionary cyber tale of hygiene for site operators
Assuming that Root’s account is correct, the episode is a case study in how not to handle an operational issue. Leaving geotags on user images, not sanitizing uploads, and relying on superficial verification checks are openings to compromise. The least you can do to protect your users’ information is a great deal: mandatory metadata stripping, the principle of least privilege (which refers to granting only the minimum level of access necessary for a particular task), robust audit logging, and routine third-party assessments.
At this writing, all three sites are dark, a 100GB dataset is on limited release, and both sides of the hacktivist debate are using the temporary chaos as an opportunity to make their case.
Whether the takedown is a turning point in its rise or merely a temporary setback for this niche extremist network will depend on what pops up next and how researchers and law enforcement react—as well as the degree to which platforms are taking their policy shifts seriously.

