A self-described hacktivist has scraped more than 500,000 payment records tied to consumer-grade stalkerware and phone-tracking services, exposing buyers’ email addresses and partial payment details associated with apps marketed for covert surveillance. The cache links hundreds of thousands of transactions to a cluster of monitoring tools, highlighting poor security practices in an industry that thrives on secrecy.
What the Leaked Payment Records Actually Exposed
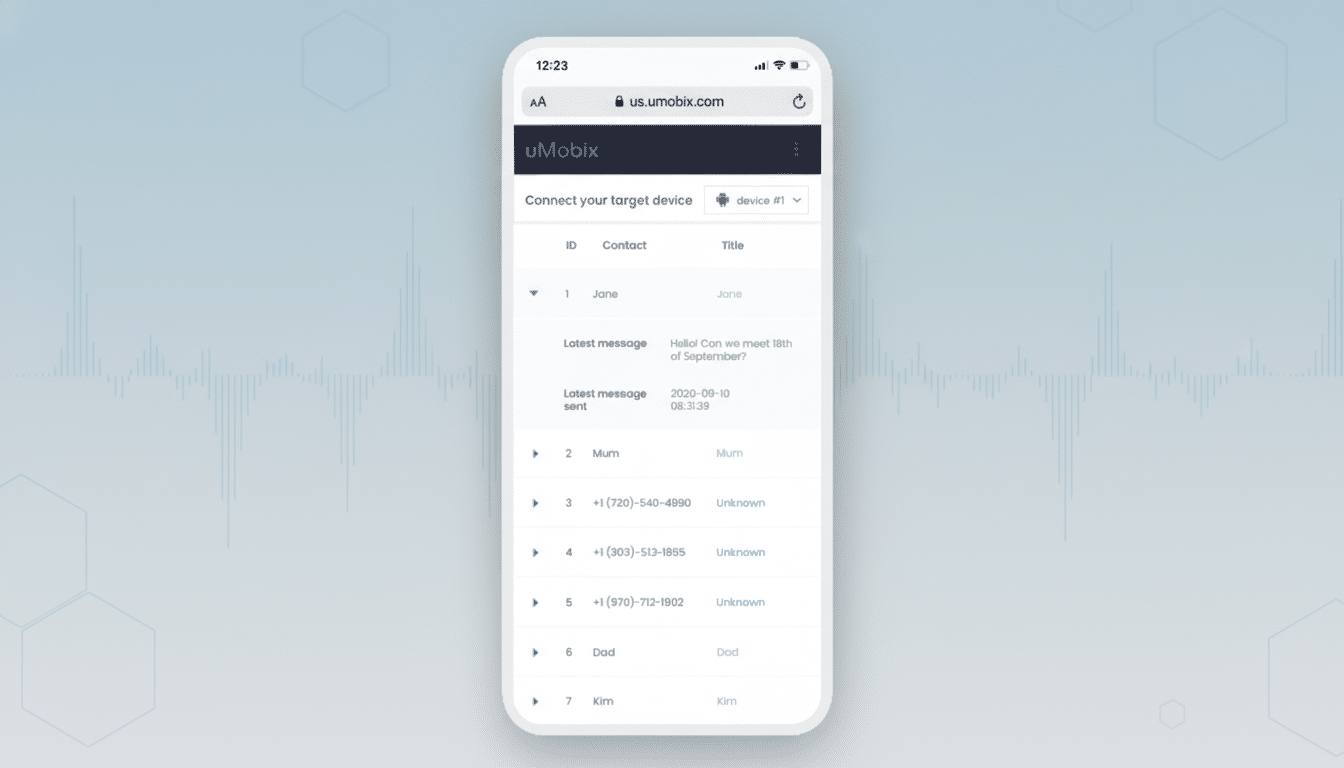
The dataset contains checkout records for phone and account monitoring products including uMobix, Geofinder, and Peekviewer (formerly Glassagram), along with entries for Xnspy, a known surveillance app previously tied to a significant data leak. The exposed fields include customer email addresses, transaction identifiers, amounts, and partial payment information drawn from the vendors’ purchase systems.
- What the Leaked Payment Records Actually Exposed
- How the Checkout Data Was Scraped at Massive Scale
- A Tangled Web of Surveillance Brands and Entities
- A Pattern of Security Failures Across Stalkerware
- Legal and Safety Implications for Buyers and Victims
- Why the Payment Trail Matters for Enforcement Actions
- What Platforms and Users Can Do Now to Reduce Harm
- The Bottom Line on This Large Stalkerware Payment Leak
While the leak does not appear to include full card numbers, security experts warn that even truncated payment details and emails can enable targeted extortion, doxxing, and identity fraud. It also creates a paper trail for law enforcement and civil litigants by linking individual buyers to services often advertised for illegal spying on partners and family members.
How the Checkout Data Was Scraped at Massive Scale
The records were obtained through insecure checkout infrastructure that exposed customer and invoice data without robust authentication. In effect, sequential or guessable identifiers and unauthenticated endpoints allowed an attacker to enumerate transactions and pull related details at scale.
This is a textbook breakdown of basic web security controls: lack of access gating, predictable object references, and insufficient rate limiting. Payment platforms subject to PCI DSS are expected to enforce strict authorization, minimize data retention, and segregate sensitive systems—requirements that appear to have been brushed aside.
A Tangled Web of Surveillance Brands and Entities
The transactions point to a sprawling vendor network tied to a Ukrainian software company known as Struktura and a U.K.-presenting entity called Ersten Group. The brands in this ecosystem sell overlapping capabilities: GPS tracking, access to messages and photos, social media viewing, and activity logs that can be pulled from a target’s phone once the spyware is installed.
Industry researchers have long noted that stalkerware businesses operate through a patchwork of company names and white-label apps. Rebranding and jurisdiction hopping are common, making it harder for app stores, regulators, and payment processors to keep pace with enforcement.
A Pattern of Security Failures Across Stalkerware
Stalkerware vendors have a track record of mishandling sensitive data from both targets and purchasers. In 2022, Xnspy leaked private data harvested from tens of thousands of Android and iOS devices. Earlier incidents hit mSpy and Retina-X, and the U.S. Federal Trade Commission in 2021 banned the makers of SpyFone from the surveillance business for egregious security lapses and illegal tracking.
Telemetry from the Kaspersky State of Stalkerware report indicates tens of thousands of unique mobile users are flagged annually with stalkerware installations worldwide, underscoring a persistent threat that blends intimate partner abuse with commercial spyware. The Coalition Against Stalkerware, which includes advocacy groups and security firms, continues to document widespread harms from these tools.
Legal and Safety Implications for Buyers and Victims
Using stalkerware to monitor spouses, partners, or anyone without consent is illegal in many jurisdictions and can carry criminal and civil penalties. The newly exposed payment records heighten buyers’ legal risk by tying emails and invoices to specific surveillance services—and may also identify resellers or affiliates who profit from distribution.
For survivors of abuse, the incident is a double-edged sword. While exposure of buyer identities may aid investigations, the underlying business model depends on quietly harvesting victims’ messages, locations, and photos. Privacy regulators in Europe and elsewhere could scrutinize whether these companies processed personal data lawfully under frameworks such as GDPR, and whether they breached security and accountability obligations.
Why the Payment Trail Matters for Enforcement Actions
Financial records are often the most durable form of evidence. Even if apps rebrand or domains vanish, invoices, processor logs, and customer support tickets can persist in third-party systems. That makes payment data a powerful lever for regulators, banks, and card networks to sever services and for investigators to map relationships between entities that present as separate but operate in concert.
Card networks have previously cut off high-risk merchants, and payment providers can require remediation or offboarding when PCI DSS violations surface. If the scraped dataset is validated at scale, pressure will likely mount on processors and hosting providers that enable these operations.
What Platforms and Users Can Do Now to Reduce Harm
App stores and certificate authorities can intensify reviews of surveillance-linked binaries and revoke trust for stealth monitoring apps. Payment processors should audit merchants tied to stalkerware keywords, enforce stronger merchant due diligence, and mandate third-party security assessments before onboarding.
For potential victims, safety groups recommend checking device settings for unknown device administrators, suspicious accessibility services, and profiles that grant remote control; keeping operating systems updated; and seeking support from organizations in the Coalition Against Stalkerware. Survivors should prioritize personal safety planning and consult advocates before attempting device cleanups that might escalate abuse.
The Bottom Line on This Large Stalkerware Payment Leak
This scrape is not just another leak—it is a rare look at the financial backbone of a shadowy industry that preys on intimate access and weak security. By exposing who pays for these tools, the breach raises the cost of doing business for stalkerware vendors and could accelerate regulatory, financial, and criminal consequences across their networks.

