Cybercriminals piggybacked on YouTube’s endless appetite for game cheats and software cracks to run a sprawling malware operation that security researchers say quietly flourished for years. According to a new analysis from Check Point, a coordinated “YouTube Ghost Network” used more than 3,000 videos claiming to offer game hacks and pirated software to trick viewers into installing data-stealing malware.
The campaign leaned on familiar bait—free tools for popular titles like Roblox and cracked copies of Adobe Photoshop, FL Studio, and Microsoft Office—paired with slickly produced videos and convincing comment sections. Google was notified and has removed most of the malicious content, researchers said, but remnants of the network are still surfacing.

How the YouTube Ghost Network Actually Worked
Videos featured step-by-step “tutorials” and pinned comments that pointed viewers to download archives hosted on mainstream cloud services, including Dropbox, Google Drive, and MediaFire. Fake engagement—likes, timestamps, and templated praise from burner accounts—helped confer legitimacy and push the clips up in recommendations.
Victims were typically told to disable Windows Defender before running the download, a classic tell that something is amiss. Instead of cheats or cracked suites, the payloads deployed Windows info-stealers such as Lumma and Rhadamanthys, which are designed to vacuum up passwords, browser cookies, and cryptocurrency wallet details.
Attackers amplified reach by churning out new channels and hijacking existing ones through stolen credentials. Once a channel was compromised, its pre-existing audience and trust accelerated distribution, making takedowns a race against the algorithm.
Evidence of the YouTube Ghost Network’s Scale and Reach
Check Point’s investigation indicates the network has been active since at least 2021, with output accelerating significantly this year. Researchers observed that the volume of these videos has roughly tripled, underscoring the operation’s scalability and its success at evading moderation long enough to rack up views.
In one example, a compromised channel with 129,000 subscribers posted a “cracked” Photoshop download that drew 291,000 views and more than 1,000 likes. Another video promising an FL Studio workaround surpassed 147,000 views. Those view counts translate to sizable exposure for malware that can be deployed in seconds once a victim runs an executable.
The approach reflects a broader shift in criminal tradecraft toward using archive files and commodity info-stealers delivered through trusted brands and platforms. Multiple security labs have reported that archives like ZIP and RAR continue to rank among the most common malware delivery formats, in part because they slip past user suspicion and some legacy filters.
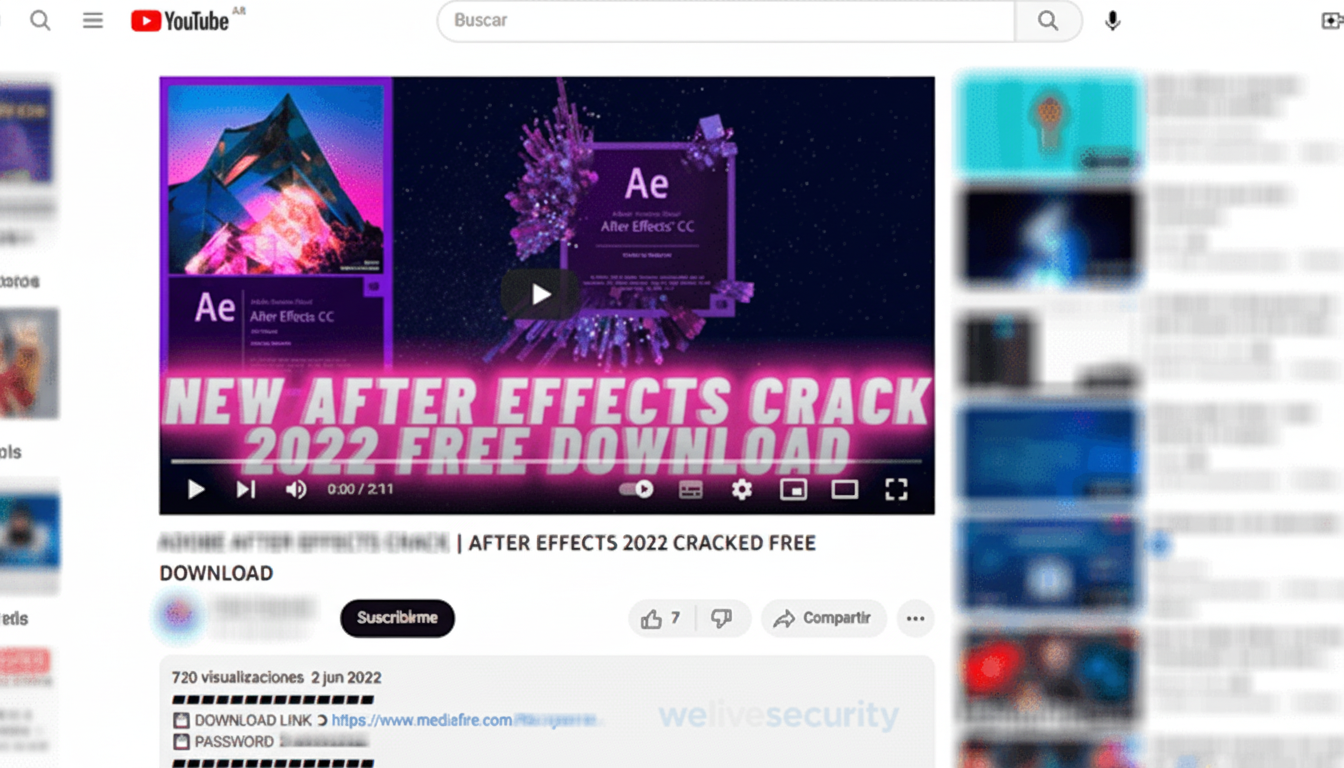
Why Cheats And Cracks Make Effective Lures
Game hacks and pirated tools sit at the intersection of high demand, constant churn, and plausibly “gray” behavior that many users rationalize. On YouTube, searches for terms like “cheat,” “crack,” and “free activation” reliably generate traffic, which the attackers weaponized with short videos, aggressive keywording, and copy-pasted comment scripts to simulate social proof.
The social dynamics matter: once a few apparent users vouch that a hack “worked,” the perceived risk drops. Couple that with instructions to toggle off security tools “to stop false positives,” and even cautious viewers can be nudged into bypassing the very defenses that would prevent infection.
What Users and Platforms Should Do to Respond Now
For users, the guidance is straightforward: avoid pirated software and game cheats; never disable antivirus protections at the direction of a video; and treat downloads hosted on consumer cloud storage as untrusted by default. Keep Windows Defender or a reputable endpoint suite enabled, restrict admin rights on daily accounts, and store credentials in a password manager with phishing-resistant multi-factor authentication.
Creators should lock down their channels with hardware security keys or passkeys to prevent takeovers, review third-party app permissions, and monitor for unusual uploads or community posts. For platform operators, faster cross-signal correlation—matching comment spam patterns, identical video scripts, and repeated cloud-hosting hashes—can surface clusters instead of whack-a-mole removals.
The Bottom Line on the YouTube Ghost Network Threat
The YouTube Ghost Network shows how efficiently criminals can turn creator tools, cloud storage, and engagement mechanics into a malware pipeline. The content looked routine, the comments felt familiar, and the downloads were only a click away—exactly why it worked.
Most of the malicious videos flagged by researchers are now offline, but the playbook will resurface. Treat any promise of “free” software or effortless game hacks as a security risk, because on YouTube as everywhere else, if it sounds too good to be true, it’s probably a payload.

