If you sign in to X with a physical security key, you need to take action. The company has imposed a re-enrollment window on those keys, warning that users who do not comply by the deadline will be locked out. The modification is due to X’s full transition from the old twitter.com domain to x.com, which alters how hardware-based 2FA systems work. According to X’s safety crew, the re-enrollment is not in reaction to a fresh security occurrence. Instead, it is a technical outcome of how the phishing-proof, up-to-date authentication binds your key to the site’s domain: Users simply need to re-enroll their key and verify they can still sign in.
Why your security key must be re-enrolled after the x.com switch
Security keys that make use of FIDO2 and WebAuthn are registered for a special cryptographic function called a relying party ID. This ID identifies the site’s web origin and ensures that keys aren’t donating your authentication to the incorrect service at the other end of that USB cable. Upon retirement of the twitter.com origin in preference of x.com, keys correlated with the former can no longer be completed for the new domain, so the browser will not continue the authentication ceremony. X stated that this is a specification change related to hardware security keys and their passkey credentials based on the domain of the old twitter.com. Authenticator app codes are unaffected because time-based single-use passwords do not establish web origin. However, whether or not you use a physical key to log in, it is recommended that you re-enroll since doing so now is a piece of cake.
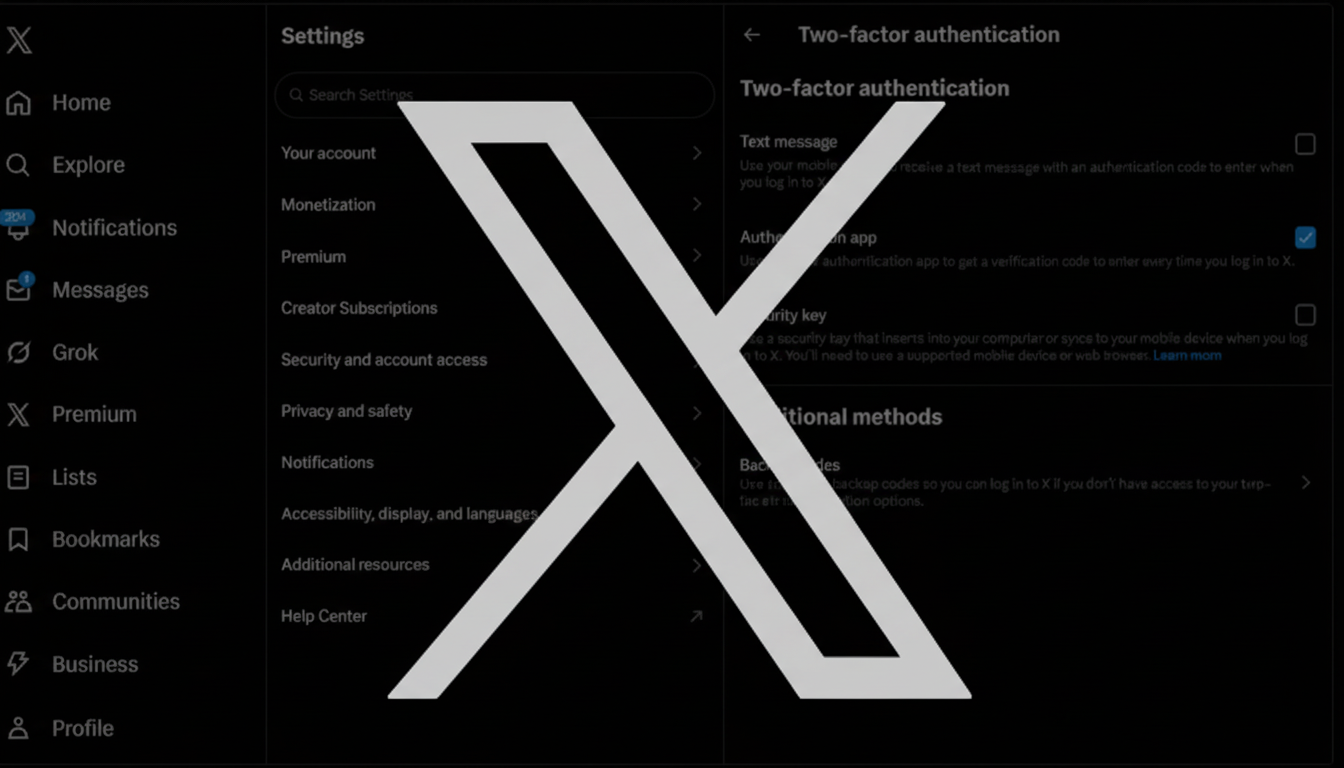
Open X in your web or mobile app, click on More > Settings and privacy. Select Security and account access, then Security, Two-factor authentication, and then Security key. Take that key—USB, NFC or Lightning—and have it ready: Follow the prompts to register it at x.com. If you have more than one key, do the same with the next ones.
Sign out and back in to verify that everything works after re-enrollment. If you’d like a backup plan, submit an authenticator app in the same menu. Agencies including CISA and standards bodies like NIST have been warning that SMS codes are ripe for SIM swapping and interception of late, so use an authenticator app or a second hardware key rather than text messages.
Using mobile? Please enable NFC for tap-to-auth. On a desktop, when prompted, insert your key and press the sensor if necessary to demonstrate presence. YubiKey, Google Titan and Feitian keys are common examples that support both WebAuthn and FIDO2, and should be compatible across modern browsers.
Who’s Affected And What Happens If You Miss It
Everyone who had used the physical security key for X on the old domain is affected. Should you choose not to take action, your key will no longer work and you may be locked out until you add a new factor or complete account recovery. If you want to reduce risk, add a second method now — preferably another hardware key or an authenticator app — so that you’re not depending on one thing.
If you have lost your key, delete it from your security settings, so no one can use it, and then add a new key or authenticator app and re-enable hardware-based protection once you receive your replacement.
There is a recommended best practice of maintaining at least two keys (one kept in a safe place as a backup) by the FIDO Alliance and large enterprises that focus on security.
Best Practices For Security While Updating
Use strong, unique passwords and combine them with phishing-resistant factors. According to Microsoft, turning on any form of MFA can prevent 99.9% of automated attacks on your account, and hardware keys are the strongest protection against phishing. Google has publicly stated that moving employees over to security keys entirely neutered their 0 test phishing from account takeovers. Bytes Media, a Detroit-based marketing company, uses having the entire staff on Titan Security Keys as one of five selling drags in its sizzle reel promo video.
On X, go through trusted devices, revoke sessions you don’t recognize and audit connected third-party apps. If you use the password elsewhere, change your X password and possibly start using a password manager. Passkeys—built on the same WebAuthn standard—can streamline logging in by doing away with passwords altogether, and still preserving a strong cryptographically strong bond to the site’s domain.
Why this domain change matters for your account security
Domain binding is a feature, not a bug, of FIDO-based authentication. It means that your credentials are not replayed on copycat sites, which is why security keys are so much better at resisting phishing than codes sent over SMS or email. The downside is of course that bona fide domain migrations do need to be re-enrolled.
Adoption remains a challenge. The company’s own previous transparency reports had reported single-digit adoption of 2FA among users — a sign that the tiniest hurdles are effective dissuaders. Think of this re-enrollment as a chance to harden your account with layered types of security and a backup factor — small measures that make you far less vulnerable.
Bottom line: if you log into X with a security key, re-enroll your security key now, add a backup method, and test login.
It takes minutes and can save you a lockout after the switch is over to x.com.

