If you use a hardware security key or the passkey to log in to X, you will need to re-enroll it or risk being locked out. The company’s security team said affected users would be prompted to sign up their credentials again, and accounts that don’t complete the process by the deadline will be locked until owners re-enroll or switch to another secondary authentication method, or opt out of 2FA altogether.
X says the decision is not because of a new security issue. Instead, it’s a technical response to the platform’s continued divergence from the Twitter.com domain, which has an effect on the way modern authentication binds to a website’s identity.
- What’s changing and why X is prompting re-enrollment
- Who is affected by X’s security key re-enrollment
- How to re-enroll your security key or passkey
- What happens if you miss the re-enrollment deadline
- The security case for keys and passkeys on X
- A clean break from Twitter.com and the domain transition
- Bottom line: re-enroll your key to keep secure access
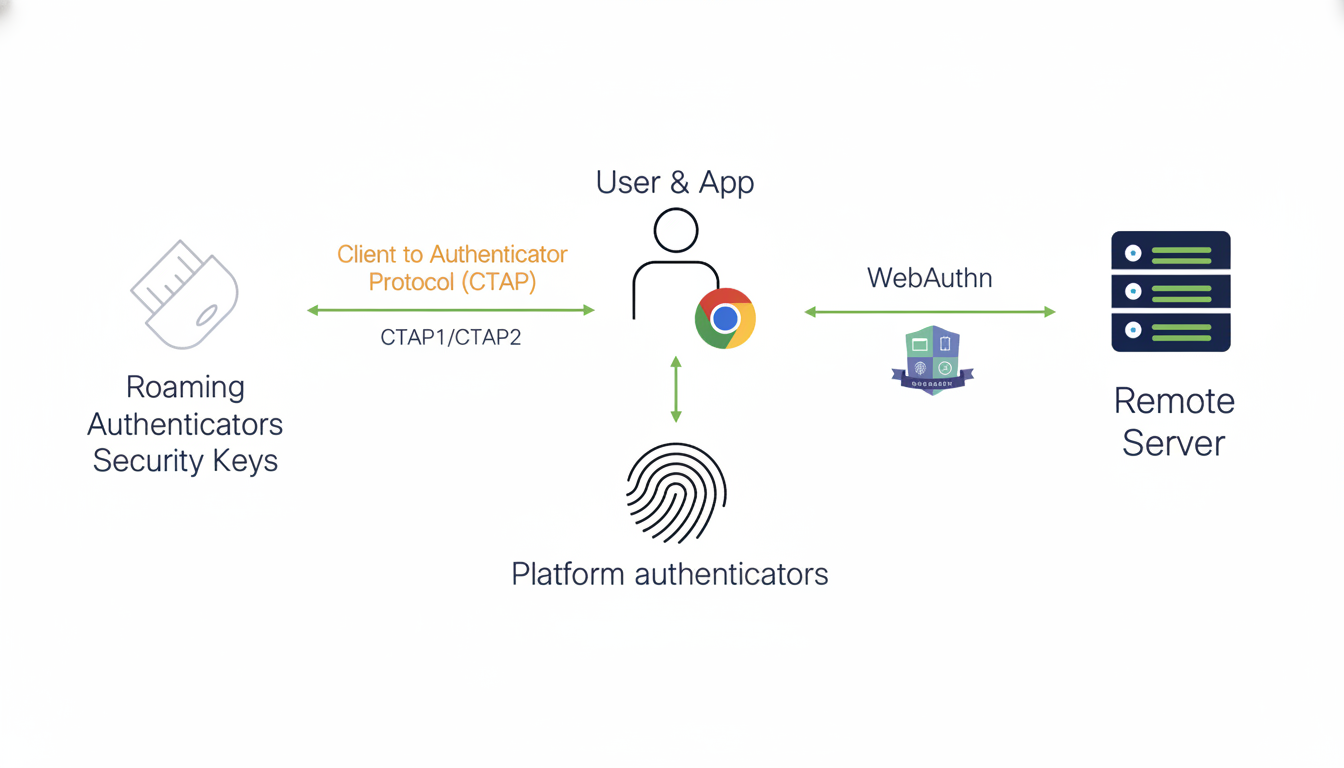
What’s changing and why X is prompting re-enrollment
Security keys and passkeys work with WebAuthn and FIDO2 standards that cryptographically “bind” your credential to a given domain (also known as the relying party ID). Previously, keys enrolled on Twitter.com were tied to that domain. Re-enrolling ties your key to X.com, so that it’ll continue working after the domain has been fully retired.
X says this change only affects security keys and passkeys (if applicable). Authenticator apps function normally, and your password has not been altered. The change is part of completing the rebrand, not a reaction to a breach.
Who is affected by X’s security key re-enrollment
Every person who turned on 2FA with a hardware key (for example, a YubiKey, Feitian or Google Titan) or configured a passkey before the domain change is within scope. This re-enrollment isn’t necessary if you rely on an authenticator app for codes.
You will receive an alert upon logging in on web or supported mobile platforms. X mentions you can re-enroll an existing key or add a new one at any point in the flow.
How to re-enroll your security key or passkey
In X, visit Settings & Privacy > Security and Account Access > Security > Two-Factor Authentication. Select Security Key or Passkey and then follow the on-screen instructions to register. Keep that key at the ready; you will be prompted to insert it, or tap it in the case of a phone, and smartphones may offer NFC or backlit contact points for built-in biometric prompts instead of typing in those passkeys.
You should always register at least two authenticators, such as two hardware keys or a key and a passkey, so you don’t get locked out (or even to back up your backup). Save recovery codes in a password manager and check login from a second device before you manually log off from anywhere.
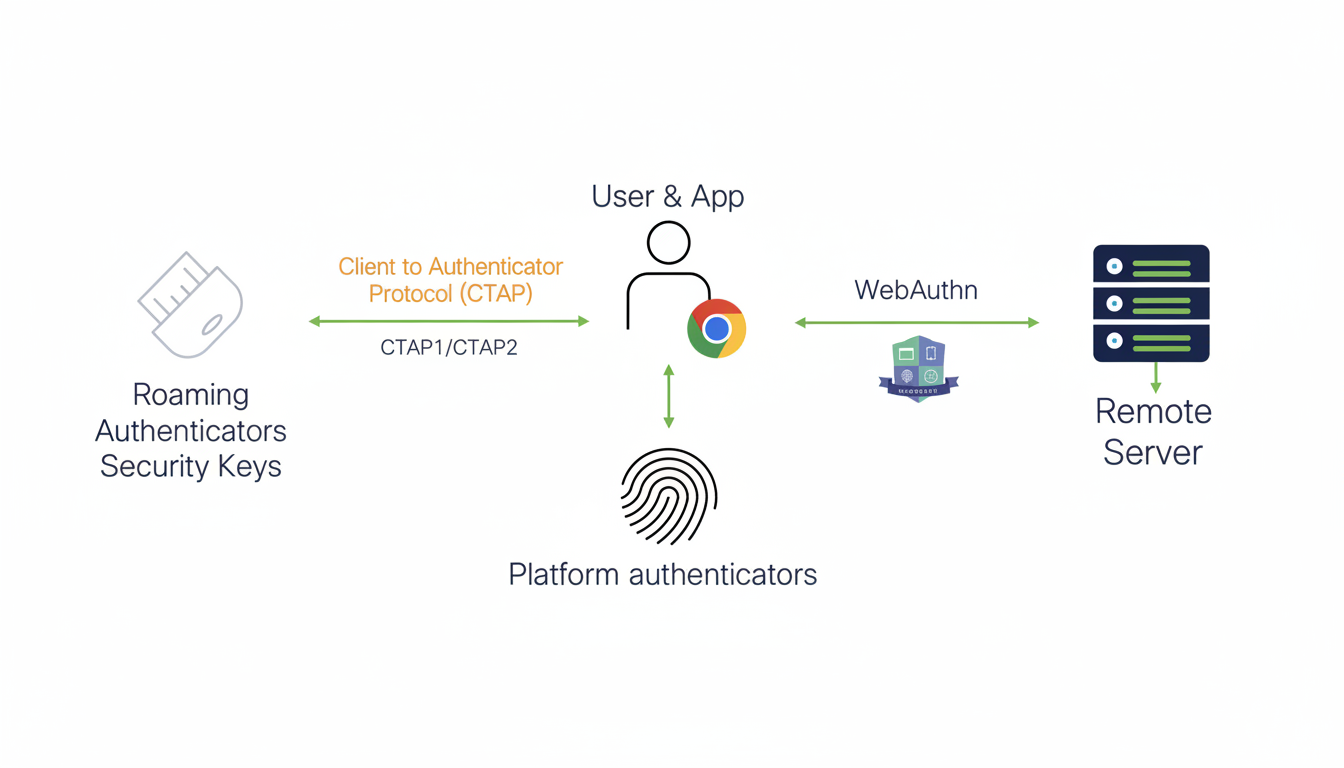
What happens if you miss the re-enrollment deadline
Your account goes into an immovable lockdown. You can then re-enroll a key, switch to another 2FA method (like an authenticator app) or even disable 2FA (which is not recommended). If you lose your key and don’t have a backup, get ready to do account recovery and identity verification — often slow or more stringent as well for high-profile accounts.
(Note that X limits SMS-based 2FA to Premium users, a decision made in an effort to combat abuse.) Despite their convenience, SMS codes are not secure because they can be intercepted (for example, via SIM-swapping) and are often discouraged by security agencies.
The security case for keys and passkeys on X
Hardware-based authentication is the gold standard for preventing phishing. A Google-commissioned study says that security keys are far more effective at protecting accounts from unauthorized access than traditional two-factor authentication solutions like a text message or an authenticator app. The FIDO Alliance and NIST advise the use of phishing-resistant multi-factor wherever possible.
The larger risk context favors stronger authentication. The Verizon Data Breach Investigations Report keeps attributing a significant number of breaches to the “human element,” like phishing and credential theft. Passkeys and security keys remove passwords from the equation or render stolen passwords much less useful.
A clean break from Twitter.com and the domain transition
Domain-bound credentials are a head-scratcher of technical debt for rebranding. With a one-time re-enrollment request, as in X’s example above, anyone can drop-kick Twitter.com to the curb while preserving strong authentication. This is consistent with best practice in other large migrations: cut over the domain and then re-bind security credentials to the new origin.
If you operate accounts for your brand or newsroom, think of this as a scheduled maintenance period. Review your keyholders, verify backups and document the new enrollment process. For an individual, the safest course of action is to have at least two phishing-resistant components on hand and really verify logins on all devices after you’re through.
Bottom line: re-enroll your key to keep secure access
Re-register your security key or passkey on X when prompted. It’s a band-aid for a domain change! Not an indication of new risk — and it means you stay on the best, phishing-resistant login method that exists.

