If you work with telecom networks, you’ll hear the term subsystem number often. In Signalling System No. 7 (SS7), a subsystem number (SSN) is a small numeric identifier that tells the network which application inside a node should receive a signaling message—such as an HLR, VLR, MSC, SMSC, or other service platform. Think of it like an apartment number inside a large building: the building is the network node (addressed by a point code) and the apartment is the application (addressed by a subsystem number). Together, they make sure the message reaches the exact software function that must process it.
What is a subsystem number?
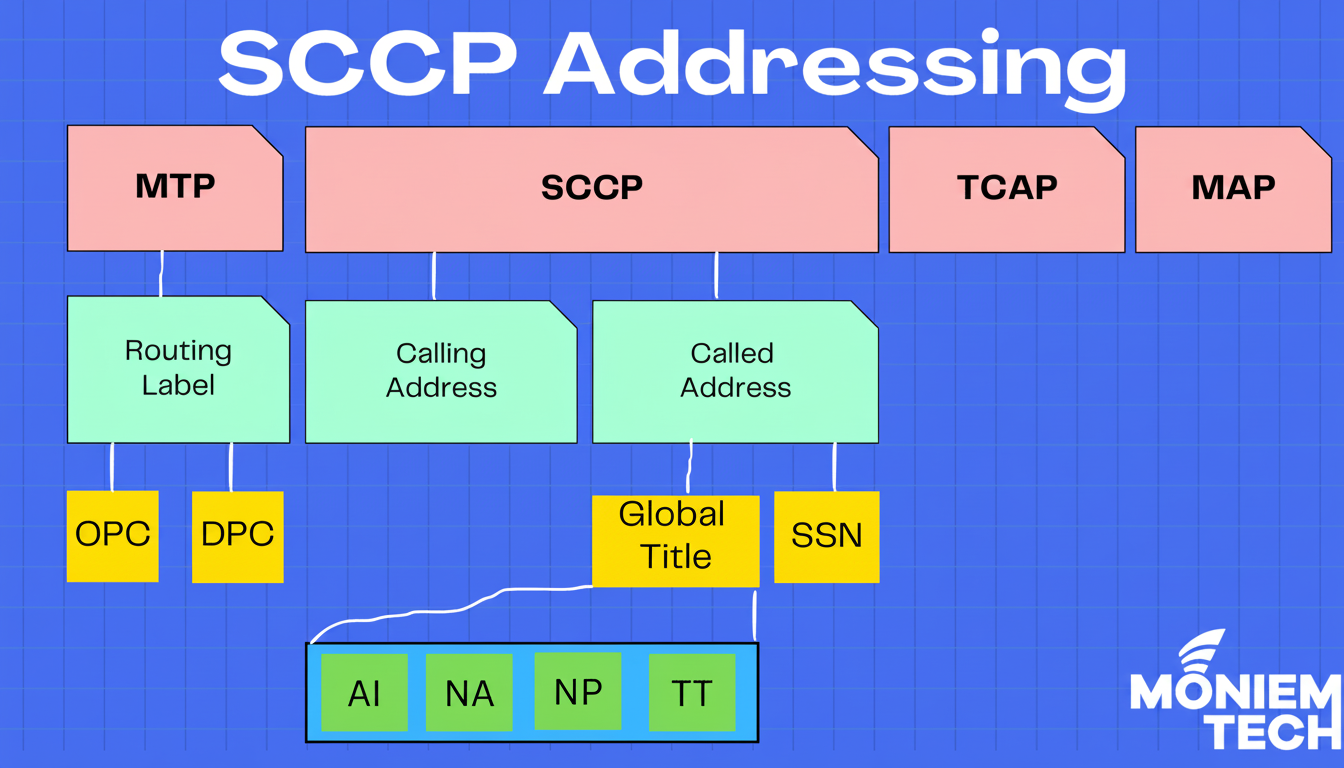
Within the SS7 stack, the Signalling Connection Control Part (SCCP) provides flexible addressing and routing beyond lower layers. SCCP uses:
- What is a subsystem number?
- Why subsystem numbers exist
- Common SSN assignments (typical examples)
- How routing with SSN actually works (simple example)
- The standards behind subsystem numbers
- SSN in the age of SIGTRAN (SS7 over IP)
- Typical troubleshooting questions (and where to look)
- Best practices when working with subsystem numbers
- Frequently asked questions
- Key takeaways

- Point code (PC): identifies the node (the box or logical node in the network).
- Subsystem number (SSN): identifies the application inside that node.
When a message arrives, SCCP looks at the destination PC (which node) and the SSN (which application on that node) and delivers the message to the correct software process. This keeps many services running on the same node from getting mixed up.
Some networks also use global title (GT) routing. GT routing is like a directory service: the network can route on a dialable number (for example, an MSISDN) or an IMSI, translate it, and produce a final PC + SSN pair. That way you don’t need to hard-code every destination on every switch.
Why subsystem numbers exist
Modern telecom nodes are multi-service. A mobile core element can host mobility management, authentication, SMS delivery, prepaid charging triggers, and more—all on one platform. The SSN cleanly separates those applications so a signaling message lands in the right place every time. Without SSNs, you could reach the node but still miss the exact function you needed.
Common SSN assignments (typical examples)
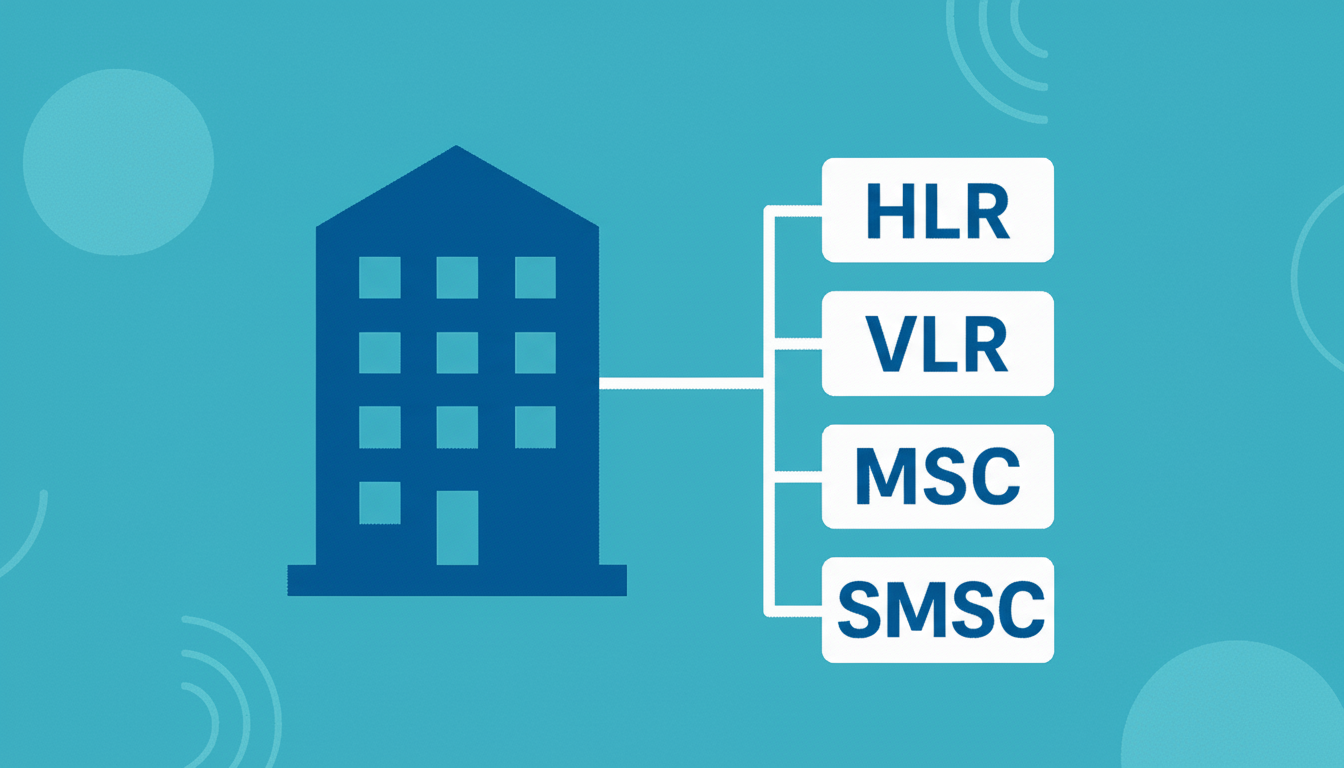
Standards bodies and industry profiles define well-known SSNs so different networks can interoperate. Exact assignments can vary by country or operator, but the following are widely recognized in mobile networks:
- 6 — HLR (Home Location Register)
- 7 — VLR (Visitor Location Register)
- 8 — MSC (Mobile Switching Centre) for MAP services
- 9 — EIR (Equipment Identity Register)
Other services (like SMSC, CAMEL/IN, location services, or packet-core interfaces) often use national-range SSNs chosen by the operator’s profile. Always check the local numbering plan or your interconnect specification when you deploy or interconnect services.
How routing with SSN actually works (simple example)
- A handset action, such as a location update or sending an SMS, triggers a MAP (Mobile Application Part) message.
- The network may apply global title translation to convert a dialable number or IMSI into a point code + SSN destination.
- The message is then sent via SCCP to the node’s point code and delivered to the application identified by the SSN, such as HLR (SSN 6) or VLR (SSN 7).
This two-part address—PC for the node, SSN for the application—ensures the message reaches the right software module even when many modules live on the same system.
The standards behind subsystem numbers
The rules for SCCP addressing, including SSNs, are defined in the ITU-T Q.713 series and related SCCP specifications. Mobile-specific behavior (such as MAP use of SCCP) is profiled by 3GPP and regional standards bodies. Vendors then implement those profiles in their equipment and documentation. While you don’t need to memorize the specs to operate a network, it helps to know where the behavior comes from and why certain values are “well-known.”
SSN in the age of SIGTRAN (SS7 over IP)
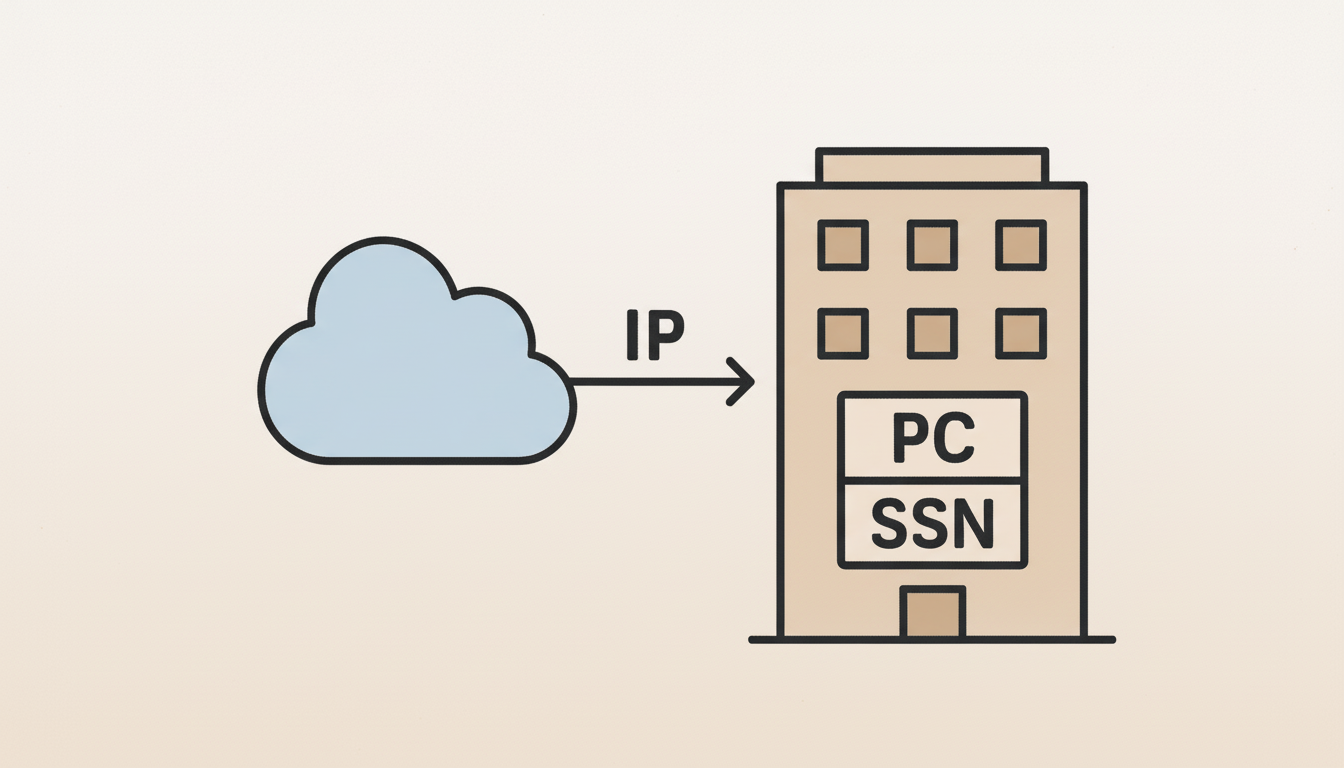
Classic SS7 ran over TDM links. Today, many operators carry SS7 messages over IP using SIGTRAN—most commonly the M3UA adaptation layer on top of SCTP. The move to IP transport does not change the addressing model. You still route to a point code and deliver to an SSN on the destination node (or to an Application Server that represents the node). In other words, PC + SSN remains the logical address, even when the physical transport is IP.
Typical troubleshooting questions (and where to look)
“I can reach the node, but the application doesn’t respond.”
Confirm that the destination SSN is active on the target node and that SCCP management has not blocked it. Mis-matched or disabled SSNs cause silent drops and management alarms.
“Global title translation works for calls but not for SMS.”
SMS paths sometimes use different GT tables or target different SSNs (for example, an SMSC service). Check that your GT rules translate to the correct PC + SSN pair for messaging.
“Which SSN should we use for CAMEL/IN triggers?”
CAMEL/IN services typically use national-range SSNs defined in the operator profile. Confirm the exact value with your interconnect or internal deployment guide before you turn up the service.
“Do we need a unique SSN for every instance?”
In large networks, it’s common to reuse the same SSN for the same type of application on multiple nodes and differentiate by point code (each node has its own PC). Some operators also split services by SSN to simplify routing and troubleshooting; your design guide will specify the approach.
Best practices when working with subsystem numbers
- Follow the standard ranges. Use well-known SSNs for inter-operator interfaces and national ranges inside your own PLMN to avoid conflicts.
- Document mappings. Keep a single source of truth for GT → PC + SSN mappings. Update it whenever you add or retire services.
- Monitor SCCP management. If a subsystem goes out of service, traffic can fail or reroute. Watch alarms, counters, and OOS/IS changes.
- Test before cutover. Use tracing tools to verify that each service receives traffic on the expected PC + SSN, and that responses come back on the same pair.
- Plan for growth. As you add features (for example, number portability, location services, or fraud signaling), assign SSNs in a structured way so your routing remains clear and scalable.
- Mind interconnects. When peering with other operators, align on SSN usage and global title rules in your Interconnect Agreement to prevent translation loops or blackholes.
Frequently asked questions
No. The combination of point code + SSN identifies an application on a specific node. The same SSN can appear on many nodes.
They shouldn’t. One SSN should map to one application (or application group) on a node. If you co-host apps, give each its own SSN to keep routing and troubleshooting clean.
5G core signaling is mostly HTTP/2 over TLS with Service-Based Architecture (SBA), not SS7. But many 4G/3G/2G functions still exist in today’s networks, and interworking with legacy domains continues to rely on SS7 concepts like PC + SSN.
Key takeaways
- A subsystem number (SSN) identifies the application inside a node; combined with a point code, it directs SS7 signaling to the right destination.
- Common examples include HLR (6), VLR (7), MSC (8), and EIR (9); other services often use operator-specific national-range values.
- Global title translation maps dialable numbers or IMSIs to PC + SSN and keeps routing scalable.
- The move from TDM to SIGTRAN does not change the addressing model—PC + SSN still rules.
With these basics, you can read traces, configure routes, and debug signaling issues with more confidence. And when someone asks for the “subsystem number,” you’ll know they’re referring to the specific application inside the node—not just the node itself.

