A browser marketed as privacy-first is under fire after independent researchers said it behaves like malware. A joint investigation reviewed by a major technology magazine, with findings from cybersecurity firm Infoblox and the United Nations Office on Drugs and Crime, alleges the Universe Browser secretly installs components, reroutes traffic through servers in China, and tampers with user protections.
What Investigators Found About Universe Browser Behavior
According to researchers, Universe Browser exhibits traits more common to surveillanceware than a consumer web app. The software reportedly initiates covert connections to external infrastructure, modifies device settings without transparency, and implements features that resemble keylogging by monitoring user input fields. It also disables routine browser safeguards, including right-click menus and developer tools, limiting a user’s ability to inspect or control what the app is doing.
- What Investigators Found About Universe Browser Behavior
- Distribution Through Gambling Networks in Southeast Asia
- Why It Matters for Privacy and Online Safety Worldwide
- Signs of Trouble Users Can Spot in a Risky Browser
- What to Do Now to Protect Your Devices and Data
- The Bottom Line on the Risky Universe Browser Allegations
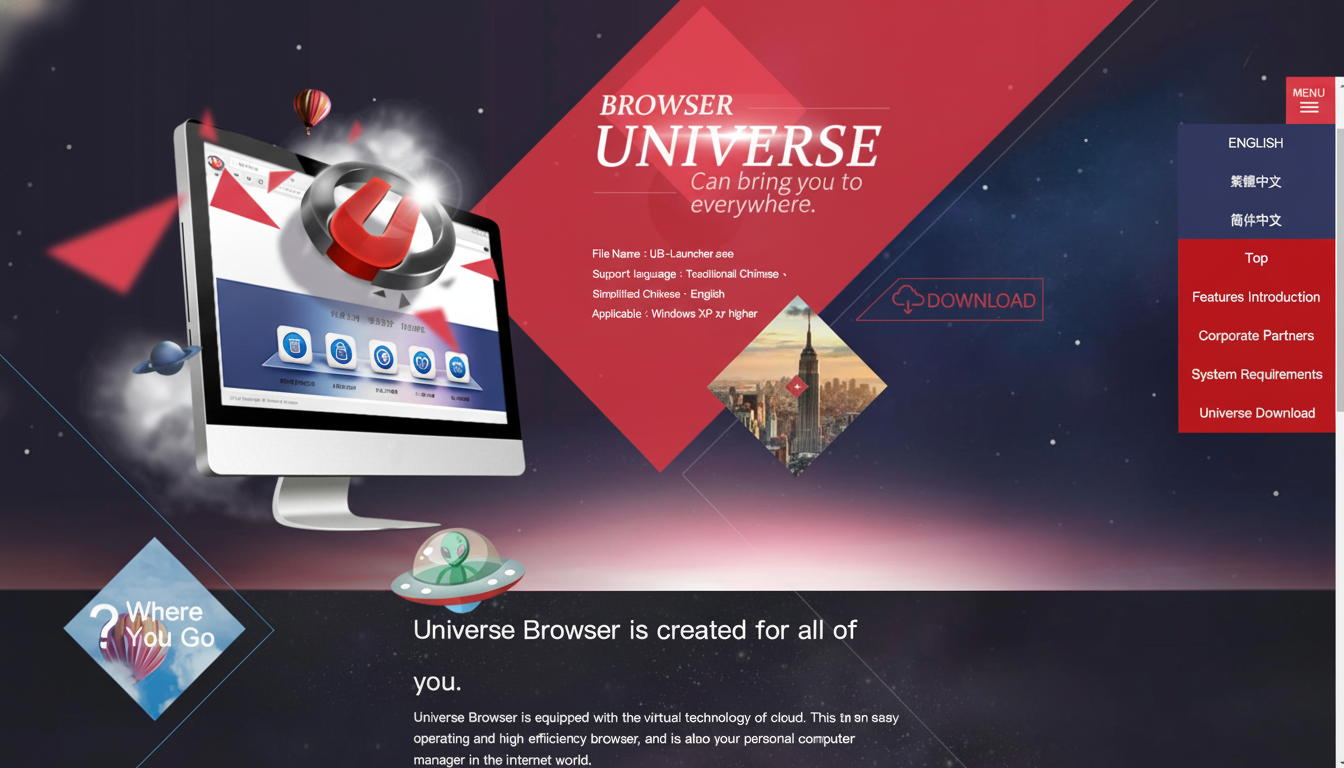
Infoblox’s analysis indicates the browser funnels network traffic through servers in China, raising concerns about cross-border data exposure and jurisdictional access. While the researchers stopped short of asserting definitive malicious intent, they argue the architecture is primed for abuse, enabling operators to profile users, siphon credentials, and monitor behavior at scale.
Distribution Through Gambling Networks in Southeast Asia
The app’s growth appears tied to illegal online gambling ecosystems in Southeast Asia, where it has reportedly been downloaded millions of times. Investigators say Universe Browser is promoted on casino and betting sites as a “fast” and “secure” way to bypass local restrictions. The Windows and iOS versions are available directly from these sites, and on Android the app is offered only via sideloaded APKs rather than through the official app store.
Security teams have long warned that app distribution outside trusted stores carries elevated risk. Annual mobile threat reviews consistently show a higher incidence of harmful apps installed via sideloading compared with software vetted through official marketplaces. In this case, the browser’s packaging and marketing as a safe alternative likely reduced user skepticism while masking risky behavior in the background.
Why It Matters for Privacy and Online Safety Worldwide
Browsers sit at the center of digital life, with access to passwords, session cookies, financial accounts, and identity data. A browser that captures keystrokes or manipulates traffic can undermine multi-factor authentication, intercept online banking sessions, and exfiltrate sensitive information. Infoblox warns that a tool like this would be ideal for identifying high-value gamblers and pivoting to deeper compromise of their devices and accounts.
The alleged links to organized cybercrime heighten the stakes. UNODC has documented the growing sophistication of syndicates in the region, including the use of seemingly legitimate apps as delivery mechanisms for fraud, illicit gambling, and forced-labor scam operations. A browser that disables visibility and pushes traffic through opaque servers fits a pattern: wrap malicious capability in a glossy user experience that promises privacy, then monetize stolen data and access.
Signs of Trouble Users Can Spot in a Risky Browser
Several red flags highlighted by researchers are recognizable even without deep technical skills. If a browser disables right-click, blocks access to developer tools, or resists changes to default settings, treat that as suspicious. Unexpected background services, persistent connections to unknown domains, and requirements to install from unofficial sites are additional warning signs. Privacy tools should increase transparency and control—never reduce it.
What to Do Now to Protect Your Devices and Data
If you installed Universe Browser, security experts recommend removing it immediately, then running a reputable endpoint scan. Consider rotating passwords, revoking sessions for banking and email, and reviewing saved credentials in your password manager. On Android, review installation sources and disable “install unknown apps” for browsers or download managers you do not fully trust. On all platforms, audit proxy settings and root certificates in case the app modified network trust.
For future protection, stick to official app stores, scrutinize privacy claims, and favor browsers with transparent security documentation and independent audits. Enterprises should enforce application allowlists, monitor for unusual outbound traffic, and block known malicious domains at the DNS layer. If you operate in regions targeted by illegal gambling networks, consider additional safeguards such as endpoint detection and response and strict network egress controls.
The Bottom Line on the Risky Universe Browser Allegations
Researchers say Universe Browser blurs the line between privacy tool and surveillance platform, with behavior that looks and feels like malware. Until independent verification proves otherwise, users and organizations should treat it as a high-risk application—and a reminder that security is earned through verifiable design, not marketing slogans.

