Ransomware is losing its most potent weapon: the ransom. As victims increasingly refuse to wire money to their attackers, the goal of attacks has changed. Instead of freezing operations with encryption, they steal data first and use exposure as their primary weapon.
Why Are Ransomware Payments Plunging Now?
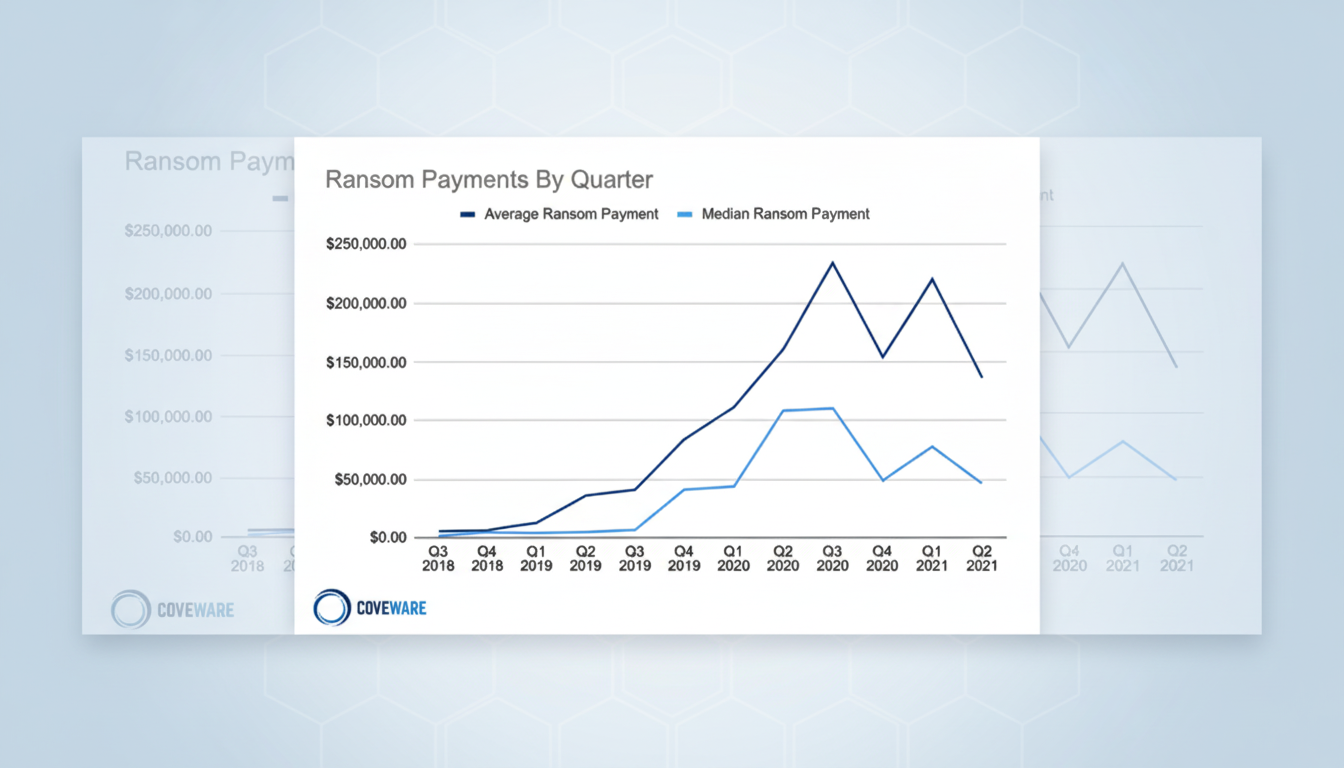
The dynamics of cyber extortion are shifting. The percentage of victims that pay has dropped to a near-historic low of 23%, from around 85% in 2019, according to Coveware’s recent data. And established backup strategies, pen-tested incident response plans, and firmer legal guidance are making it easier to say no.
Insurers, too, have upped the ante.
Policies increasingly are demanding that controls such as multifactor authentication, immutable backups, and segmentation be in place to get coverage, while picking apart ransom reimbursements. Sanctions risk hangs in the balance, too—groups fear running afoul of government regulations by paying entities linked to embargoed regions or established criminal networks.
Law enforcement has upped the pressure on the ecosystem with takedowns, waves of decryptor releases, and arrests. Together, these have exerted relentless pressure on attackers’ leverage and shrunk their sources of income.
Data Theft Is the Primary Payload in Attacks
With encryption alone no longer the action driver, exfiltration has become the tip of the spear. According to Coveware, data theft is occurring in 76% of MDR attacks they are tracking now in Q3 of 2025, sometimes the entire motive. Increasingly, groups bypass the locker malware and go straight to “pure extortion”: steal, threaten, release.
Public shaming sites, paste bins, and leak channels ratchet up the pressure. Attackers post samples, reach out to customers or partners, and count down the release of sensitive documents. The model reflects mass data theft campaigns such as those witnessed in the MOVEit exploitation spree, where a single vulnerability led to a long tail of disclosures and third-party fallout.
This change penalizes companies even if their backups are perfect. Restoration can bring systems back, but it cannot unspill a breach. Regulatory alerts, customer confidence, and potential lawsuits are the leverage—and that calculus is more difficult to game with technology alone.
The Ransomware Economy, by the Numbers in 2025
Coveware’s numbers by quarter show a consistent downward trend: 27% in Q1 2025, 26% in Q2, and 23% in Q3. The average payment fell to $376,941, a 66% quarter-over-quarter decline; the median amount fell 65% to $140,000. Big businesses are pushing back more uniformly, and when small and midsize companies do pay up, they’re paying far less.
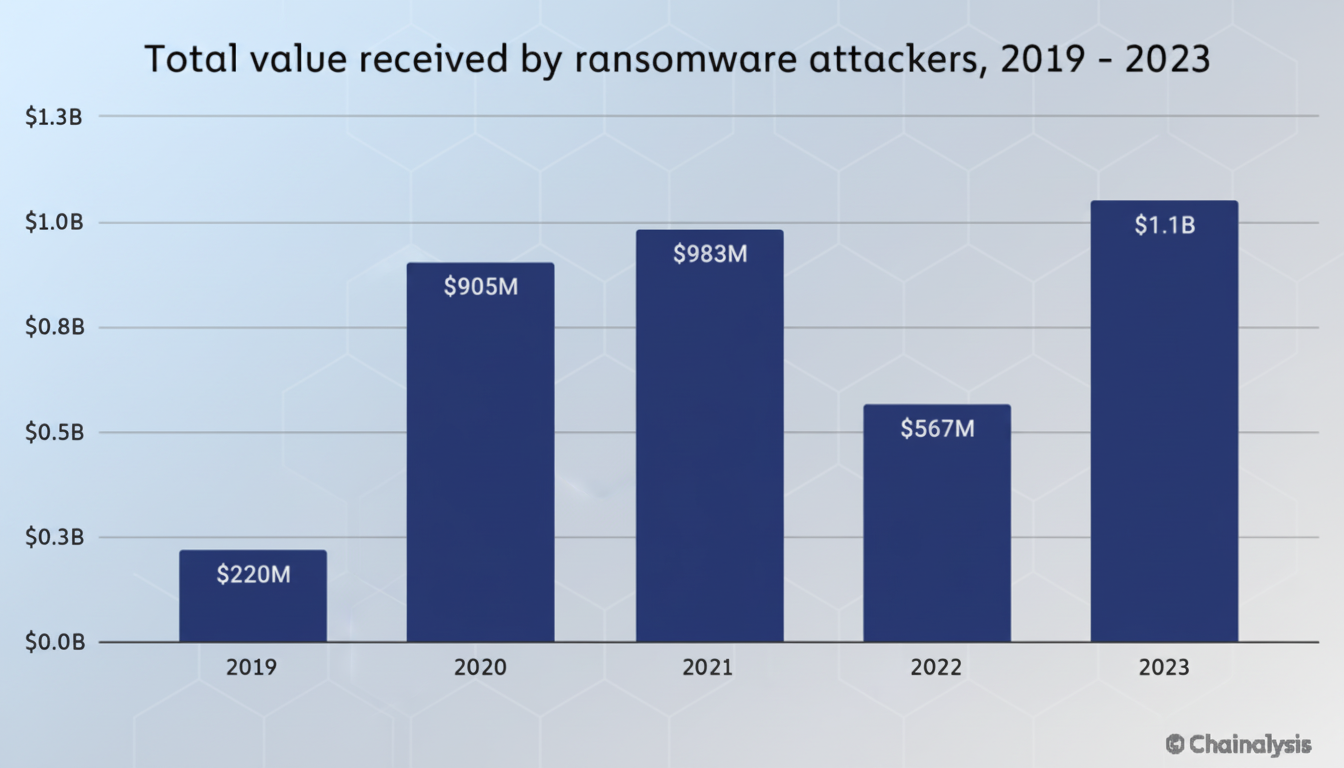
These trends are consistent with broader findings from companies like Chainalysis and Sophos: crime profits have become more erratic, on the rise even as defenders lock down better. Legal advice is now also beginning from a non-payment position, especially because the threat of your data being resold and re-extorted months down the line renders any kind of “guarantee” inoperable.
Two Criminal Models Emerge in Ransomware Operations
The ecosystem has bifurcated. On one side stands ransomware-as-a-service (RaaS), where affiliates rent code and are volume players who usually concentrate on the mid-market. Then there is the bespoke, high-touch type of intrusion against “white whale” enterprises; deep reconnaissance and tailored extortion may command more cash—if the victim breaks.
Other high-profile groups, such as LockBit and ALPHV, have alternated between both tactics by pursuing an aggressive outreach effort to affiliates alongside targeted attacks. Look for more hunting in data-rich environments and among third-party suppliers as criminals pursue higher margins from fewer payers.
How Defenders Should Respond to Data-Centric Extortion
Prepare for data-centric extortion. The basics still apply—MFA everywhere, patching, least privilege, segmentation, and phishing-resistant authentication—but the new game is egress. Observe for disproportionate outbound transfers, stage-to-exfil activities, and unusual compression. Use data loss prevention when possible and implement tight restrictions for privileged accounts and service tokens.
Just imagine the disclosure risk and rehearse the playbook. Leverage security operations with legal, communications, and privacy activities. Put your incident response team together ahead of time—incident responders, breach counsel, negotiation, and PR. Maintain immutable, offline backups and test restored backups under duress. Think about the downstream impact on customers and vendors, and draft templated notices that can quickly be updated.
Finally, be skeptical of allegations of extortion. Even if you do pay, there’s no contractual stipulation preventing resale/re-leak. Partner with LE and sector ISACs, write everything down, and make prioritized decisions. As the price goes down, attackers will look for softer targets or more valuable data. The companies that have the most egress hardening, least privilege, and regular response will fare best against the pivot.

