Three intersecting menaces are dominating the cybersecurity week: cryptocurrency handed off in industrial quantities to North Korea, a breach of identity checks at Discord that unlocked stacks of government IDs, and an extortionist group that says it possesses a billion records from dozens of household-name companies. Together they sketch a blunt picture of how financial crime, identity risk, and supply-chain compromise now all contribute to the same criminal economy.
The connective tissue is leverage. Crews of nation-states steal and launder value; consumer platforms centralize sensitive documents to enforce age checks; an attacker chains a small vendor to reach a big brand. Each such episode emphasizes a separate soft spot, yet the end result is always the same: money plundered and identities exposed, data as a bargaining chip.

How stolen cryptocurrency disappears into North Korea
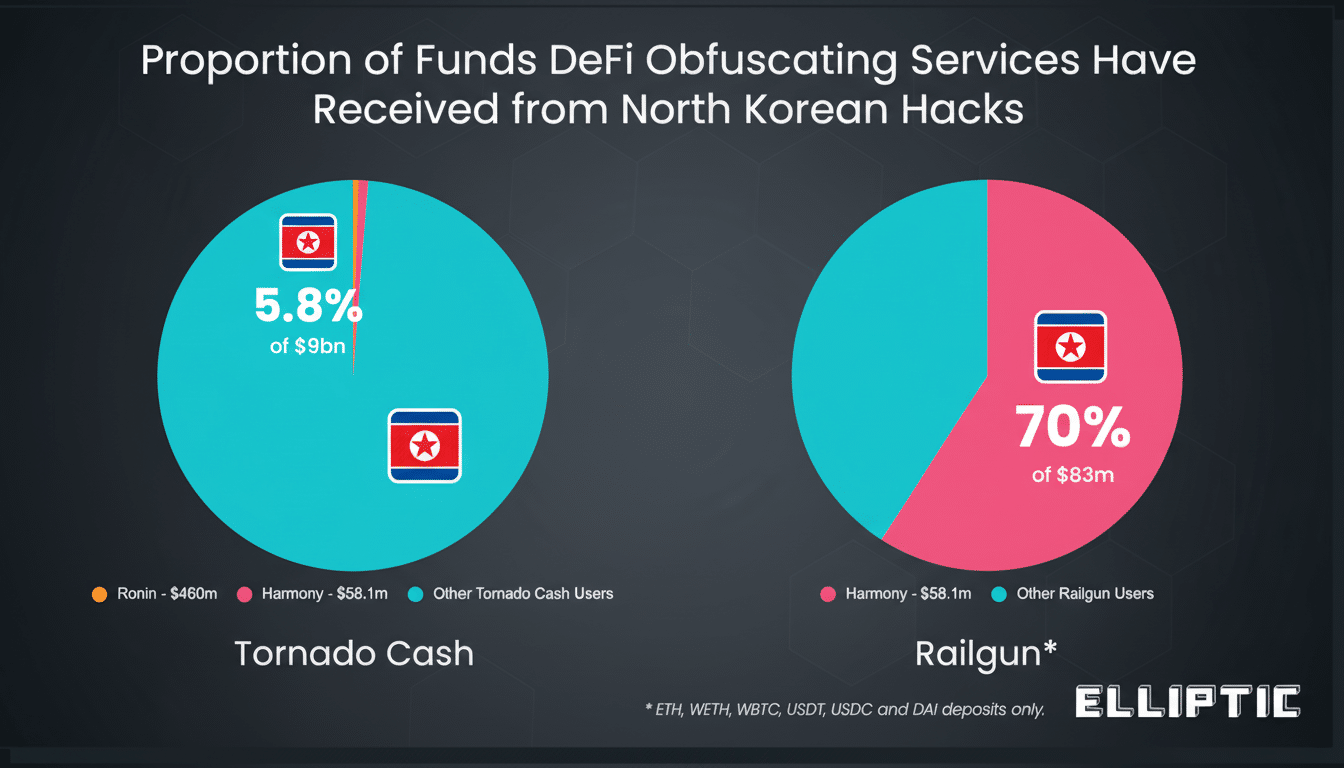
Blockchain-intelligence companies say DPRK-linked groups have already stolen more than $2 billion in cryptocurrency this year, building momentum after a record haul in 2022. The Lazarus cluster and related entities account for a most sizable share of that as they have shifted from exploiting DeFi protocols to aggressive social engineering of developers and exchange staff, which the FBI and international partners said in advisories on the “TraderTraitor” campaigns.
It’s not just how the money is stolen, but also how it moves. After high-profile mixers were sanctioned, bankers at Chainalysis and Elliptic traced DPRK laundering across cross-chain bridges, peel chains, instant exchangers, and over-the-counter brokers in permissive jurisdictions. Seizures and takedowns have meant constant adaptation — once one new mixer is thwarted, funds are being juggled through other privacy tools, liquidity pools, and nested services on networks, with grinding efforts around the clock.
The motivation is strategic. U.N. sanctions monitors have repeatedly connected crypto theft to the funding of weapons programs. This creates geopolitical pressure that causes attackers to shift their targets from larger exchanges, now heavily fortified, to smaller custodians, gaming projects, and wallet infrastructure — targets with weaker controls but that do hold liquid assets.
Discord ID leak spurs growing age-verification risks
Discord is facing a huge privacy backlash today after users discovered its “verified servers” system inadvertently requires that those servers collect all users’ activity and data, according to the terms of service (ToS). The problem is that this includes personal data on people who are not members of the verified server, and also government-issued IDs. “It’s come to our attention that we missed a privacy option in chat,” Discord founder and CEO Jason Citron tweeted Tuesday night. The company had received word on Tuesday from threat actors claiming they stole personal information for roughly 5.5 million unique users — or anyone who hadn’t enabled two-factor authentication when prompted by Discord itself — which included documents such as images of government IDs submitted for age verification. Discord disputes the scale of the incident, stating that it affected some 70,000 users who had appealed moderation decisions by uploading their IDs and that the leaked data was processed as part of a contract with a third-party service provider. Both of these figures highlight a single issue: identity cards have essentially become extremely valuable loot.
Age-verification schemes collect exactly the information that criminals most cherish — full names, birthdates, addresses, ID numbers, and even selfies.
If exfiltrated, those images can be used to seed synthetic identities, circumvent facial checks at other services, and power fraud that will last long after it is detected on a single platform. Privacy researchers have called for data minimization, more stringent vendor risk assessments, and clear deletion policies because the attack surface is no longer confined to core app infrastructure; it is every contractor and verification pipeline attached to that core.
The lesson is blunt for consumer platforms: treat your KYC and age-verification stores as though they were crown jewels.
That means putting them behind separate identity and encryption domains, enabling strict supplier audits, and using hardware-backed phishing-resistant authentication for all administrators with access to validation workflows.
Hackers claim to sequester more than one billion records
Meanwhile, a separate extortion wave is being carried out by a cybercriminal group claiming to have stolen more than 1 billion records from 39 companies and promising to leak the data if ransoms are not paid. Brands cited by the criminal gang include high-profile companies in entertainment, automotive, and fast food, with not all victims impacted yet proven. What’s certain is the path of attack: Hack a smaller vendor with privileged integrations, and pivot into high-value customer data.
This is classic island-hopping. Instead of pummeling the perimeter of a Fortune 500 company, attackers hit upon a niche support provider integrated into expansive Salesforce deployments, help-desk platforms, and analytics connectors. Once in, they steal API keys, session tokens, or data exports at the collection layer. It’s a playbook that incident responders have seen time and again following significant supply-chain breaches or, more recently, financially motivated campaigns involving the abuse of cloud data warehouses and third-party service accounts.
The stakes are larger than any one leak. Ransomware gangs are starting to pose triple threats — exfiltrating data, launching DDoS attacks, and now sowing mayhem on the dark web. Even without encrypted systems, exfiltrated customer records invite regulatory scrutiny, class actions, and brand damage — pressure that moves companies closer to paying out. Law firm and law enforcement officials continue to warn that ransom payments encourage repeat targeting and come with no guarantee of deletion.
The common thread connecting these three security cases
These are not isolated cases of randomness; they are symptoms of the same structural exposure. Value today pools in only a few places: programmable money, identity vaults, and vendor-mediated data pipes. Adversaries follow the leverage — liquidity pools, document vaults, and supply-chain integrations — because each of these has monetization paths after a given breach.
What security leaders need to prioritize right now
- First, harden identity. Require MFA for sensitive accounts such as administrators and vendors with phishing-resistant MFA, like FIDO2; use just-in-time administrative access; and use behavioral controls to detect token theft or session hijacking. Keep the storage of age validation and KYC data in a separate location, encrypted on a field-level basis, and require retention at one end with an automatic deletion scheme.
- Second, contain vendor blast radius. Demand least-privilege scopes on API integrations, rotate credentials constantly, and isolate third-party access into separate tenants or projects. Move to continuous third-party risk monitoring versus once-a-year questionnaires, validate claims with evidence such as SBOMs (Software Bill of Materials), pen-test attestation, and control mapping to frameworks like NIST CSF or ISO 27001.
- Third, prepare for crypto-targeted intrusion. If you’re a wallet or smart contract operator, turn on real-time anomaly detection for token flows, keep your hot wallet and warm or cold storage separate from each other, make certain to require multi-party custody of large transfers of money common between them all, as well as run red-team tests around developer social engineering and key theft. Partner with blockchain analytics companies to rapidly track and seize stolen funds.
- Finally, share signals early. Working with national cyber agencies and industry ISACs means identifying the vendor footholds and laundering routes before they can scale. The latest takedowns indicate that when defenders — in this case, platforms, analytics firms, and investigators — work together, they can disrupt adversarial logistics even though the threat will mutate.
This week’s triad of events is a reminder that the largest threats increasingly live upstream, or in parallel, from any one login screen. Secure the money, secure the identity vaults, secure the pipes between you and your suppliers — or someone will do it for you.

