Apple’s iPhone 17 is here with a fresh security layer that takes direct aim at mercenary spyware and state-backed surveillance. The feature, Memory Integrity Enforcement (MIE), has been implemented to subvert the memory corruption trickery utilized by most zero-click iPhone exploits—but requiring users to adjust none of their settings.
For MIE to be most useful, it would be unwise to protect one from the precision attacks tied to commercial spyware vendors, nor everyday adware, nor run-of-the-mill phishing scams.
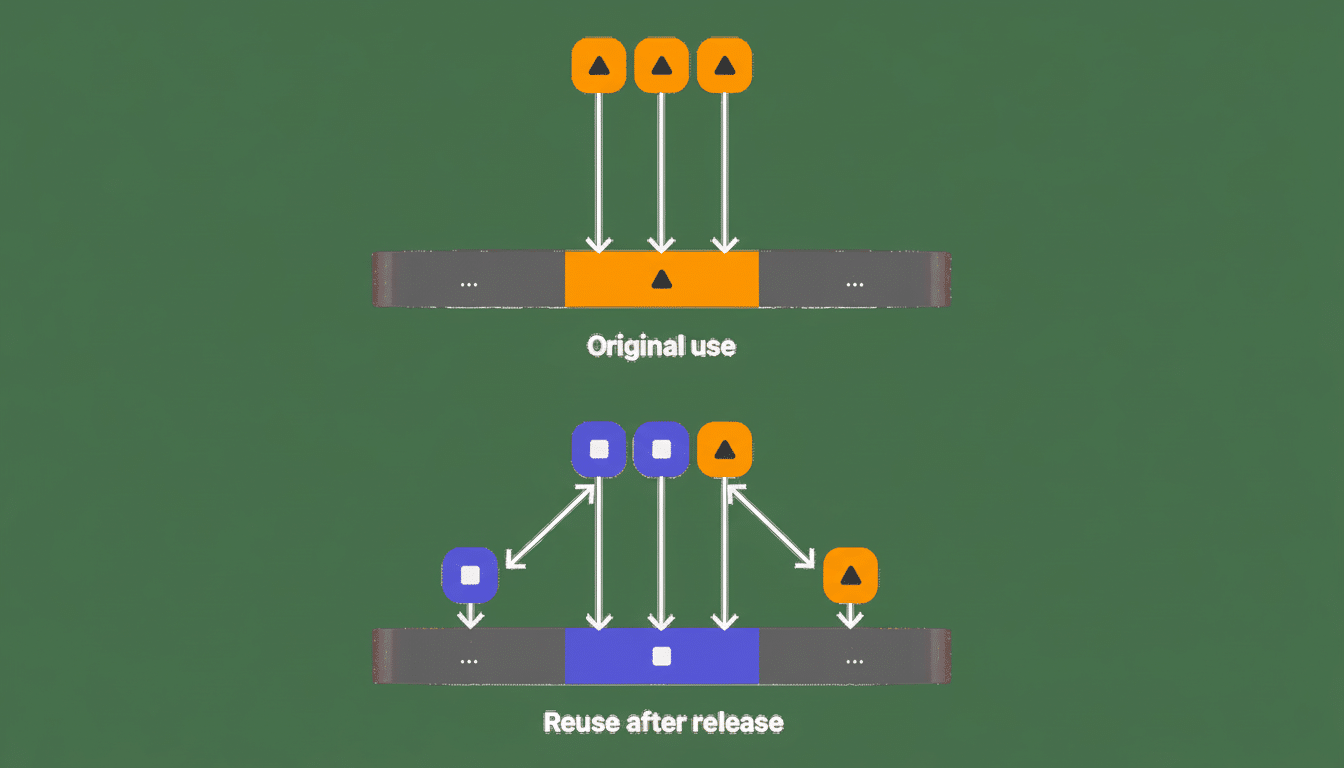
Apple’s objective is to ensure that these high-end exploit chains fail far more often and cost far more to develop.
What MIE actually does
MIE provides all the time memory safety check across the iOS kernel and more than 70 of, the core processes of iOS that attackers are most interested in compromising. It does this by tagging segments of memory and then checking those tags on use, breaking all common privesc attacks including use-after-free, buffer overflows, and type confusion — which are patterns commonly found in iOS zero click research.
Think of them as real-time tripwires that are planted deep in the operating system’s memory map. If malicious code attempts to access memory incorrectly, the tag checks can catch the attempt and stop the attack in its tracks before the machine gets fully compromised.
This is of particular importance to cases like the Pegasus operations revealed by Citizen Lab and Amnesty Tech, where image parsers or messaging services, or font libraries were exploited through subtle memory issues. MIE is constructed specifically to mitigate those same types of flaws—from 4’10’’ on up without the user ever noticing the change in elevation.
Powered by Arm EMTE, optimized for iPhone
Structurally, MIE is built around the Enhanced Memory Tagging Extension (EMTE) a hardware-assisted capability developed jointly by Apple and Arm. EMTE improves the previously proposed Arm Memory Tagging Extension from 2019 by shoring up patches and by adding hardening features such as tag confidentiality and secure typed allocators.
In theory, memory-tagging isn’t a new concept, but Apple’s implementation stands out because it’s turned on by default across key system components, rather than being a for-developers-only or test-mode feature. That default-on stance is important: the attackers cannot assume that they will be dealing with devices that have this protection turned off.
Context helps here. Memory safety has long been cited by Google’s Project Zero as the source of most of the highest-severity vulnerabilities and the majority of in-the-wild attacks; the team has historically found that about two-thirds of exploited bugs involve memory corruption. The Android security team also announced a substantial decline in memory safety bugs as a larger portion of system components transitioned to memory-safe languages, highlighting the positive effects of systemic defenses. The same playbook applies to MIE, only the hardware-enforced barrier is now the edge.
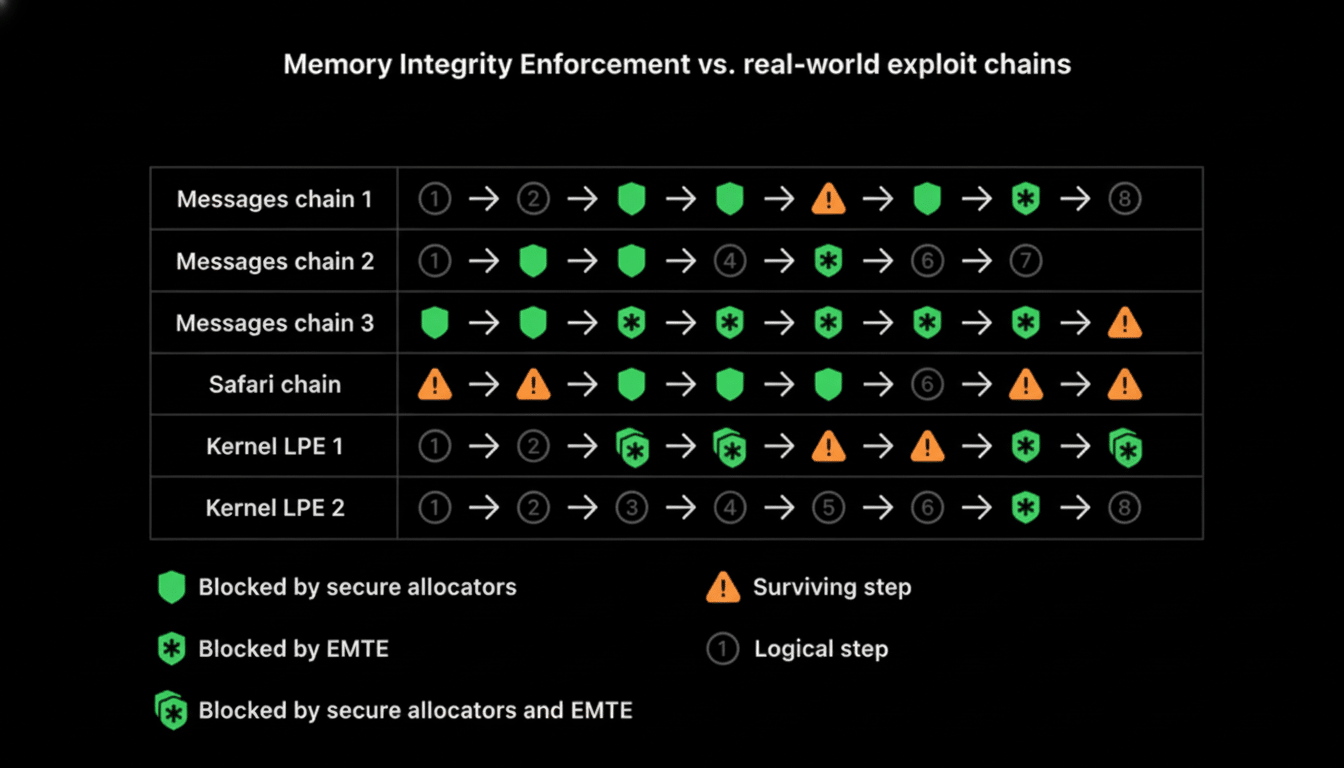
Why this is relevant to the economics of spyware
Seven-figure sums have been paid by commercial exploit brokers for dependable iOS zero-click chains, and investigations into mercenary spyware have revealed budgets that can reach into the millions as a capability investment. By shattering the most reliable exploitation primitives, MIE compels attackers to build longer chains, resort to rarer bug classes, or burn expensive logic bugs—each alternative adding days to weeks to development, risk, and cost.
It is not a silver bullet. Advanced adversaries can switch to non-memory bugs, baseband targets, partial sandbox escapes, or social engineering. But the overall impact is significant: fewer turnkey exploits, more misses, and a higher likelihood that attacks are detected or patched before they can be broadly weaponized.
— (For defenders, that extra friction is also invaluable.) It adds to other measures like iMessage BlastDoor sandboxing, swift security actions and Lockdown Mode—features that have already neutralized several high-profile campaigns described by Citizen Lab and Google’s Threat Analysis Group.
What users and organizations will see
There’s nothing to toggle. MIE operates quietly behind the scenes, and it doesn’t change the way apps are installed or used. Developers shouldn’t even need to rewrite software to be covered, as the protections come down at the OS and the allocator level. Organizations have a baseline device that’s more resilient, yet doesn’t require management overhead.
Performance is always important with always-on checks. Apple maintains that it developed the feature to have a low overhead, and the fact it ships enabled across important system processes implies the hit is contained. When it comes to security, a practice of default-on — without destroying user experience — is often what separates theory from real-world practices.
It’s also fair to mention outside skepticism. The GrapheneOS project and other security researchers have highlighted limitations in memory tagging schemes and warned against overhyping their guarantees. That is a good criticism: defenses like MIE work best when used in conjunction with rapid patching, attack surface reduction, memory-safe languages, and strong sandboxing. Apple’s stack now meets more of those.
Bottom line: fewer backroom deals and broken promises
The iPhone 17’s Memory Integrity Enforcement will not stop spyware, but it changes the game.
In making hardware-backed memory tagging a default defense for the most security-sensitive portions of iOS, Apple is taking aim at the core reason behind so many of the iPhone’s worst bugs. For high-risk users — and everyone who benefits from the consequences of increased attacker costs — it’s a good step forward.

