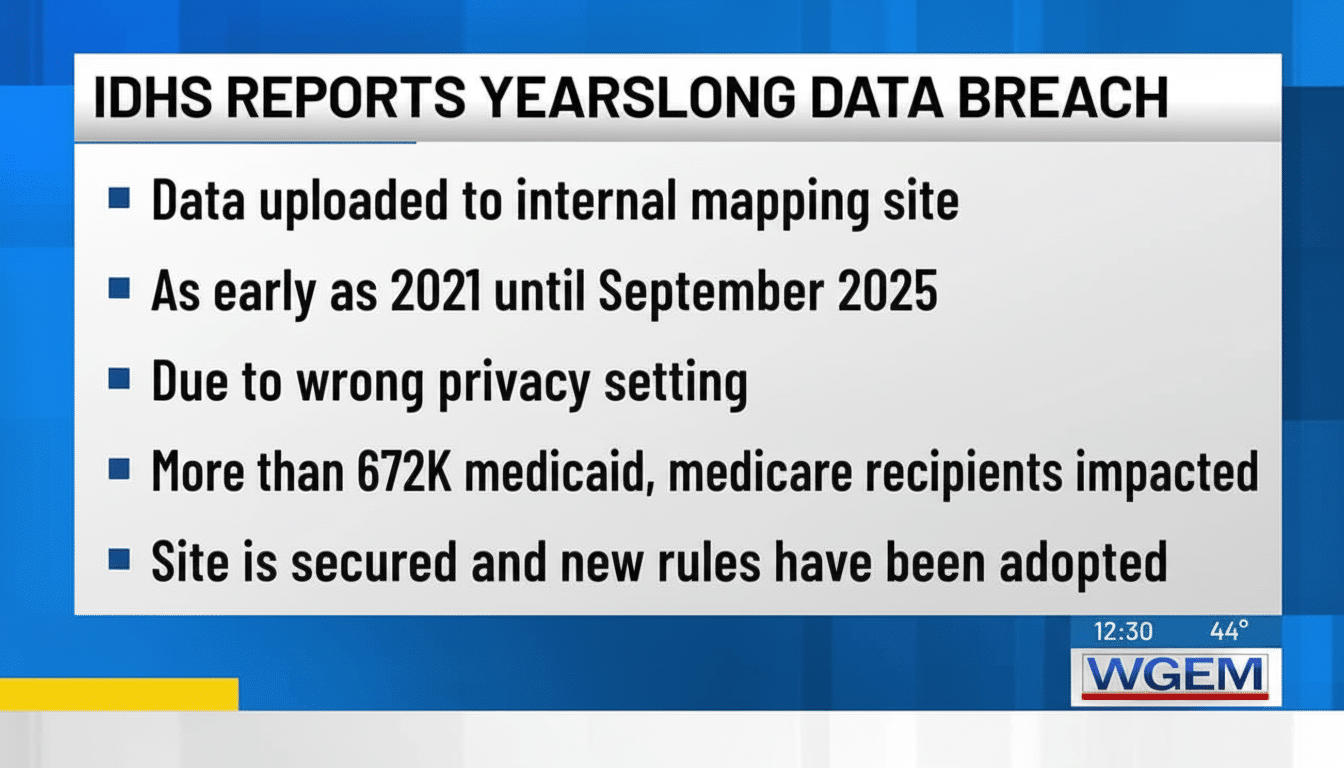
Illinois’ human services agency has acknowledged a computer processing error that stretched for nearly a decade, resulting in an internal mapping website that was intended only for state workers instead being publicly available and exposing the personal information of more than 700,000 people. The Illinois Department of Human Services (IDHS) announced that the information was pulled from tools administrative staff used to manage benefits and services — and that it cannot tell whether outside observers saw or downloaded any of the exposed data.
What Information Was Visible On The Public Mapping Site
IDHS said the exposure impacted two categories. Among the biggest was one with 672,616 participants enrolled in Medicaid and in the Medicare Savings Program. For residents depicted in these maps, the versions that were publicly available included addresses and case numbers, as well as some demographic information but not names. Another 32,401 consumers of the Division of Rehabilitation Services (DRS) had names, addresses, case status, service delivery group and other program information visible.
- What Information Was Visible On The Public Mapping Site
- How An Internal Map Tool Was Mistakenly Made Public
- Potential Harms And Who Is Most At Risk From Exposure
- Agency Response, Regulatory Obligations And Accountability
- Guidance For Affected Residents To Protect Themselves
- Big-Picture Data Exposure Across The Public Sector

Even if names are omitted, addresses, case numbers and demographic information can make re-identification possible by matching with other public-facing records like voter lists and property data. For the DRS population set, for which names and case status were included, the sensitivity is higher: there is information that allows one to infer participation in certain programs that individuals could reasonably expect not to make public.
How An Internal Map Tool Was Mistakenly Made Public
The episode revolves around an internal mapping application — the type that many government agencies use to visualize caseloads, track the coverage of services and plan where resources are needed. As it happens, these solutions frequently collect information into geographic layers and dashboards. If a setting flips a layer from internal to public, even someone with the URL of a seemingly private map can see it — and maybe even do so in some cases with help from a search engine.
Security experts often point to misconfigured web apps as the top culprit behind government data exposure. U.S. Government Accountability Office reports have long raised the flag that gaps in inventory, access controls and change management for web applications can often cause sensitive datasets to be left unintentionally exposed. The most recent industry-driven studies, including the Verizon Data Breach Investigations Report, still list misconfiguration among the top root causes of data exposure across different industries.
Potential Harms And Who Is Most At Risk From Exposure
Addresses attached to program case numbers provide scammers with useful information they can use to draft credible phishing attempts that appear to originate from a benefits office. A standard scam could call on a real case number and demand “reverification” for the purpose of gleaning Social Security numbers or bank information. Rehabilitation service users may also experience stigma or unwanted contact if it becomes known they took part.
IDHS added that it cannot confirm if the vulnerable maps were indeed accessed. Such a variable risk is not canceled out by such uncertainty. Data brokers, bad actors and automated web crawlers regularly scrape significant portions of the internet; when sensitive records are copied, they can linger in caches and private repositories long after a site is secured.
Agency Response, Regulatory Obligations And Accountability
The agency broke news to employees that access to the mapping site had been cut and that an investigation was under way. The breadth of the exposure is likely to attract the attention of federal and state regulators. Medicaid data can be considered protected health information under rules enforced by the U.S. Department of Health and Human Services’ Office for Civil Rights, which mandates that individuals and regulators are notified when unsecured health data is breached. The Illinois attorney general also has breach reporting requirements under state law for breaches of personal information.
It will depend on whether people could have reasonably been identified with only the addresses and case numbers in a larger dataset that was scrubbed of names, when deciding if that met the criteria for health or privacy breach reporting. For the smaller DRS cohort, names and case status are likely to be considered personally identifiable and sensitive.
Guidance For Affected Residents To Protect Themselves
- Residents who receive notices from IDHS should be cautious of any unsolicited calls, texts or emails about benefits. Do not provide personal information unless you make contact through a phone number posted by the agency. Be on the lookout for messages that reference your case number and suggest taking “urgent” action — that’s a classic phishing move.
- Consider putting a free security freeze on your accounts with the three major credit bureaus — Equifax, Experian and TransUnion — which will prevent new credit from being opened in your name without explicit permission. Although the exposed records may not have included financial credentials, in such cases criminals frequently aggregate partial data from different episodes to create complete profiles.
- Monitor benefits statements and notify IDHS immediately of any discrepancies.
Big-Picture Data Exposure Across The Public Sector
It’s no one-off issue, either. Misconfigured portals have resulted in the exposure of sensitive information at other federal agencies, as well as a health insurance exchange breach that exposed congressional staff records and multiple municipal mapping scenarios in which private layers were mistakenly made public. The lesson is that internal tools warrant the same rigor as a public site in at least role-based access controls, authentication, audit logs and regular configuration reviews.
It will take more than shuttering one portal to restore Illinois residents’ confidence. Agencies with responsibility for benefits data should adopt a program of ongoing monitoring to ensure that accidental public exposure is avoided, red-team against internal apps, limit the use of direct identifiers in analytics layers and have data classification policies that assume mapping outputs are sensitive. Residents want the state to provide services — and to keep their information off the open web.

