Google has begun shutting down its dark web report tool — the database of credentials it collected over more than a decade by scraping criminal forums and sites on the dark web — which automatically alerted people if their information was among them.
The company has started informing users that it will cease scanning for new content on January 15, while all existing reports on user accounts will be deleted by February 16.
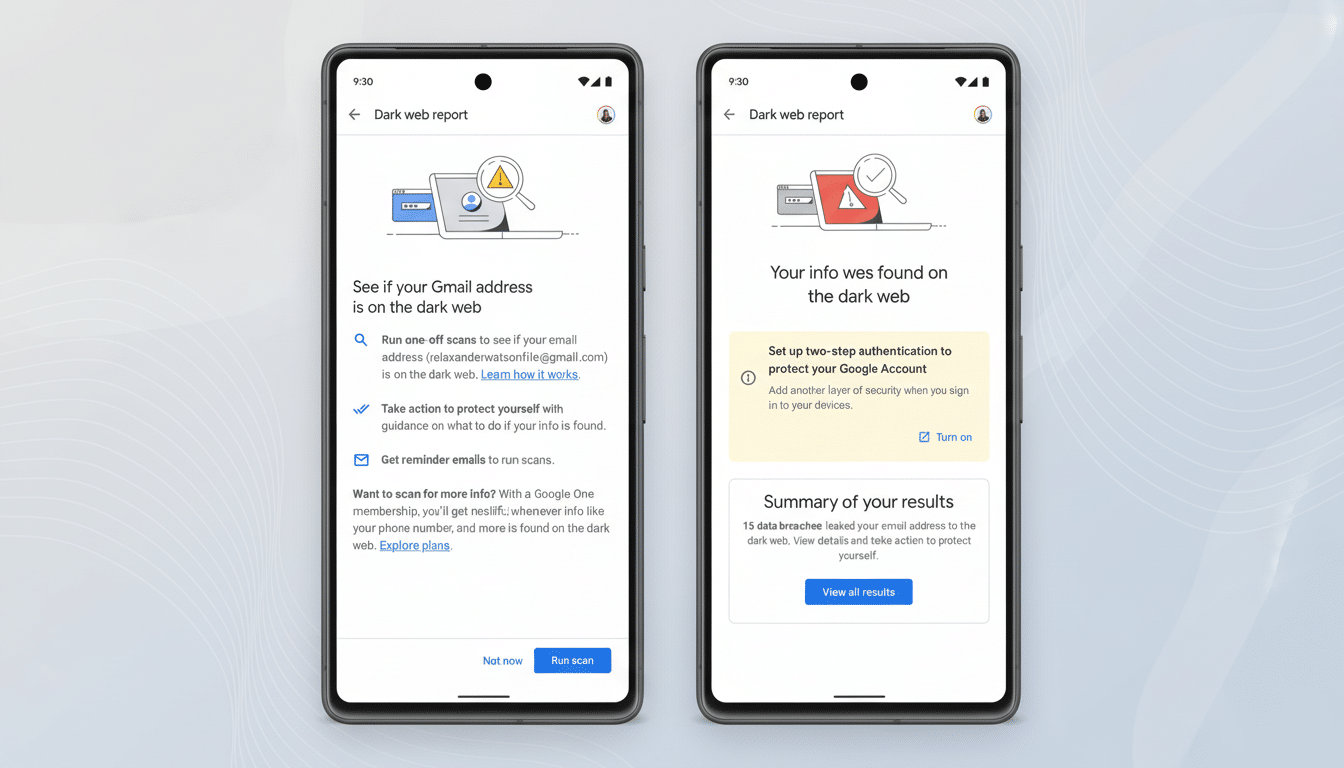
The dark web report, which was first released as a premium perk for Google One users and later made available to all account holders, provided a one-stop shop to find out if your email addresses, phone numbers, or other identifiers were being circulated in illegal markets. The shutdown means that centralized view is disappearing, even as Google insists it will still be doing broad threat monitoring in the background.
Why Google Is Sunsetting the Dark Web Report Tool
Google also said that while the feature surfaced useful signals, many users found it difficult to know what to do after being presented with raw breach data. In the wild, it can be bewildering to see a set of exposed identities — sometimes scraped, other times years old — without guided remediation. The company says it’s prioritizing protections that work by default, like stronger sign-in defenses and automated account alerts, over providing a separate dashboard.
That shift dovetails with Google’s larger push for built-in protection: Chrome’s Password Manager runs your credentials through breach checks, account Security Checkup flags bad usernames or reused passwords, and two-step verification now comes auto-enabled for big swathes of the user world. Google has also rolled out its own Results About You tools to assist people in wiping sensitive personal information from Search results, whether or not it’s associated with the dark web.
What Will Become of Existing Dark Web Reports
Two dates matter. On January 15, Google will cease allowing new appearances of your data to be monitored. Beyond that, you can still see your current dark web report, but just temporarily. It also plans to remove report data from user accounts on February 16. If you depend on the tool, take some time to review and save any details that you’ll need beyond those deadlines — especially any email aliases, phone numbers, and addresses that you have been keeping current.
Importantly, Google isn’t giving up on threat intelligence work. The company notes that it will still monitor criminal ecosystems to inform product defenses and abuse prevention moving forward; it is only sunsetting this dedicated consumer-facing report.
What to Do Instead After the Dark Web Report Ends
If the dark web report was your early warning to check in, you’ve still got choices. Begin with what is built in: run Chrome’s password check, rotate any reused passwords, and set up two-step verification or, better yet, passkeys for your most sensitive accounts. Google’s own Security Checkup is still generally the best baseline for risk hardening.
- Sign up for breach notifications from Have I Been Pwned.
- Use Mozilla Monitor for remediation steps when your data is detected in a known breach.
- Consider security suites — including Microsoft Defender’s identity theft monitoring in some regions — that search for exposed identifiers, or use consumer identity services with credit alerts.
- If your Social Security number or other financial information has been exposed, place a credit freeze with the major bureaus.
- Establish bank and card transaction alerts.
- Audit account recovery options; attackers often target phone numbers and backup email addresses to reset passwords.
The Bigger Picture on Data Breach Exposure
Data breaches continue to be a persistent, expensive problem. IBM’s most recent Cost of a Data Breach Report pegs the average breach cost globally at roughly $4.9 million, an indication that stolen data translates into real-world destruction. Also worth noting because it reinforces the importance of unique passwords and multi-factor authentication: Verizon’s 2018 Data Breach Investigations Report (PDF) found that email — not websites or malware — is the most common vector for initial compromise in a data breach, with stolen or lost credentials involved in over 90 percent of these incidents.
High-profile episodes in recent years have illustrated how long-tail exposure remains, from giant dumps of credentials to supply-chain compromises that struck hundreds of organizations as a result. Even when a leak is years old, crooks reuse the same information sets, trying them against accounts that haven’t changed their passwords or use the same logins from another site.
Closing the dark web report takes away a nifty dashboard, but the fundamentals haven’t changed: devalue any leaked data by tightening down accounts; minimize reuse, and then when you get notified of a breach, no matter the source, act. With scanning set to end on January 15 and report data to be deleted on February 16, now is the time to check your findings, shore up defenses against an attack, and prepare yourself for what comes next.

