Google is reversing one of its most controversial new attitudes toward Android. Following pushback from the developer community and power user audiences, it will offer an “advanced flow” in which experienced users can explicitly choose to allow apps to be installed from untrusted sources, giving Apple a way to reopen legit off‑store channels without ditching its broader security program.
What the advanced flow changes for Android sideloading
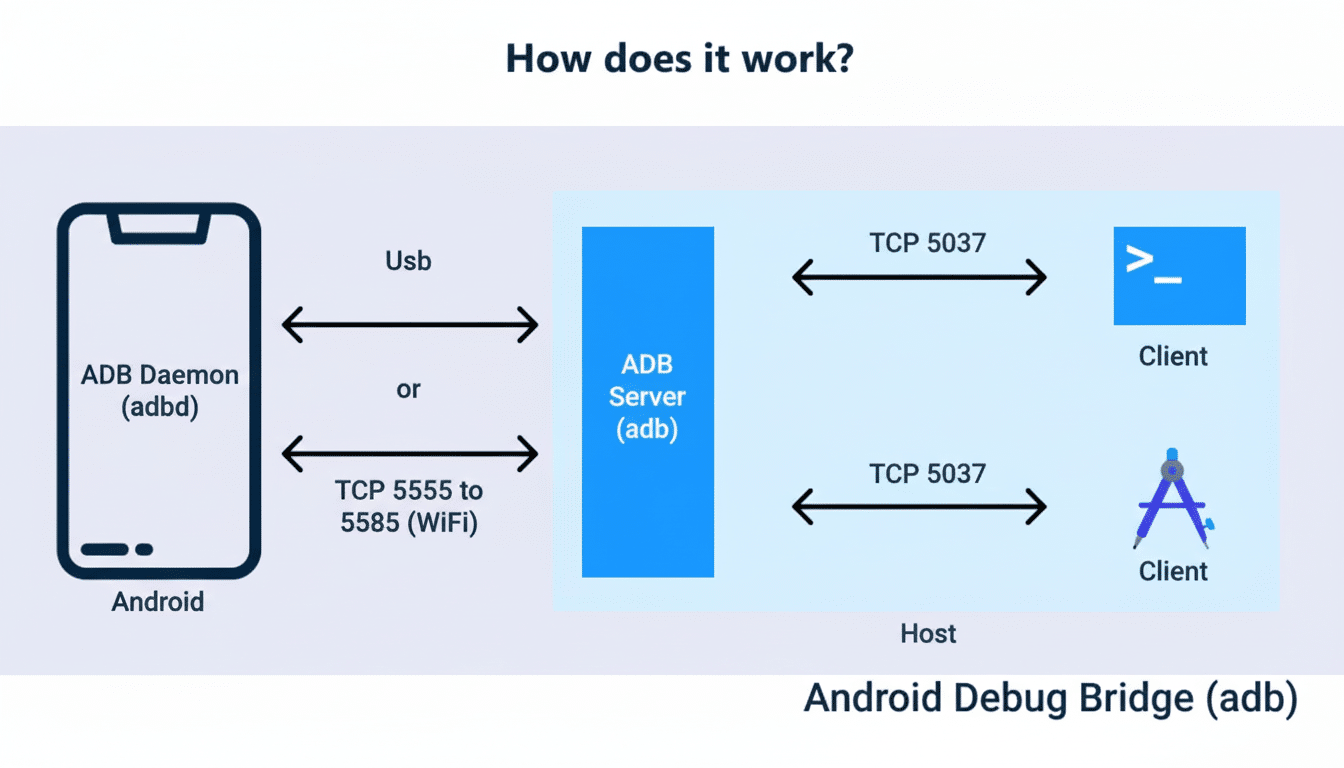
In Google’s new plan, users who know the risks can undertake a controlled, high‑friction process to install unverified apps. The pragmatic workaround, for some time, was to sideload via ADB, a developer tool never meant to serve as a consumer portal. The new flow is designed to attempt to make that possible in the UI, with clear, repeated warnings and opt-in steps.

Google says the experience is being “designed to resist coercion” — an oblique reference to real-world scams in which attackers sometimes pressure victims over the phone, instructing them how to bypass warnings. Anticipate things like unskippable explanations, delay timers, and systemwide confirmations that are tougher to railroad a non-technical user through. In short, the door isn’t shut, but it’s being watched.
Crucially, this is not a universal rollback. The default stance is still guarded: Apps from non-verified developers will not install with a single tap. “But for developers, testers and enthusiasts who purposefully run outside of app stores, the enhanced flow should be a new feature supported in key scenarios.”
Why Google restricts sideloading in the first place
Google’s Android Security Team has long wanted us to believe that social engineering, rather than zero‑day vulnerabilities, are the greatest threats to the security of mobile devices. Security firms such as ESET and ThreatFabric have observed campaigns in which attackers impersonate bank or delivery services, spamming targets with links to sideloaded APKs of fake “verification” apps. When installed, these apps ask for notification access or Accessibility permissions to capture 2FA codes or carry out on‑device fraud.
According to Google’s annual Android security reports, devices that download apps from outside of trusted stores have a higher rate of potentially harmful app (PHA) installs compared with devices that do not. Though specific numbers vary by region and year, it’s a clear pattern: distribution channels without the vetting of developers and enforcement of policies are more risky. That pattern has been particularly stark in certain areas of Southeast Asia, where law enforcement officials have repeatedly warned about phone‑extortion scams connected to the installation of sideloaded malware.
By forcing developer identity verification, developers hope to make abuse more expensive. When bad actors are forced to have distribution tied back to a real, repeatable identity, they can’t spin up new campaigns as easily post-takedown. In theory, that should slow the churn that enables social‑engineering operations to persist over time.
Developer verification and the new onramp for distribution
App-like methods were known to have worked in years gone by, but nothing could be further from the truth these days.
Enrollment occurs via the Android developer console and is designed to ease the transition ahead of enforcement, which will impact shippers through Play already who will be entered into the same verification framework, harmonizing policy across distribution channels.
To prevent that barrier from freezing out new entrants, Google intends to create a special account type for students and hobbyists. It will include some more relaxed verification and will waive the standard registration fee, but with strict distribution limits so it can’t be used to run a public app store. That compromise acknowledges the part side projects and university labs play in Android’s developer pipeline while preserving a friction layer to mass abuse.
What power users can expect from the revised sideloading flow
The advanced flow is a welcome relief for the ROM community, enterprise testers, and users depending on apps from third-party stores. It also acknowledges that not every legitimate Android app comes from a mainstream store, maintaining OS-level openness while encouraging users to think twice about one‑tap installing from a faceless corner of the internet.
The feature is almost certainly going to closely mirror Play Protect. Look for real‑time scanning, certificate checks and risk scoring to stay in the mix, as well as clearer developer identity signals in the installer. If Google includes revocation or reputation data in that flow, it may significantly inform user choice — a clarion call by security researchers for decades.
The trade-offs and the road ahead for Android sideloading
It’s a pivot of calibration, not ideology. It is still Google’s plan to crack down on drive‑by abuse and high‑pressure scams. But it’s a recognition that an all-or-nothing approach doesn’t really represent how Android is used by its most involved users.
The questions now are pragmatic: Will the OEMs roll out the more advanced flow uniformly? How many steps are too many for the legitimate user to endure? And will verification meaningfully change the economics of sideloaded malware, which is all about scale and anonymity?
If Google can get it right, Android maintains its established image as a relatively flexible operating system while clamping down on bad actors. If it overcompensates, fans will flee back to ADB and kludges. The company is soliciting feedback as it finalizes the design, and that input — from security teams competing to break Facebook’s security teams, indie developers who immediately understand its utility and power users for whom arcana isn’t a consideration — will be what decides whether this lands as a reasonable compromise or a brief detour.

