Phishing is still the easiest way in for attackers, but traditional anti-phishing training rarely does much to move the needle. A recent study by UC San Diego Health and Censys suggested that little separates the failure rates of staff who did complete annual phishing modules from those who didn’t, while click rates grew when campaigns were extended. In times of short attention spans and persuasive adversaries with good pretexts, organizations need controls that do not rely on perfect user behavior.
The business risk is undeniable. The Internet Crime Complaint Center, a service of the FBI, reported a total of more than $12 billion in losses from cybercrime in 2023, and business email compromise alone accounted for billions. The “human element” remains the central theme in most breaches as exemplified once again by Verizon’s most recent Data Breach Investigations Report. The answer is not more videos and quizzes; it’s designing systems that assume people are busy, distracted, and occasionally fooled — and yet still keep attackers out.
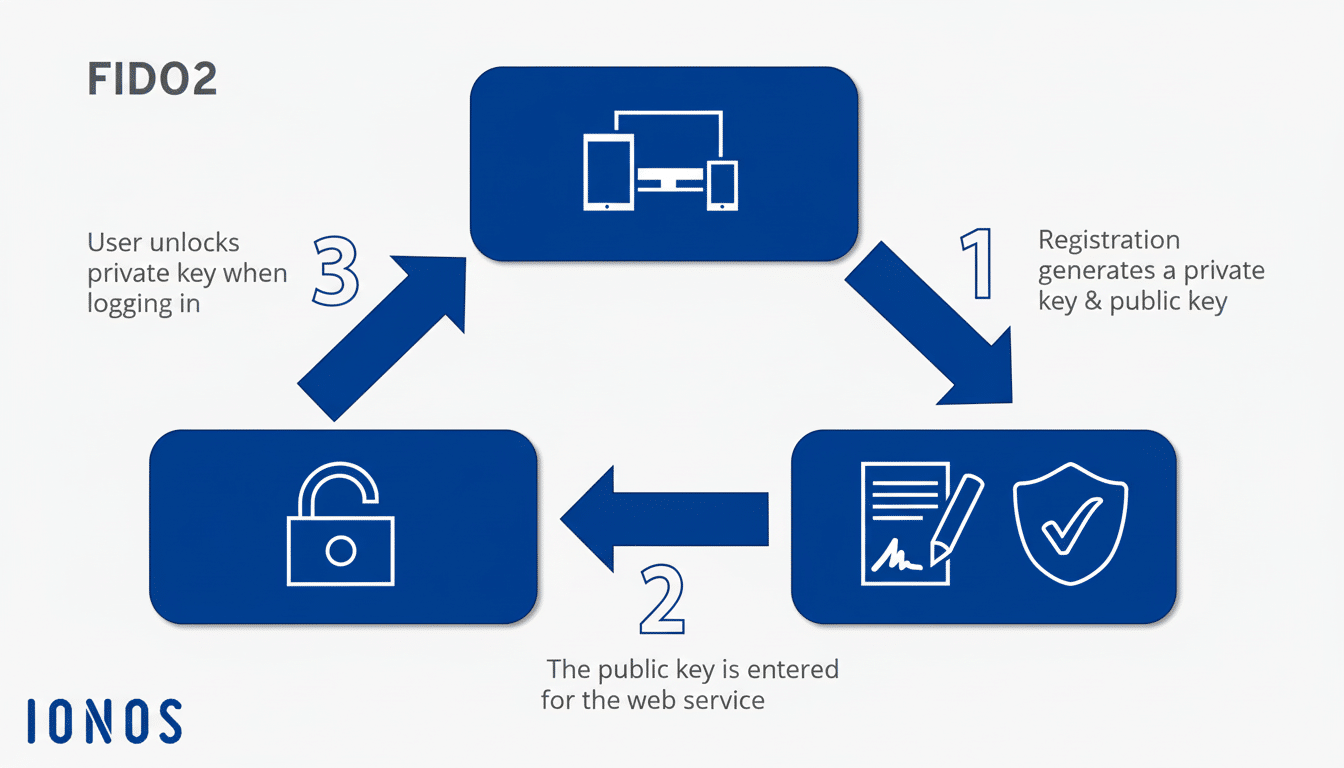
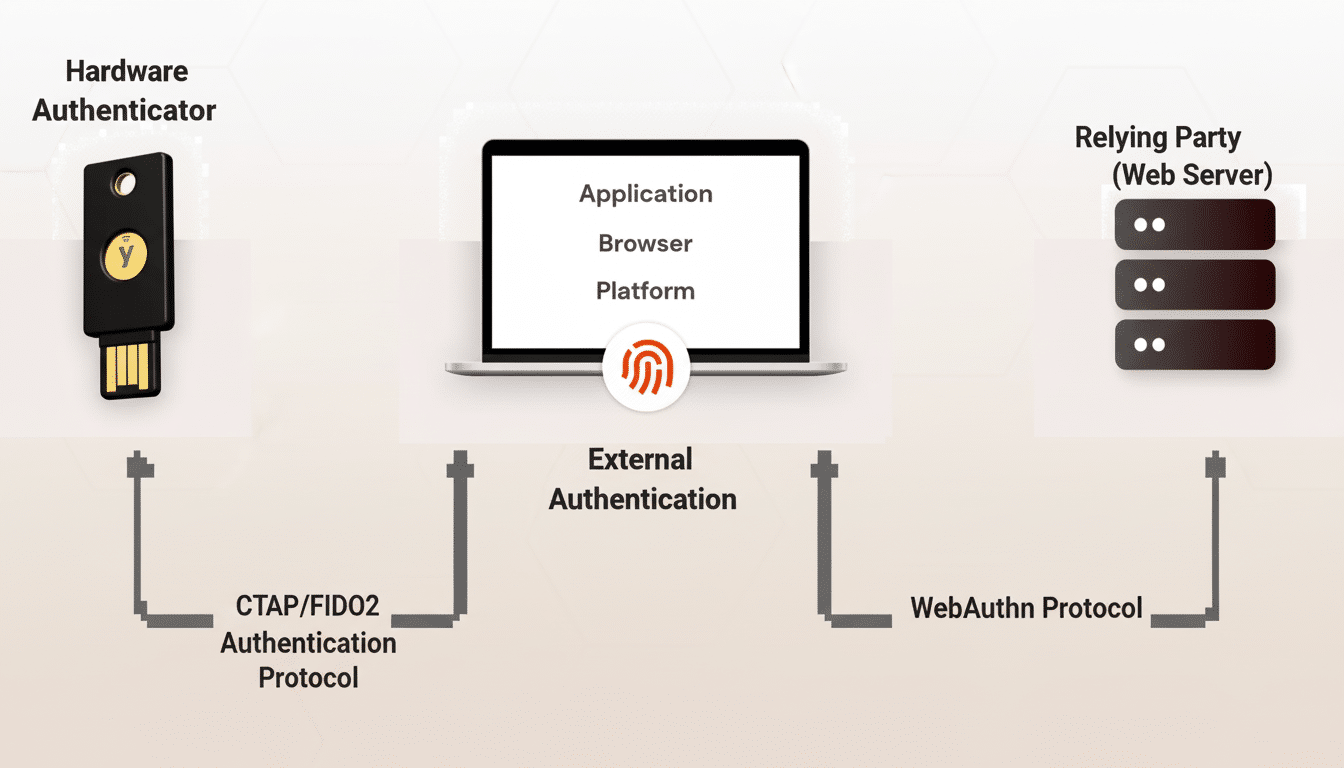
Implement Phishing-Resistant Authentication and Identity Controls
Begin by ditching passwords as a single point of failure. Embrace phishing-resistant multi-factor authentication based on FIDO2 and WebAuthn (passkeys) and retire SMS codes that can be intercepted or socially engineered. Microsoft has said that turning on multifactor authentication prevents the vast majority of bulk account takeover attacks, and Google noticed a big decline in hijackings when it started automatically asking users to activate two-step verification.
Combine strong authentication with identity guardrails: conditional access based on device health and location, step-up authentication for risky actions, and automatic blocking of impossible travel logins. Watch for mailbox forwarding rules, abuse of OAuth consent, and legacy protocols. For admins, use a privileged access management tool to provide just-in-time elevation and recording for sessions. These protections weaken the theft of credentials, even when users fall for them.
Lock Down Email and Protect Your Business Domain
Most phishing starts with email, so raise the drawbridge. Implement SPF, DKIM, and a strong DMARC policy to stop threat actors spoofing your domain; national cybersecurity authorities such as the UK’s National Cyber Security Centre advocate for DMARC with a “reject” policy on executive domains. On the inbound side, leverage advanced email security with URL rewriting and detonation, attachment sandboxing, and language-based impersonation detection for executives and finance teams.
Extend visibility beyond your inbox. Track lookalike domains and brand violations, particularly around product launches or finance cycles. Throw in supplier risk checks — hacked vendor accounts are a popular way to get into business email compromise. Robust domain protections and impersonation defenses mean that when a supplier’s mailbox is taken over, convincing but fake invoices can be kept out of the regular flow.
Let’s Contain the Blast Radius with Zero Trust Segmentation and EDR
Assume that an attacker will get in eventually.
Network segmentation, least privilege, and device posture checks will mean a single phished user can’t get to the crown jewels. Apply modern endpoint protection and behavior-based detection & response (EDR/XDR) to identify when credentials are misused, tokens are stolen, and lateral movement… minutes after a click instead of weeks later in an audit.
Overharden the fundamentals until they beg for mercy: rapidly patch browsers and plugins, disable unneeded macros, allowlist risky applications. Telemetry-driven containment — things like auto-isolation of a likely compromised host and disablement of any stolen session tokens, or an Outlook rule that blocks newly minted mailboxes — gives IR teams time to catch up. IBM’s Cost of a Data Breach research finds again and again that the quicker an organization can detect and contain one, the less it will have to pay when history writes its final bill.
Secure Payments with Out-of-Band Verification and Dual Control
Most phishing-infected intrusions are all about getting money to flow. Require dual control for wire transfers, payroll changes, and vendor banking changes — period. Even if it looks like it’s from someone you know, refuse change requests via email until an out-of-band callback is performed to known phone numbers. Establish cooling-off periods and dollar thresholds that will trigger follow-on checks.
Blend finance systems with fraud safeguards like positive pay, account holder confirmation, and anomaly monitoring for new payees or irregular schedules. Why it matters: The FBI’s 2023 numbers drive home why this matters: Business email compromise continues to be one of the largest sources of reported losses. Such technical controls that break the last mile of a fraudulent payment are frequently the difference between nearly and actually becoming scammed for seven figures.
None of these defenses prohibit training; they are your organization’s fail-safes. The UC San Diego Health results are a reminder that focus is a limited resource. Construct guardrails that assume error, and you’ll relegate phishing from a company-ending event into a containment issue.

