Everybody wants a simple answer to a complex question: how much cybersecurity is enough? In times of password breaches, ransomware attacks, and AI-engineered, convincing scams, the new baseline is higher than it once was. The aim isn’t perfection; it’s simply stacking enough layers to make you a hard target without turning life into one giant chore.
What Is ‘Enough’ Security Now for Everyday Users?
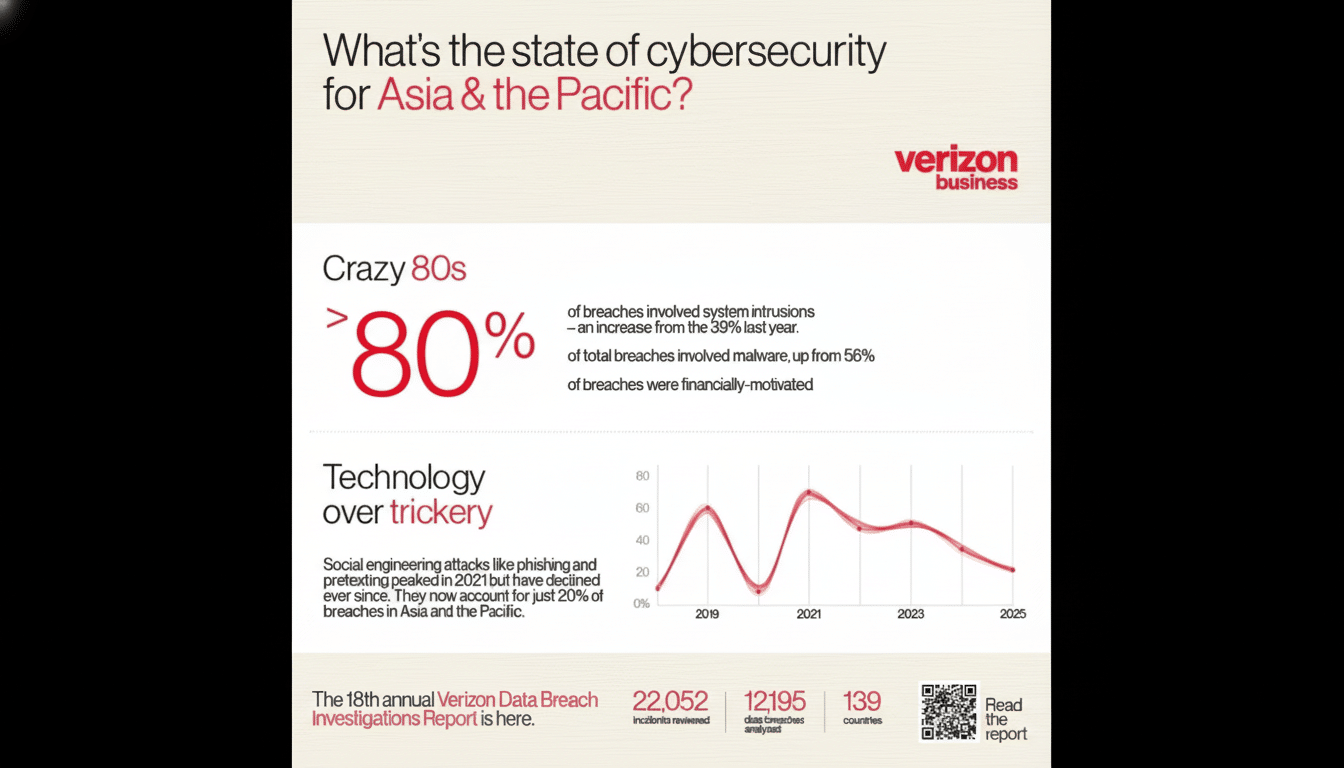
Threats have evolved from noisy viruses to silent credential theft and fraud. The FBI’s Internet Crime Complaint Center consistently logs billions in reported losses, with business email compromise in the lead. Verizon’s Data Breach Investigations Report reveals humans as one of the biggest causes behind security breaches, as ENISA points to ransomware-as-a-service and credential stuffing among continuing threats. The upshot: Identity and access, not just malware, are the hallmarks of modern exposure.
- What Is ‘Enough’ Security Now for Everyday Users?
- The Baseline Cybersecurity Setup for Most People
- When to Step Up Protection and Add Advanced Defenses
- Small Business and Solo Professionals: Security Essentials
- How much to budget for practical, layered security
- Bottom line: build layers and practice fundamentals
The Baseline Cybersecurity Setup for Most People
Start with modern endpoint protection. Pick an effective security suite that features behavior-based anti-malware, as well as anti-phishing, web filtering, application control, and firewall controls for all of your devices. Just a signature-based antivirus alone is not enough anymore.
Enable multifactor authentication everywhere possible. Microsoft has long said that MFA prevents the overwhelming majority (like, 99%) of automated break-ins to accounts—particularly if you use app prompts or FIDO2 security keys. First, focus on email, cloud storage, banks, and social media.
Use a password manager. Strong, unique passwords will kill credential stuffing. If one site is compromised, the damage does not spread. Combine that with auto-updates on operating systems, browsers, apps, and yes, even your router firmware. Unpatched software is easy pickings for attackers.
Back up like you mean it. Adhere to a 3-2-1 strategy: three versions of crucial data, in two different formats (on various kinds of media), and one offline or immutable. Enable versioning to roll back after a ransomware strike or inadvertent deletion. Test restores—backups you can’t restore are just costly adornment.
Use a VPN selectively. On public or untrusted Wi-Fi, a trustworthy no-log VPN encrypts your connection so snoops can’t see what you’re doing online. At home, prefer strong Wi-Fi security (WPA3), a unique router admin password, and a separate network for smart-home devices over a VPN-on-all-the-time habit.
Harden your devices. Turn on device encryption, screen locks, and remote wipe. On phones, restrict what apps can do; on laptops, separate admin from daily user accounts. The brief setup is worth it the first time something does go missing.
When to Step Up Protection and Add Advanced Defenses
Others have more on the line: regular travelers, gig workers working off invoices, creators with followings in the thousands or millions, cryptocurrency holders, and those who may be subject to targeted harassment. If you’re that person, add phishing-resistant MFA, involving physical security keys, email filtering with DMARC-protected domains, and account-monitoring alerts. Privacy-respecting identity monitoring and a credit freeze can be used to mitigate new-account fraud.

If you have money or sensitive data under management, graduate to endpoint detection and response (EDR) on all computers—not mere baseline antivirus. Lock down browser extensions, turn on DNS filtering to stop known-bad domains, and use different devices or profiles for banking, work, and casual browsing. Compartmentalization reduces the blast radius.
Small Business and Solo Professionals: Security Essentials
Apply a Zero Trust mentality: authenticate explicitly, give least privilege, assume breach. Single sign-on with mandatory MFA, mobile device management for laptops and phones, and role-based access control for files and applications. CISA’s guidance emphasizes the fundamentals done well: patching quickly, backing up reliably, and logging meaningfully.
Implement EDR or XDR on endpoints, set SLAs for patching, and perform vulnerability scanning on a regular cadence. Keep backups off-domain and immutable: many ransomware crews now delete or encrypt backups as their first stroke. Conduct tabletop exercises so that the first incident is not your dress rehearsal.
Know your recovery numbers. Establish recovery time (RTO) and recovery point (RPO) targets, then ensure your ability to meet them. IBM’s data breach research has illustrated many times that the speed at which recovery and containment occurs wields a great influence over impact.
How much to budget for practical, layered security
For the average person, this means paying a small monthly fee for a password manager, a reputable security suite, and cloud backup—in many cases less than what you would pay for a streaming pack. Yes, add a good-quality VPN if you travel or use public Wi-Fi. High-risk users will want to consider adding security keys and identity monitoring.
For small companies, the rule of thumb should be to budget for the controls that materially mitigate your top risks: MFA, EDR, patching automation, backups with immutability, and training. Cyber insurance increasingly demands these controls anyway, and insurers commonly embrace frameworks from NIST and guidance echoed by CISA and ENISA.
Bottom line: build layers and practice fundamentals
“How much” security is less about a number than layers. For the majority of people: endpoint protection, MFA, a password manager (please use it with commitment), updates, trustworthy backup, and smart Wi-Fi hygiene take care of essentials. If you have a higher degree of risk, then throw in hardware keys, better isolation, and EDR. The key is discipline—practice the fundamentals consistently and you’ll outpunch the odds attackers bank on.

