Cloudflare’s chief eXplained the scope of what was lost in technical detail after an untold number of websites briefly went down across broad swaths of the internet, bringing services like X and ChatGPT to their knees. The episode, which the company describes as its worst since 2019, was due to a bug in the bot protection system rather than an outside attack.
What Broke Inside Cloudflare’s Bot Defense
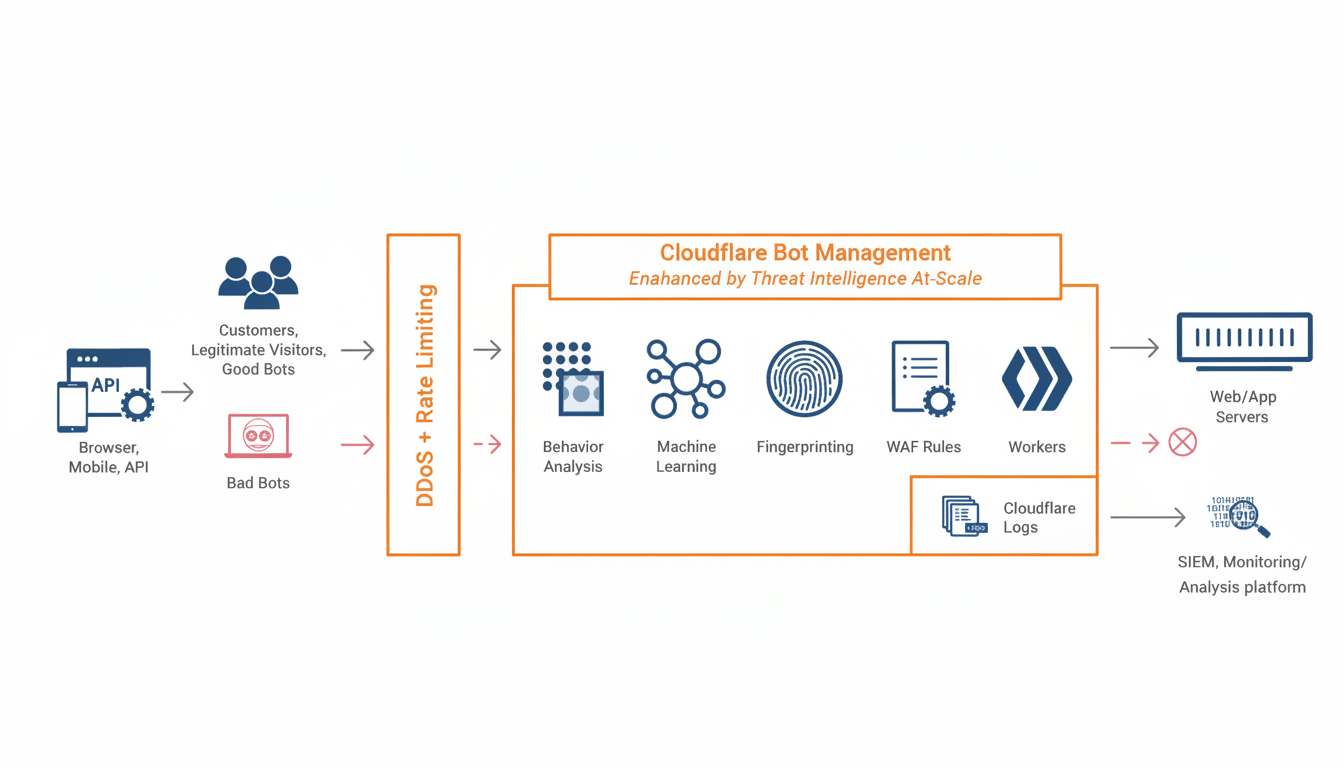
At the heart of the outage was Cloudflare’s Bot Management, which looks at incoming requests and distinguishes which are from nefarious automation (pretty much everything from volumetric DDoS floods to credential stuffing or scraping). The service uses an AI model that scores each request for risk against a collection of computed signals laid out in a “feature file.”
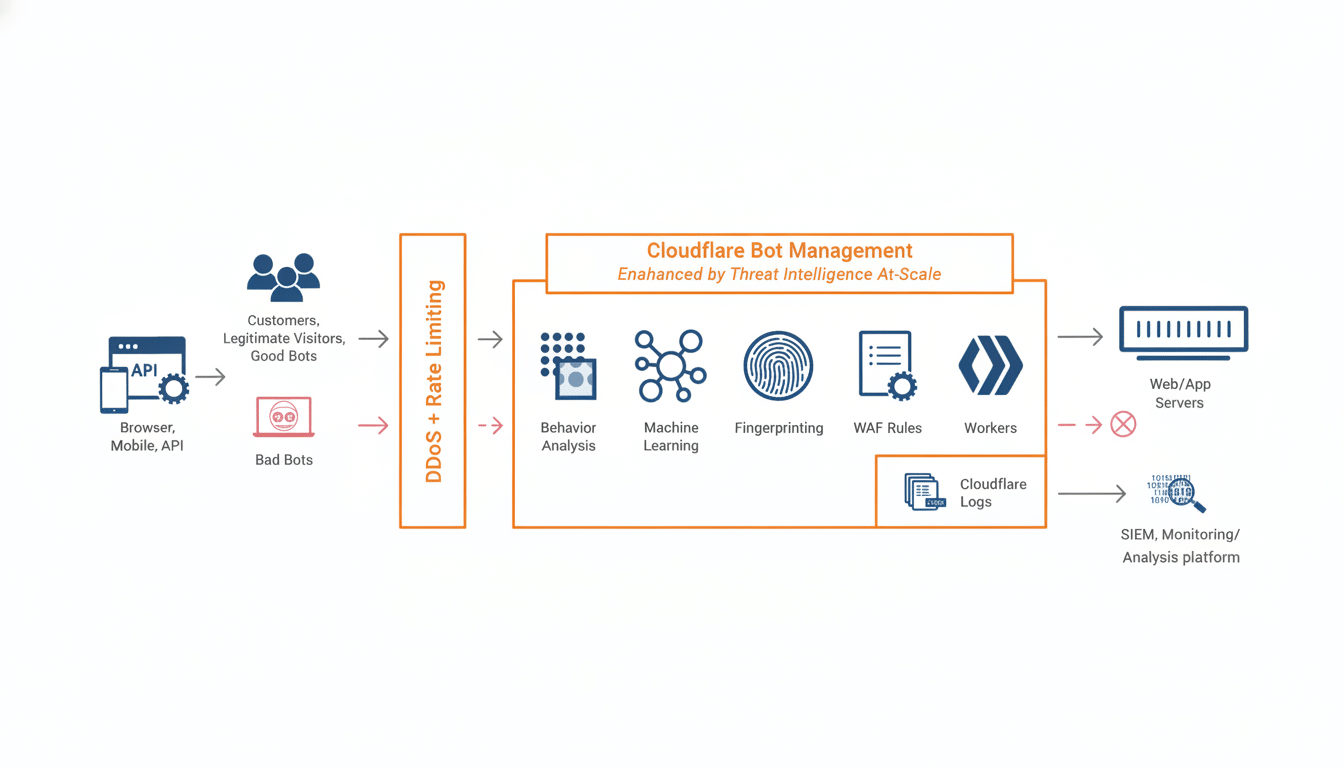
That feature file refreshes every five minutes across Cloudflare’s global network to keep up with the constantly changing behavior of bots. A modification was made to the query that creates the file, repeating entries at scale and making the files much larger than usual. The scoring pipeline failed on legitimate traffic at the edge when the oversized file was propagated and it encountered errors.
The chain reaction and why so many sites failed
As Bot Management is inline with traffic for millions of internet properties, the malformed feature file created a ripple effect. About fifteen minutes after the update had started being pushed, Cloudflare was observing large-scale failures as edge locations started ingesting the larger-than-expected file and began rejecting requests that were protected by the service.
End users saw sudden errors instead of slowdowns, which is consistent with a logic error as opposed to just congestion. On high-traffic platforms, that makes a difference: a deterministic scoring error can block entire classes of requests at scale; one site becoming unavailable can instantly cascade across industries.
Not a cyberattack and the status page oddity
Initially, indicators pointed at a hyper-scale DDoS campaign — not to mention very slow loading times for Cloudflare’s status page, which is hosted separately from production infrastructure. The postmortem explains there was no malice. The failure was inward, a software-driven one, and the status page disruption was purely coincidental but inconvenient timing that muddied early triage.
Why this distinction matters: It is important for customers who design incident playbooks based on root cause. The company’s statement that no breach or attack occurred pivots attention directly to software change control and model feature governance, as well as blast radius containment.
Recovery timeline and what’s coming next
Engineers stopped the spread of the rogue feature file and rolled back to an earlier version, returning most operations to normal in approximately three hours and full services in five. Cloudflare says it is adding further protections, such as mechanisms to ensure that internal error reporting does not exacerbate load during an incident — subtle but important forms of backpressure that can help avoid control planes getting swamped.
More hardening around file-size validation, canarying, and progressive rollouts with strict circuit breakers is planned. These are run-of-the-mill site reliability engineering controls, but they quickly become a critical time issue when model artifacts refresh every five minutes and are propagated instantly to an enormous edge network.
Why the stakes are so high for a Cloudflare outage
Cloudflare sits underneath much of the modern web, providing security and performance services for millions of websites. Independent tracking by companies like W3Techs shows that the company is steadily becoming one of the most popular reverse proxy and CDN providers, which is why a simple feature-file mistake has been felt around the world.
The incident is reminiscent of a 2019 Cloudflare outage caused by an erroneous Web Application Firewall regex deployment — another example that configuration snafus can quickly scale up to global proportions on the internet. Today’s plot twist: The point of failure was buried in a defense that was steered by artificial intelligence, where inputs and feature stores need to be vetted as carefully as code deployments.
Lessons learned for AI and security operations
Feature governance now sits on the same checklist as code reviews: artifact size thresholds, schema validation, and rollback automation are all must-haves for model artifacts. Fast-refreshing files (such as approximately five-minute updates) must also be tightly versioned and gated behind canaries, so that a single misgenerated file does not immediately affect every point of presence.
For consumers, the takeaway is practical: don’t trust a single vendor to monitor for you (because flapping), and engineer your application’s behavior so that it’s resilient when upstream security systems start emitting errors.
For Cloudflare, the chief executive’s frank description — and clear plan to fix that issue in the future — is a show of confidence after an outage that, by its own description, was one of the most significant it had ever faced.

