For years, ransomware crews relied on a simple formula: lock the files, ask for payment and then wait. That playbook is failing. As victims are opting to pay far less often, the attackers have had to look for something more powerful and profitable than scrambled files: data that is of lasting value to its owners and yet is theirs alone to lock away.
The payment rate has fallen to about 23 percent from around 85 percent in previous years, according to Coveware’s most recent analysis. As paydays diminish, adversaries are evolving the crime. Now, encryption is no longer the apex of an attack but just a detour. The actual goal is data exfiltration and all of the leverage that this affords.
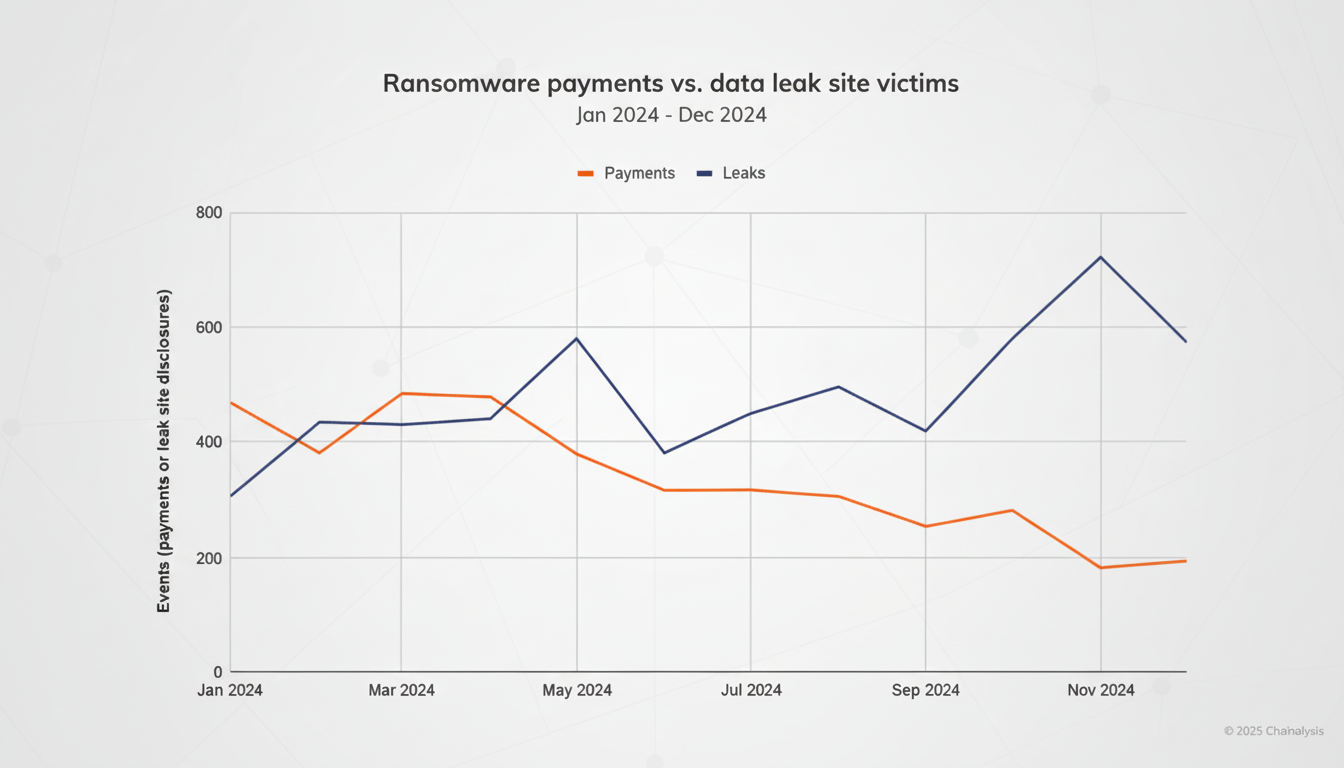
Data Exfiltration Is Now the Point of Ransomware Attacks
Leak-first extortion inverts the cost calculus. Backups help to dampen the effects of encryption, but a backup cannot unring the bell when it comes to stolen confidential files. Coveware sees data theft in 76 percent of incidents it follows, and many crews are now eschewing encryption altogether. Within hours, criminals publish “proof packs” on leak sites, send emails to customers and partners or message workers to ratchet up pressure.
Double and triple extortion maneuvers—threats to release data, launch DDoS attacks or inform regulators—pose the kinds of risks no backup can cure: reputational harm, regulatory vulnerability, litigation and customer trust erosion. This leverage persists even after a victim quickly restores operations.
Why Fewer Ransomware Victims Choose to Pay Demands
Several pressures are driving payment rates lower. And more organizations now keep immutable, offline backups—and rehearse recovery—compressing the time dimension of downtime and blunting the classic “pay to resume operations” threat. Advice from the likes of CISA, the FBI and the UK’s NCSC has consistently warned against paying up, while insurers are demanding stronger controls before underwriting for extortion-related cover.
There is a powerful legal and compliance risk, as well. As a rule, paying doesn’t stop the deletion then and there—many victims have found their data resurfacing soon after. Authorities’ warnings of sanctions take the stakes for any transaction with a banned party sky-high. Corporate lawyers are taking more of a hard-line stance, and the outside advisers who coached clients to settle to stop leaks are waning as policy leans toward not paying by default.
Shrinking Payouts Remake the Market for Cyber Extortion
Even when things do change hands, it is often less than in the past. Coveware points out the average payment is now $376,941, a 66% plunge from last quarter, with the median at $140,000—down 65%. Enterprise holdouts are a major factor: when big companies refuse to pay, the overall average drops. The smaller companies that do pay often don’t have the volumes to afford high demands.
That squeeze alters incentives. Affiliates in ransomware-as-a-service (RaaS) operations go after volume in the mid-market, whereas more advanced crews focus on “white whale” targets where customized intrusions and weeks of doggedness could lead to a monster payday. It is data theft, not just encryption, which is central to both paradigms.
A Split Criminal Economy Emerges in the Ransomware World
The ecosystem is now running on two tracks. On one side, RaaS operators rent tooling and leak-site access, itself a matter of scale monetization; on the other, specialized groups stage tailored intrusions in custom malware deployment by way of living-off-the-land techniques and stealth data staging. In addition, I suspect that law enforcement disruptions and some high-profile implosions (e.g., exit scams in which affiliates don’t get paid) have added to an atmosphere of instability, goading actors into faster, more brazen data-theft campaigns.
Real-world campaigns underscore the pivot. Mass-exploitation incidents involving the types of file-transfer, edge software vulnerabilities disclosed in recent years and affecting a wide range of victims have resulted in lists that go on ad infinitum when those impacted don’t encrypt. The extortion depends on what they stole and how quickly the criminals can authenticate it publicly.
What Defenders Should Do Now to Counter Data Theft
Defenses must assume exfiltration. Emphasize data minimization, strong encryption at rest and in transit, and tight egress controls. Clip network segments to restrict lateral traversal. Enforce phishing-resistant MFA, harden endpoints with EDR, and patch aggressively—particularly internet-exposed services and remote access gateways.
Consider backups a recovery tool, not an extortion antidote. Keep unaltered, disconnected copies; regularly test restore; and watch for staging activities such as nonstandard compression, archiving or outbound transfers. Yes to DLP where possible and using honeytokens/canary files to instrument high-value repositories for access and exfil attempts.
On the side of response, prebuild an extortion playbook, beginning with non-payment. Get legal, comms and exec sign-off in sync; write customer/regulator notification templates and define decision points. Track leak sites and criminal channels to verify claims and understand exposure without tipping off the adversary. Secure the vendor risk, as third-party breaches tend to become your problem.
The ransomware tale is more than downtime now. It’s all about leverage on your data. With payments evaporating, criminals are doubling down on what hurts most: exposure. Plan and invest accordingly.

