My phone used to function as a public noticeboard — tack up a robocall next to a coupon blast next to an “urgent” delivery update I had never requested. The hack that did finally work was not an app or a new filter. It became a policy: the real number is for people, not for companies. The rest of you get a subheading. It’s easy, it’s cheap and it has transformed how usable and tranquil my phone feels.
Your digits power the spam economy
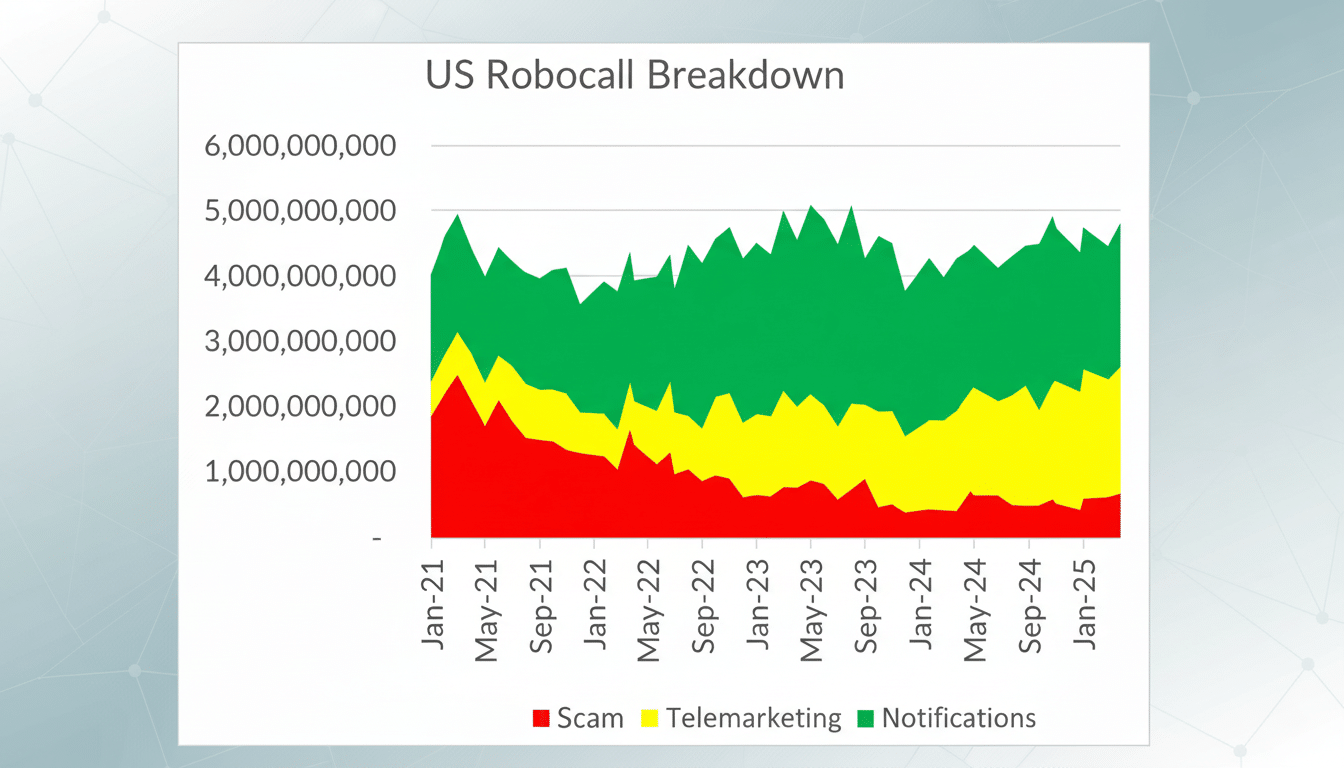
Phone numbers are a de facto universal identifier, he said, and as such they are irresistible to data brokers and advertisers. YouMail’s Robocall Index in the U.S. continues to hover around 4-6 billion robocalls per month. The Federal Trade Commission’s most recent data just noted that consumers lost tens of billions to fraud over the past year, with phone calls and text messages still serving as some of the most common vectors. Regulators from Chile to the United States and elsewhere have promoted authentication frameworks and have enforcement in the sights, but the nuisance is still there. When that number is out there, it’s tough to pull back.
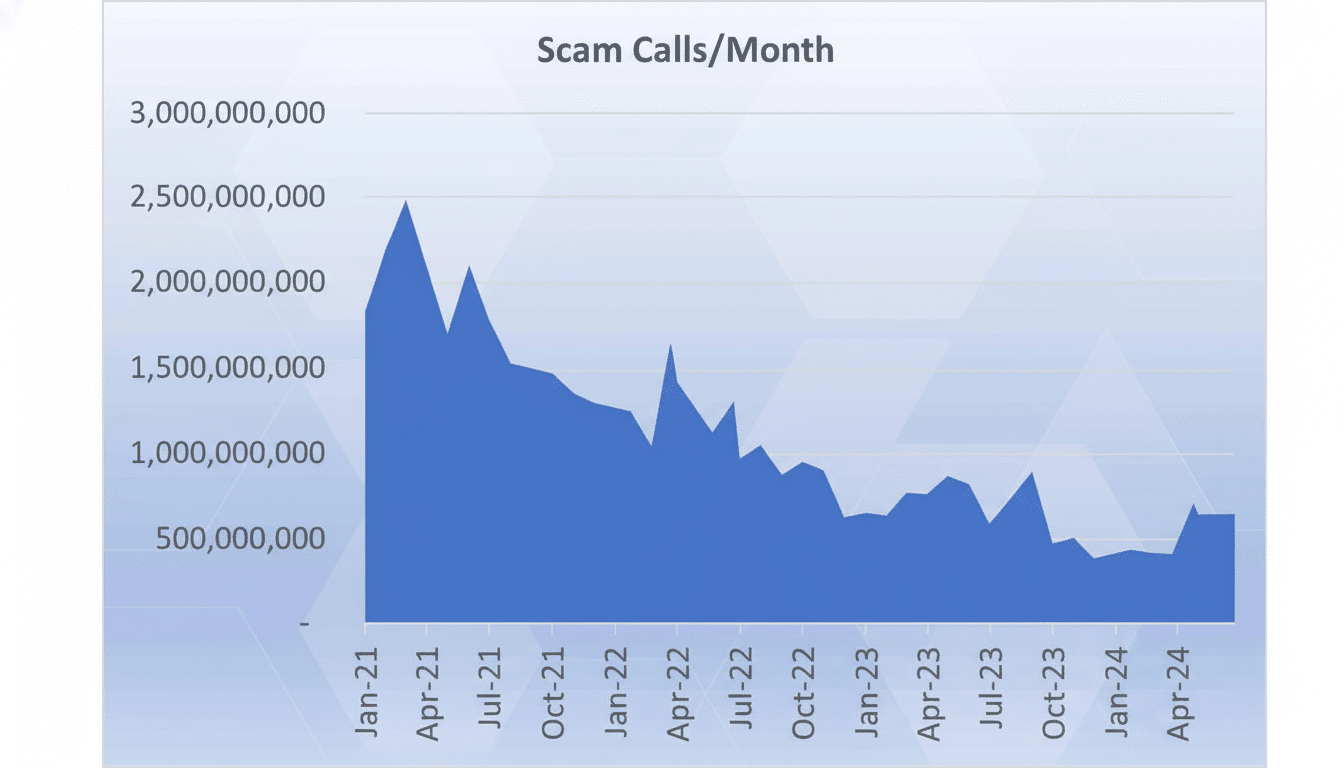
Beyond annoyance, there’s risk. Phone numbers are easily exposed through data breaches; the Verizon Data Breach Investigations Report has shown that contact information will open the door to credential theft, social engineering and account takeovers. A phone number associated with many services is low-hanging fruit for phishing and impersonation.
One phone, two identities
The practical way to do this is to bifurcate your identity: You have a real phone number for real people, and trusted accounts, and you have a burner phone number for everything else (like signing up for deliveries, shopping and anything that’s likely to text or message back). And with dual SIM and eSIM, it’s trivial on modern phones. Keep the second line on a cheap pay-as-you-go plan — just enough for incoming SMS and calls here and there. When you don’t want it, toggle it off. When you’re expecting a one-time code, flip it back on. If calls start to ramp up spammers, you can replace the secondary number without having to disturb your real-life contacts.
2. If you can’t add a physical or embedded SIM, a VoIP number from a reputable provider can often be used for many services, except some banks and secure apps block virtual lines. It’s the same principle: add friction between companies and your actual identity.
Safe and sound benefits that are more than just quiet
Segmented numbers limit your attack surface. If a retailer or delivery app exposes your data, it’s your burner, not your personal line, that is added to spam lists. That decreases the chances of targeted phishing making it to your inner circle or multi-factor prompts ending up on your primary phone at a bad actor’s whim.
There’s another, smarter MFA story here, too. Keep important accounts on stronger factors — app-based authenticators, or passkeys — and save your SMS codes for lower-impact logins or travel. Put a carrier PIN and port-out protection on each line so SIM-swap attacks are less effective. This is all in accordance with advice from security bodies such as NIST: your number shouldn’t be the only way into your digital existence.
How to establish it without making life more difficult
Begin with a prepaid eSIM plan that will allow you to send SMS and rename lines it something obvious (People vs. Services) in the settings of your phone. On Android, utilize features such as Call Screen and Silence unknown callers for the business line; on iOS, implement Silence Unknown Callers and use separate contact lists. Messaging apps that are based on contact discovery may also be fenced: you register your secondary number with services where you don’t want to be identified, like for deliveries or classifieds, while using your primary for the small circles.
When you’re registering for a new tool, stop and think about: does this entity truly need to reach me? If not, write down the second number. It becomes over time a high-signal channel on your main line, where each buzz probably means something.
Costs, caveats, and workarounds
There are trade-offs. Even the bare-bones plans are a monthly cost, and you’ll sometimes switch lines to receive verification codes. Certain institutions do not accept VoIP numbers, and not all phones have dual-SIM hardware. For foreign travel, vehicle roaming on both lines might need to be configured. None are dealbreakers — and they’re often outweighed by spam and scams declining — but they’re worth noting.
And it’s also worth remembering that while SMS-based verification is convenient, it is not bulletproof. Treat your main number as if it’s a password: Don’t hand it out to people you don’t trust, and monitor account recovery settings so companies can’t assume they should default to a compromised line for any sensitive resets.
Why this policy sticks
Dividing numbers is not just a privacy gambit; it’s a boundary. It translates in practice to a sense of trust in the ring of your phone, and the ping of a text. Companies will keep on asking for your number, though, because it hypothetically makes sign-ins more seamless and drives marketing. Provide one — just not the key that opens your time, attention and relationships.
That outcome is felt: fewer interruptions, fewer scams landing where they hurt, and a more tranquil, pinpointed experience every day. My real number is for people. Everything else clicks into the burner — and my phone feels like mine again.

