Phishing awareness courses string the prospect of safer inboxes, but the newest proof proves they achieve little to that success. A massive field study performed by UC San Diego Health and Censys researchers exposed that standard cybersecurity education had virtually no substantial effect on workers’ click-through on malicious messages.
Even simulated phishing with inserted lessons scarcely renovated the needle, slicing disappointment by perhaps two percentage points at best. This level of victory is incredibly disappointing given the convenience of phishing results in ransomware and account takeover, underlined by many of the available industry information, like the SpyCloud Identity Threat Report and the Verizon Data Breach Investigations Report.
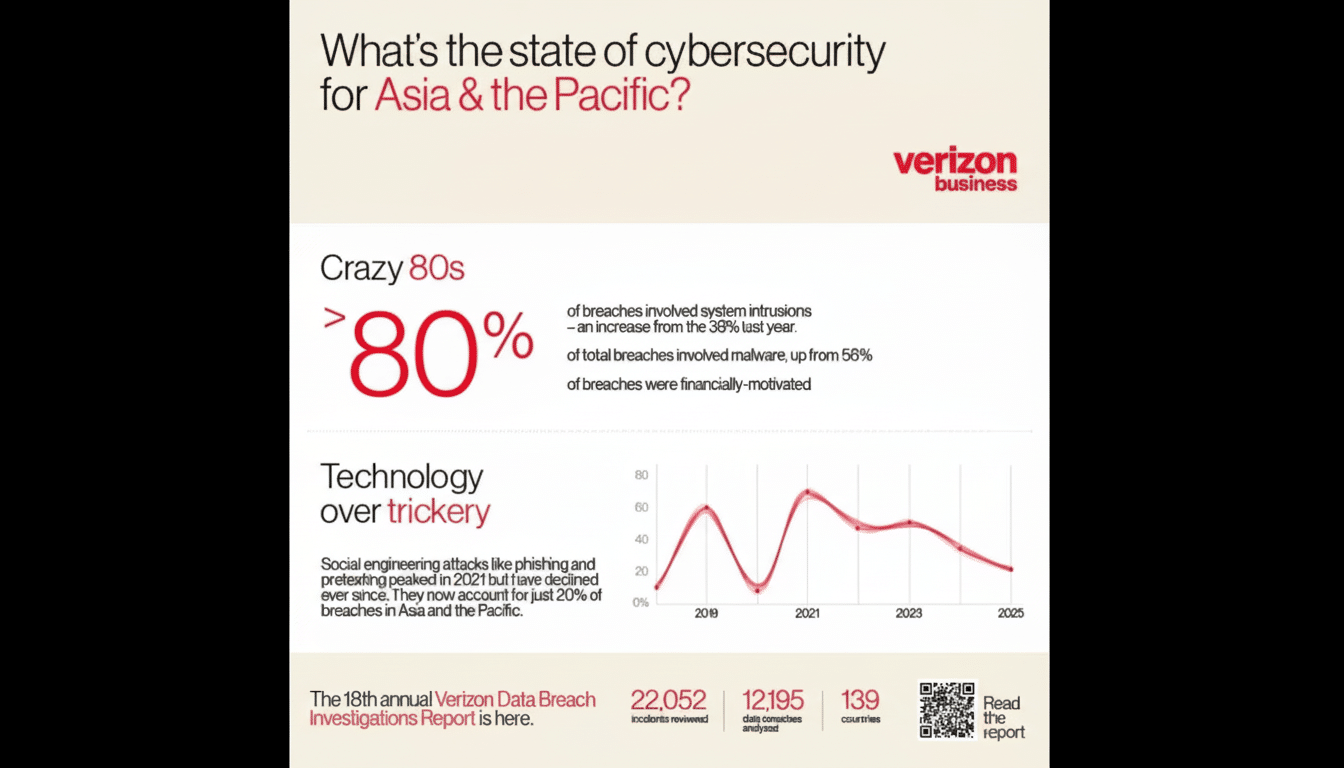
The Evidence Under The Microscope In A Large Study
The researchers assessed results across ten phishing movements administered to over 19,500 staff of a large healthcare company. One variable that failed to forecast performance: mandated yearly training. Instead, the draw more than the bait mattered: when only a few clicked on the generic “update your Outlook password” ticket, over a third fell for the “vacation bill plan update” cliché.
Over time, susceptibility improved: responses rose over the drive, beginning from low double digits and rising above half in later moves. In other words, employees didn’t get more knowledgeable; attackers got more persuasive. The final verdict was straightforward: the standard preparedness tactics provide minimal real-world guarantee against well-made phish.
Why Traditional Training Teaches So Little
Slide decks and click-through quizzes once a year are the wrong tool for a fast, emotionally manipulative threat. Phishing succeeds by diverting attention under the guise of urgency, authority and rewards. In that moment, people don’t consult a memory of rules; they act based on habit and context. Without perpetual, situational reinforcement, that knowledge dims and reflexes rule.
Simulated phish can also backfire. If the questions are too easy, staff learn nothing. If they’re too tricky, they’ll learn to mistrust internal email and hate security. If you do this, public shaming of the clickers discourages reporting — people conceal their mistakes instead of raising a hand promptly, and what incident responders need is precisely the opposite.
Companies often measure the wrong things. “Click rates” on staged emails are a vanity stat — they don’t mirror how attackers operate: including multi-channel lures, QR codes, OAuth consent abuse, and voice or chat-based social engineering. Meanwhile, email banners and generic warnings lead to alert fatigue — and users tune out exactly the cues you wanted them to see.
The Real Fix? Build Defenses Around Humans
The way forward is not more lectures; it’s resilient design, both locally and globally. Make the safe and healthy action the easy action; make the risky, unhealthy action hard to do. Security agencies including CISA and standards organizations like NIST support “phishing-resistant” authentication. That means device-based cryptographic login systems such as FIDO2 passkeys, not one-time codes that attackers can relay. And where there are passwords, apply number-matching and conditional privileges tied to device health and location on the way in.
Enhance the email stack to block more threats before delivery and actions remaining on click:
- Enforce SPF, DKIM, and DMARC with alignment.
- Roll out MTA-STS and use modern TLS.
- Sandbox and detonate risky links.
- Isolate browsers for high-risk users.
- Disable legacy protocols that supersede modern controls.
- Limit OAuth app consent and keep an eye on token issuing, a popular vehicle for silent persistence.
Redesign high-risk business workflows. Vendor bank account updates or payroll/gift card procurement requests should be prompted for out-of-band validation and dual approval. Macros and links from outside the department must be blocked by default. Restrict standing authorizations and provide temporary credentials when necessary. These restrictions help dissipate the force of those inevitable clicks.
Smarter Schooling Without The Security Theater
Education matters just as much — but it needs to be behavioral education, not performative. Quick, in-context nudges when at risk within email and collaboration tools. Sub out once-a-year marathons for minutes-long microlearning relevant to a user’s role and duties. Praise quick reporting over perfect detection; the security team can sift through noise, but they can’t examine what never comes to their attention.
Conduct tabletop exercises for executives and help desks — the very groups attackers hope to socially engineer. Train your staff on how to authenticate requests via a trusted mechanism, not to try and memorize hundreds of possible red flags. Gamify safely: challenges are opt-in and encouraged as ways to help people out, not adversarial.
How To Measure What Matters In Real-World Security
Shift metrics from “Who clicked?” to “How fast were we detecting, containing and recovering?” Track the right indicators and outcomes:
- Median time to report suspicious messages.
- Pre-delivery block rates.
- Percentage of attempted credential thefts that fail.
- How often risky changes (such as bank account updates) are interrupted by verification steps.
- Reductions in OAuth token abuse, unauthorized wire transfers, and account takeovers after control adjustments.
Real-world breaches underline the lesson. Famous intrusions at major brands have often begun with an authentic-seeming message and an accommodating help desk or a distracted employee. Training didn’t let those people down; the system failed to predict human moments. Harden the system, and humans are not your Achilles’ heel but your best early-warning sensor.
The answer is plain as day: traditional phishing training by itself is a pipe dream. Couple pragmatic, phishing-resistant technology with thoughtful and just-in-time education and better processes. It’s how you turn less clicking into fewer compromises — and security theater into security.

