Cybercrooks have been impersonating LastPass’s “after-death” Emergency Access workflow to get their hands on the master passwords of individuals susceptible to this type of attack, using both plausible emails and persuasive live phone calls to direct victims toward a phishing site that emulates an actual recovery page.
What Attackers Are Exploiting in Emergency Access
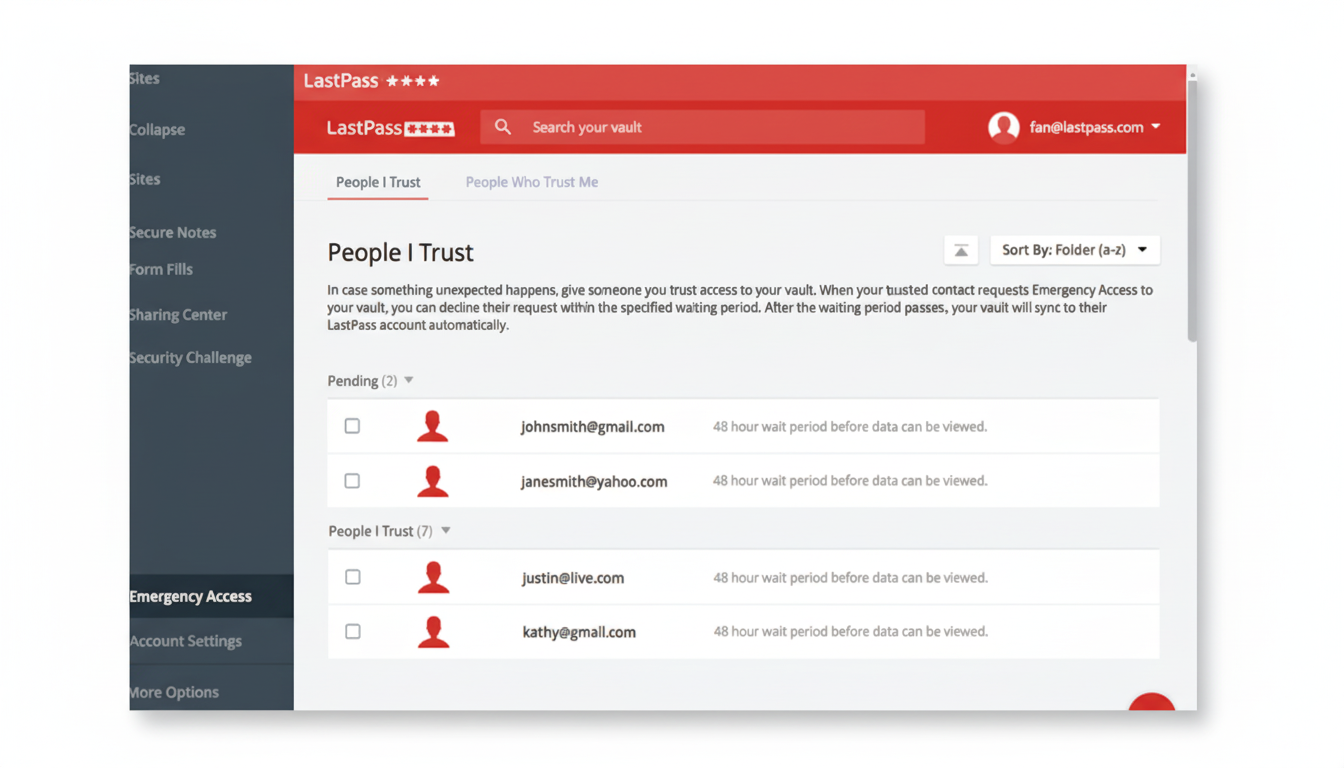
LastPass, among other password managers, allows users to designate trusted contacts who can request access to their vault after a loved one has passed or in an emergency situation. The process is supposed to be predictable: A request sets an email in motion to the account holder, a waiting period commences, and access is formally given if the request isn’t denied within that time. It is that predictable flow that scammers are mimicking.
Phishers are mailing out fake “legacy request” notices that resemble real service messages. Part of the goal is psychological as well as technical: Few alerts feel more urgent than someone trying to capture your digital estate. That urgency contributes to impulsive clicks.
How the Phishing Lure Works to Steal Master Passwords
Victims say they are receiving emails that allege a trusted contact has begun the process of taking over their legacy. The message also contains a call-to-action button leading to a domain like lastpassrecovery[.]com, a pixel-accurate reproduction that prompts the user to enter their master password. In other cases, scammers have apparently even followed up over the phone, masquerading as LastPass staff to “confirm” the alert and usher victims into typing their credentials at the mock site — classic vishing plus phishing fitting together like two pieces of a jigsaw.
The campaign was discovered in mid-October, a BleepingComputer report noted, and researchers have connected its infrastructure and tradecraft to CryptoChameleon, an entity involved with high-end phishing kits and earlier impersonation campaigns targeting U.S. government workers. The playbook includes the use of lookalike domains, search-optimized decoy pages, and orchestrated phone calls.
What LastPass and Researchers Are Saying
LastPass has said that it would never ask a customer to reveal a master password in an email nor over the phone. Should you get a legacy request notification, the best way to verify it is to open your LastPass app or go directly to the service’s site by entering its URL, and then verify Emergency Access through your account settings — never using an emailed link from within the notification of an inheritance assignment.
Imitators have taken aim at the brand often, and high-profile episodes have put it in their crosshairs.
Some hackers stole encrypted customer vault backups during a 2022 attack — data that they can’t get into unless they know the master password. That history goes some way toward explaining why social engineering is in vogue, and why, if criminals can’t break encryption, they will aim to get people to hand over the keys.
The Broader Phishing Context and Industry Trends
Type of attack: Brand impersonation and “account recovery” spoofs are on the rise across the industry. The FBI’s Internet Crime Complaint Center registered $12.5B in overall cybercrime losses in its latest annual accounting (phishing was again the most common crime category by volume). Similarly, the Anti-Phishing Working Group has reported historically high levels of phishing in 2023 with millions of attacks per month.
There are two trends that make the recovery-lure scams so effective: One, culprits can leverage legitimate workflows users expect to see; and two, they can add a ticking clock, time-sensitive urgency.
A realistic waiting period engenders a genuine sense of urgency, and sometimes that’s all it takes to overcome a healthy skepticism.
How to Protect Your Vault Now from Recovery Scams
Bypass email links entirely. If you receive one of these legacy or recovery alerts, open LastPass directly from the browser extension or mobile app and verify Emergency Access status by going to your account settings. If an in-app request isn’t pending, the email is a scam.
Harden authentication. Use multifactor authentication for your vault, with a preference for phishing-resistant options including FIDO2 security keys where available. Biometrics via a company-issued authenticator app can also minimize dependence on transmittable codes.
Scrutinize domains and caller claims. Search for subtle misspellings, extra words, or strange top-level domains. For calls, hang up and reach out to support via the official app or published avenues; never read one-time codes or divulge master passwords over the phone.
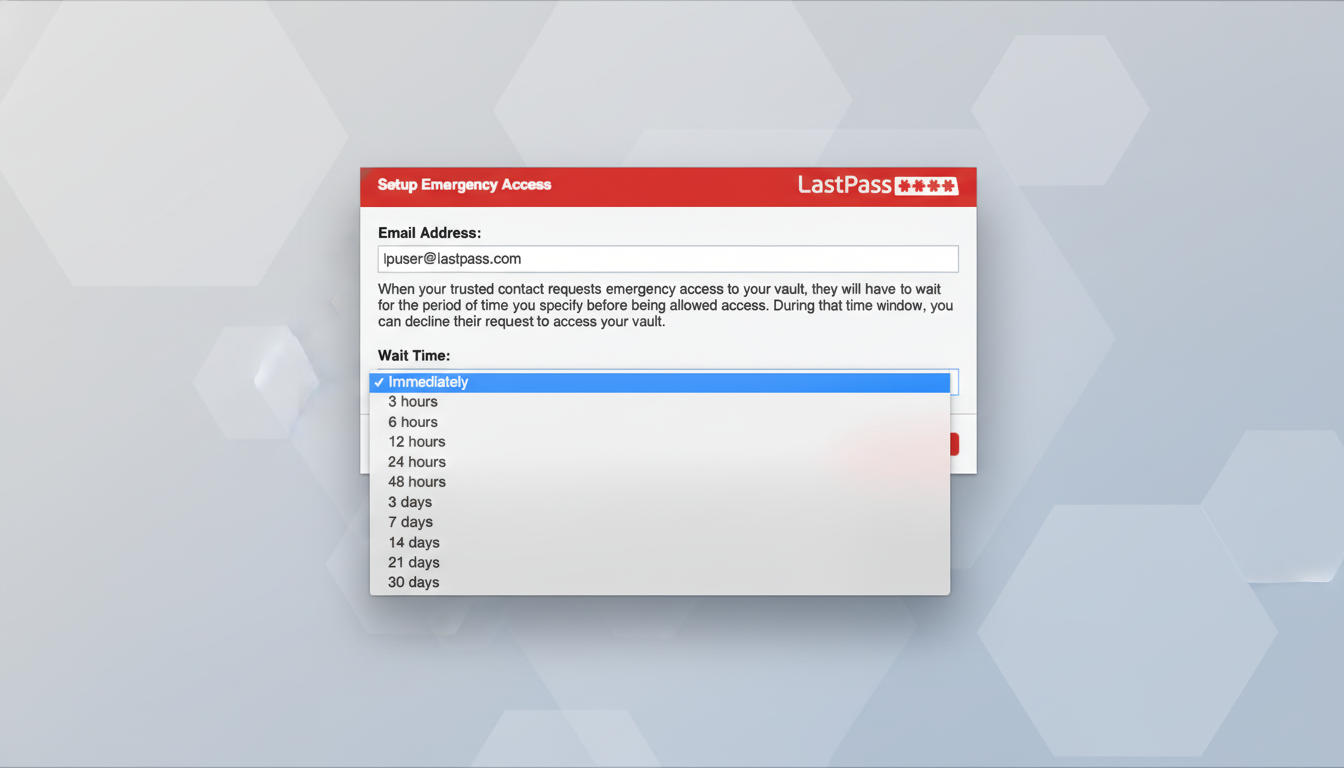
Tighten Emergency Access. Go over who you have designated, verify contact information, and perhaps institute a longer waiting period to issue the request in order to provide yourself with more time to rebuff possible fraudulent requests when an alert lands in your inbox.
Report and contain.
- Report suspicious emails to your mail provider’s abuse team.
- Report the site to trusted security groups such as APWG.
- Alert LastPass support so they can take down domains more quickly.
“The bottom line: they can make the page look beautiful, but it’s the journey you are sent down,” he said. Consider any recovery or legacy alert as a cue to go verify inside your vault — rather than typing in your master password on a page you didn’t manually visit.

