Near-field communication, or NFC, is the close-range wireless tech that powers tap-to-pay, transit gates, hotel keys and those stickers that launch an app when you tap them with your phone. It’s designed for fast, secure exchanges of very small amounts of data at a very short range — usually a few centimeters — so you get instantaneous, intentional interactions without the tedium of pairing or password entry.
Anatomy of a system There are at least two principal components to any NFC system: passive NFC tags, which store their tiny bit of data, and powered NFC readers, such as an active smartphone, which energise the passive tag so that it can transmit the data it contains. Here, in an easily understood guide, is a practical look at what each of them does, how each of the components works and how the whole system operates.
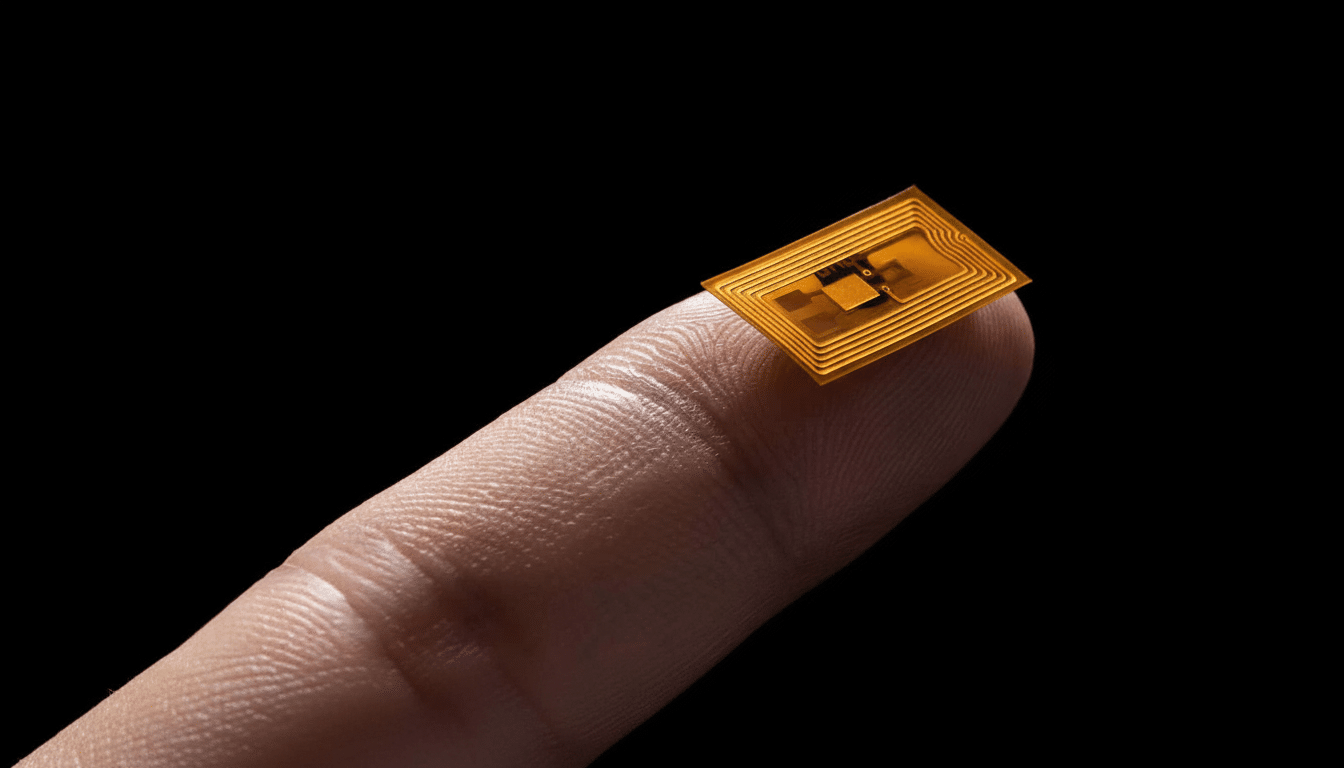
What is an NFC tag and NFC reader?
An NFC tag is a small chip containing a copper antenna coil around it — commonly hidden in a sticker, card, wristband, or product packaging. The chip contains a tiny amount of data — perhaps a web address, or a Wi‑Fi password, or a digital ticket for a subway ride, or a soda can — which can be read by other devices, no battery or network connection necessary. With no battery, the tag waits quietly until a reader gets close.
An NFC reader: creates a magnetic field, powers the tag, and communicates with a tag. Readers can include payment terminals, transit gates, door controllers, and most modern smartphones. Phones get a little crazier: They can also emulate a card for payments or access, and they can write data to tags they touch.
How NFC actually works
NFC works at 13.56 MHz and employs magnetic induction between the two coils – one installed in the reader, one in the tag. When you bring it within a couple of inches, the reader’s field powers up the tag. The tag then “talks back” by minutely altering the load on that field (a process called load modulation), encoding binary data that the reader can then decode.
OSTI Data rates are typically from 106 to 424 kbps and the practical range is generally < 4 cm. Those magnetic fluctuations then get turned into 1s and 0s by coding schemes like Manchester or modified Miller; of course, you never see those bits — the reader passes the payload to the operating system on your phone, which opens the right app or takes the right action.
NFC has three modes: reader/writer (your phone reads a tag), peer-to-peer (two devices share small amounts of data), and card emulation (your phone pretends to be a contactless card). That latter mode supports tap-to-pay services operated under EMVCo guidelines.
Standards, types, and capacity
Consumer tags tend to use ISO/IEC 14443 (Type A/B) or ISO/IEC 15693 for longer range “vicinity” tags, with the NFC Forum defining ways in which they a) interoperate and b) use the NDEF data format. (1) The Forum defines tag Types 1 – 5, ranging from ultra-low-cost, low-capacity tags to high-capacity, high-speed tags.
The capacity range is a few bytes to tens of kilobytes. These are typically around 144 user memory bytes (which is enough for a URL or a short instruction set) for popular chips like NXP’s NTAG213, while next-generation “Type 5” tags can offer up into the tens of kilobytes for applications like ticketing and asset management. According to ABI Research / the NFC Forum, NFC is very widely available having been embedded in billions of card readers and phones and able to cost only a few cents in volume.

Things you already know you do everyday
Payments and transit are the most obvious applications. Tap phone or card at a terminal, and the reader verifies credentials and approves the transaction. ‘Financial-grade’ implementations mean tokenisation and secure elements, per EMVCo—your actual card number never leaves the device.
Beyond payments, tags can simplify the act of pairing headphones, sharing a Wi‑Fi network, opening support pages on retail displays, managing assets in a warehouse or controlling a smart home. Museums employ tags — for interactive exhibits; offices do for badges; logistics outfits to verify chain-of-custody with tamper-evident silicon.
Read and write tags from your phone
NFC is present in a majority of mid-range to high-end phones. To read a tag, just hold the back of the phone up to one and a prompt will open the correct app or display the stored information. As for writing, apps which support the NFC Forum’s NDEF format will allow you to write URLs, messages, contacts, stationary and Wi‑Fi details to rewritable tags like NTAG213/215/216.
You are free to lock tags to be read-only or use a password to restrict reading or writing. Combine a tag with automation — Shortcuts on iOS, or Tasker on Android — to automate things like setting your phone to Do Not Disturb at your bedside or tapping your car mount to open navigation and Bluetooth.
Security, privacy, and limits
NFC’s limited range is a feature, not a bug: you need to be very close to connect, limiting drive-by attacks. When it comes to payments and access control, security is provided by the architecture (secure elements, tokenization and cryptographic protocols defined by EMVCo and standards bodies) and not just the radio.
Basic stickers can be cloned, so don’t use unprotected tags for anything that is sensitive. If you need something more rugged, look for a chip with cryptographic authentication or tamper detection, like the secure industrial tags from STMicroelectronics or NXP. As for digital identities keys, physical tokens with NFC are certified by the FIDO Alliance to combat against phishing.
NFC vs Bluetooth, UWB and RFID
NFC is based on high-frequency RFID, but introduces standards for two-way, secure communications. It’s purposefully close-range and low-info, perfect for taps. The other characteristic, Bluetooth Low Energy, travels meters and is more suited to continuous connections, like audio. Those enhancements and support for ultra-wideband will give you precise location for finding devices. Most trackers blur them all together: a Bluetooth/UWB tracker will contain a small NFC tag just for quick tap-to-identify.
Bottom line: NFC tags and readers make a living off of instant, intentional, secure actions. If a tap can replace opening a menu, or typing a password, or following a pairing instruction, then NFC is going to be the quickest solution at doing it.

