A newly surfaced Android spyware toolkit dubbed ZeroDayRAT is being peddled to cybercriminals and promises sweeping control over victims’ phones — from live location and camera feeds to banking credentials and one-time passcodes. Mobile security researchers who analyzed the tool warn that even low-skilled attackers can use it to mount high-impact theft and surveillance campaigns.
What Researchers Found Inside the ZeroDayRAT Spyware Toolkit
According to a technical breakdown from iVerify, ZeroDayRAT is being marketed and distributed through Telegram channels. The kit targets Android devices running versions 5 through 16 and relies on convincing a victim to install a malicious APK. Once installed, an operator-facing dashboard exposes a trove of device and personal data with minimal effort.
- What Researchers Found Inside the ZeroDayRAT Spyware Toolkit
- Why Banking and Cryptocurrency Users Face Elevated Risk
- How ZeroDayRAT Spreads and Which Victims Are Being Targeted
- Why This Feels Like a Turning Point for Mobile Surveillance
- What You Can Do Now to Protect Your Phone and Finances
- What We Still Don’t Know About the ZeroDayRAT Capabilities
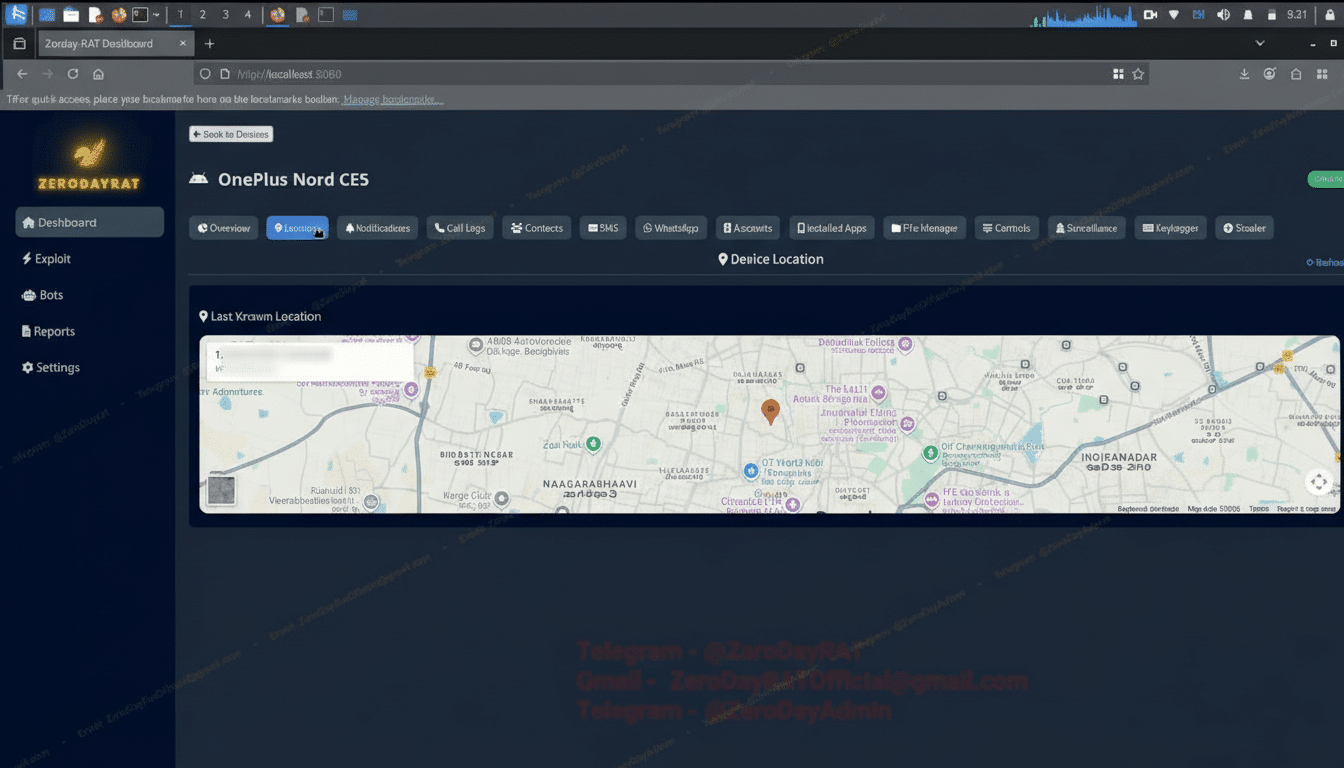
The dashboard enumerates phone model and OS details, SIM information, installed apps, and a complete log of incoming notifications. It can track a target’s location in real time, list all accounts registered on the device, and read SMS — including OTP codes often used for two-factor authentication. Researchers say the tool also enables live access to the microphone and cameras and can stream the device’s screen to the attacker.
While the current spotlight is on Android, investigators note that iOS modules are also being advertised to buyers, signaling an intent to operate across mobile ecosystems. Details on iOS capabilities remain limited, but the cross-platform sales pitch underscores the commercial surveillance trend now seeping into commodity crimeware.
Why Banking and Cryptocurrency Users Face Elevated Risk
ZeroDayRAT’s data access translates directly into financial risk. With notification logs, SMS reads, and potential keylogging or screen streaming, attackers can capture banking app credentials and intercept OTPs to bypass login protections. iVerify’s analysis also highlights clipboard manipulation — a tactic commonly used to swap cryptocurrency wallet addresses at the moment of transfer, silently diverting funds.
Security firms have long warned that Android banking threats increasingly blend multiple techniques: overlay attacks that mimic real app screens, Accessibility Service abuse to read content, and notification interception to grab codes. ZeroDayRAT packages many of the same outcomes behind a slick operator console, lowering the barrier to monetization for would-be thieves.
The wider risk context is sobering. The FBI’s Internet Crime Complaint Center continues to report record cybercrime losses, and blockchain investigators such as Chainalysis have flagged address-replacement malware as a persistent theft vector in the crypto ecosystem. Toolkits like ZeroDayRAT make such schemes easier to scale.
How ZeroDayRAT Spreads and Which Victims Are Being Targeted
Distribution through Telegram suggests operators are leaning on social engineering to drive installs: phishing messages, “urgent” support chats, or promises of cracked apps pushing victims to sideload an APK. Once the user taps install and grants requested permissions, the attacker’s dashboard lights up with live telemetry.
This is classic malware-as-a-service. Rather than building their own spyware, buyers pay for access to a ready-made kit and a control panel. Even if specific Telegram channels get taken down, copies in the wild can keep circulating among subgroups and private chats, sustaining the threat.

Why This Feels Like a Turning Point for Mobile Surveillance
Investigators note that capabilities once associated with nation-state implants — live mic and camera access, granular account discovery, and real-time screen streaming — are now packaged for the criminal market. That democratization of surveillance tradecraft mirrors trends seen with other mobile families, from banking trojans like Xenomorph and Anatsa to commercially sold spy suites.
The protective net is imperfect. Google reports blocking well over 2 million policy-violating submissions to the Play ecosystem annually, and Play Protect can scan some sideloaded packages in real time. But if a victim explicitly installs a malicious APK and taps through warnings, traditional storefront defenses may be bypassed.
What You Can Do Now to Protect Your Phone and Finances
Only install apps from trusted sources and avoid sideloading APKs sent over messaging apps, email, or social media. If you must sideload, validate the developer, verify checksums where possible, and scrutinize requested permissions — especially Accessibility, Notification access, SMS, and Device Admin.
Enable Google Play Protect and heed its warnings. Keep Android and Google Play system updates current, and turn on automatic updates for core apps. Review your device’s permission settings and revoke access that an app doesn’t clearly need to function.
For banking and crypto, use app-based authenticators or security keys instead of SMS when available. Before confirming a crypto transfer, double-check that the destination address matches your intended recipient; clipboard hijacking often changes only a few characters in the middle, hoping you won’t notice.
If you suspect infection, disconnect from networks, back up personal photos and documents, and perform a factory reset. Afterward, change passwords from a clean device, revoke logged-in sessions for email and financial accounts, and re-enable 2FA. Enterprises should consider mobile threat defense tools and restrict sideloading via MDM policies.
What We Still Don’t Know About the ZeroDayRAT Capabilities
Open questions remain around ZeroDayRAT’s persistence methods, whether it employs root exploits, and how it evades mobile security tools. The sellers’ claims about iOS support also need independent validation. What is clear is the direction of travel: full-spectrum mobile surveillance is no longer the realm of elite operators — it’s being commoditized and marketed in chat rooms.
The best defense is vigilance. Treat unexpected app installs and permission prompts as red flags, and assume that anything granting access to messages, notifications, or screen content could be weaponized against your money and your privacy.

