A web tool called Jmail is transforming an unwieldy document dump of Jeffrey Epstein’s correspondence into an easily searchable, Gmail-like inbox available to anyone. Based on the released email files that were posted by the House Oversight Committee, this project provides an inbox-style browser so readers can digest the threads, search for names, and follow conversations without scrolling through disjointed PDFs or text files.
Jmail is not an exploit and does not pull a live account. It’s a user interface built on top of public records, creating an E-ZPass clear through the 10-cent history to make a splintery archive navigable for journalists, researchers, and anybody else.
- What Jmail Does: Turning Document Dumps Into an Inbox
- Who Built Jmail and Why the Creators Launched the Tool
- Why the Design of an Interface Is Important in Investigations
- What Early Readers Are Saying About Jmail’s Usability
- Legal and Ethical Boundaries for This Public Email Archive
- The Bottom Line: A Simpler Inbox for Complex Records

What Jmail Does: Turning Document Dumps Into an Inbox
At heart, Jmail transforms dozens of discrete files into an inbox as familiar-seeming as any you’ve ever seen. Messages are organized into Inbox and Sent views; subject lines scan quickly; conversations group together threads so readers can follow context rather than opening dozens of isolated documents.
The tool’s search box functions much as you’d expect in a modern email client. You can search for names, organizations, or keywords and leap directly to messages that include those terms. A Starred tab features messages visitors found noteworthy, while a People clump serves as a live contact sheet, spotlighting people who figure largely in the trove.
Who Built Jmail and Why the Creators Launched the Tool
Jmail is produced by creator Riley Walz (a Wired interview calls him “the prankster behind a series of provocative web experiments”) and developer Luke Igel. Their goal is simple, if ambitious: instead of the haphazard array of clunky scans and plain-text exports that you’re typically faced with from hackers stealing graphics out of your inbox, create a well-structured interface that makes sense to anyone who’s ever used a mainstream email service.
And in practice, that means parsing filenames, normalizing timestamps, extracting text from PDFs, and indexing content so the search functions quickly. It’s the unglamorous data-wrangling that turns raw dumps into coherent narratives — the kind of plumbing that newsrooms routinely put in for large investigations behind the scenes.
Why the Design of an Interface Is Important in Investigations
Usability documentation from the Nielsen Norman Group has consistently shown how well-understood patterns minimize cognitive load and time-on-task for known-item search. You can call it straight up: folks are accustomed to the layout, which aids them in finding what they want with quicker and more accurate browsing.
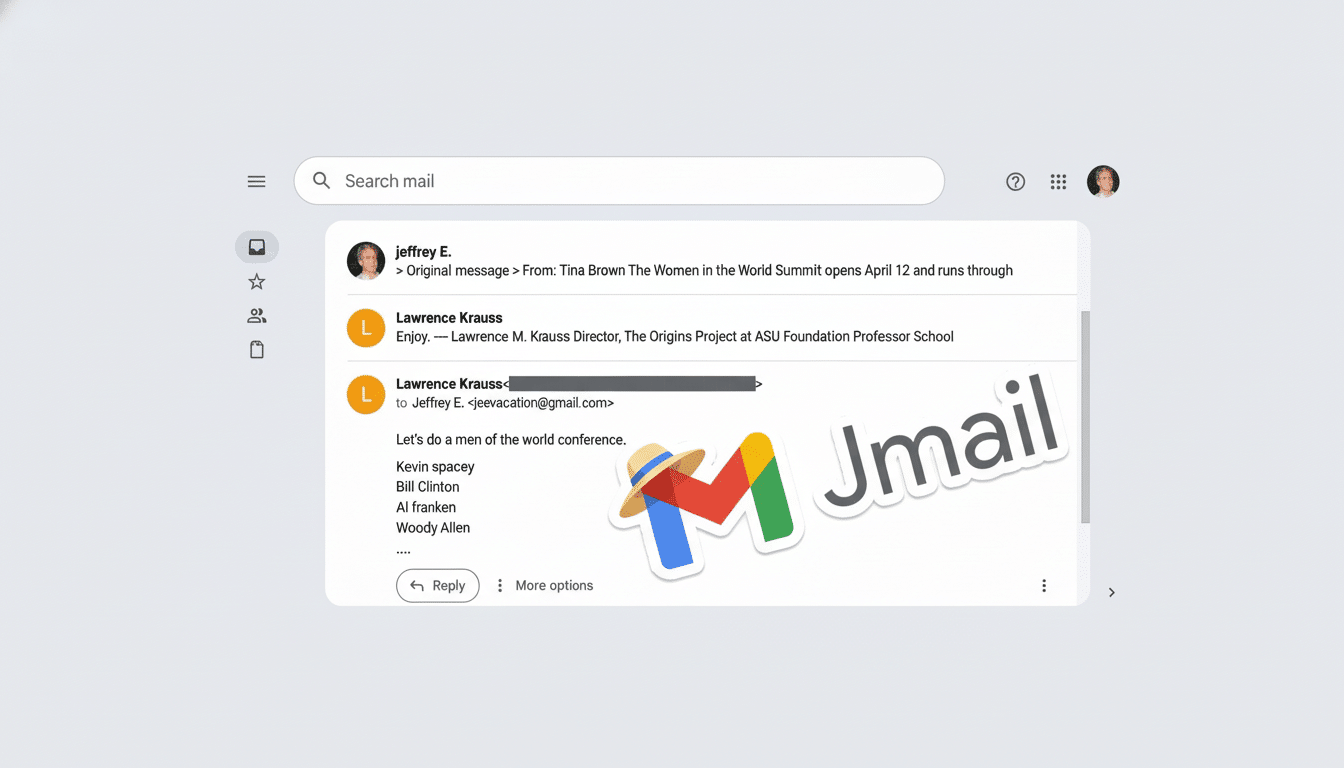
Projects like DocumentCloud, through which investigative outlets and journalists can annotate and share primary-source files, are a testament to how interface choices deeply shape the things that journalists are able to find. Jmail brings that same reasoning to the world of email, where conversation threading and sender-centered browsing can turn readings — who wrote whom at what frequency on what topics — that are transparent only in a stack of static files.
What Early Readers Are Saying About Jmail’s Usability
The Oversight Committee’s publication has fueled intense public interest, not least because the correspondence features a wide cast of prominent subjects from finance, academia, and technology. The dossier has also been scoured for connections and timelines, as reports have focused on contacts with high-profile figures like economist Larry Summers and others.
Jmail does not pretend to adjudicate the meaning of a message at every point along its trajectory; it merely makes them more legible in series. That context is crucial. Threaded views let you see who started a conversation, what it became, and whether the subject line of an email reflects substance or routine logistics — distinctions lost in raw dumps.
Legal and Ethical Boundaries for This Public Email Archive
Note once again: Jmail doesn’t access any account without permission from the user, nor does it bypass security. It’s a front end to material that has already been disclosed by a congressional committee. That’s a legal and ethical distinction that matters, especially in an environment where digital forensics experts highlight the importance of provenance, chain of custody, and potential tampering with documents.
Careful readers should still meet any given message with caution. Emails are but one piece of evidence in a larger evidentiary picture, and they are generally stronger if corroborated. Community standards from organizations like the Tow Center for Digital Journalism advise doing such basic fact-checking as verifying identities, looking to see if dates line up across sources, and drawing back from the magnetic pull of over-interpretation of isolated lines.
The Bottom Line: A Simpler Inbox for Complex Records
By recasting a haphazard release as a familiar inbox, Jmail lowers the bar for any serious reading about or through Epstein’s correspondence. It’s a deceptively simple notion, executed with care: get the interface out of the way, and let the documents speak for themselves — and let researchers spend less time wrangling files and more time asking better questions.

