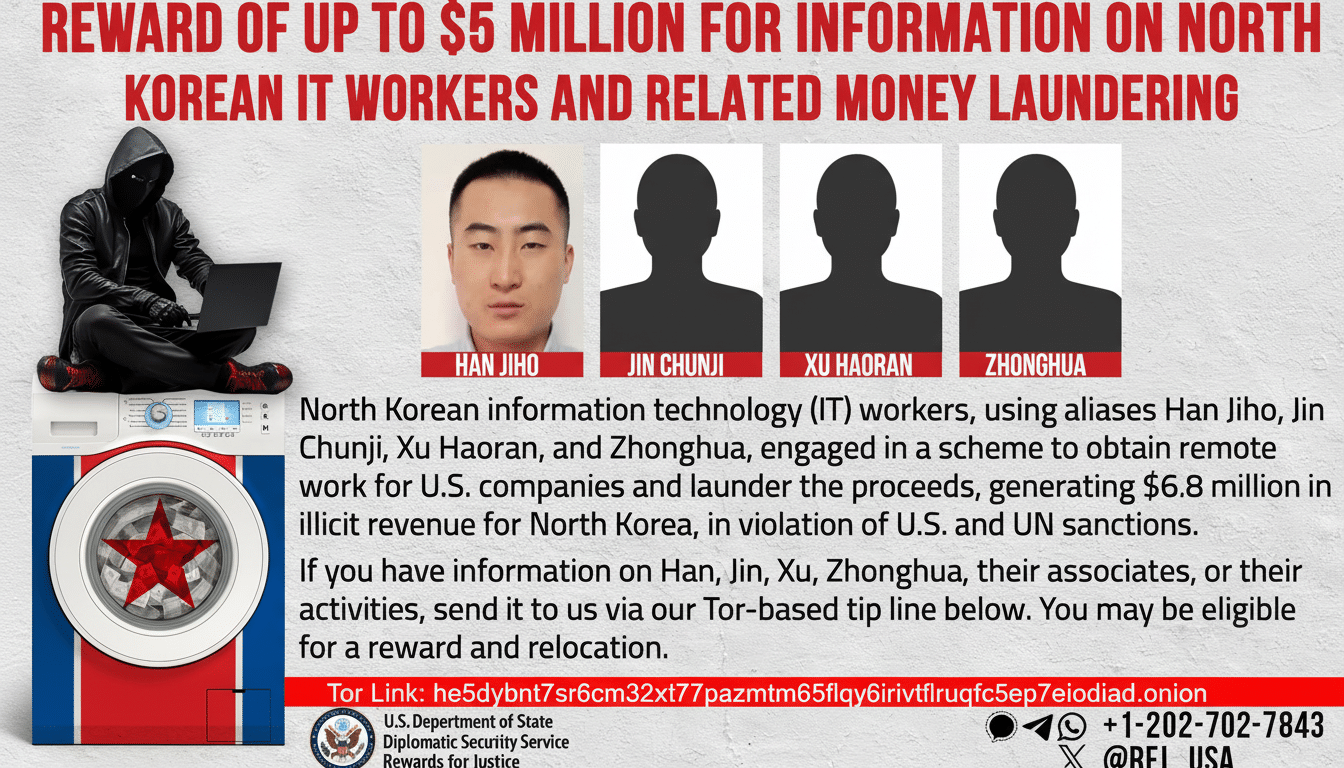
Five people have confessed to assisting North Korean agents in posing as U.S.-based remote IT workers whose services were tapped for the networks and payrolls of 136 American businesses, which funneled funds back to Pyongyang, according to the Department of Justice. Prosecutors said the operation hijacked stolen identities, domestic internet footprints and company-issued laptops to present foreign workers as hired locally with such convincing that at least $2.2 million went to the regime.
How the North Korean Remote IT Worker Network Operated
Investigators also detail a legion of U.S.-based “facilitators” who loaned real, fake or stolen identities to North Korean IT workers while hosting corporate laptops in their houses so access looked like it came from American IP addresses. The setup assisted foreign workers in passing onboarding checks and assuming day-to-day operations, including testing negative for drugs or bad background vetting — by fobbing those off on a stand-in.
Three U.S. citizens — Audricus Phagnasay, Jason Salazar and Alexander Paul Travis — pleaded guilty to wire fraud conspiracy for allowing employment in their names as well as providing remote access to the company’s devices.
Travis, at the time an active-duty member of the U.S. Army, earned more than $50,000; Phagnasay and Salazar each received no less than $3,500 and $4,500 respectively for their parts in the conspiracy, prosecutors said.
A third defendant, Erick Ntekereze Prince, operated out of Florida under the name Taggcar and provided “certified” IT workers to U.S. firms even though he knew they lived outside the United States and had used fraudulent documents, according to prosecutors. Prince stored the remote-access laptops at several homes and collected at least $89,000.
Oleksandr Didenko, a Ukrainian national, pleaded guilty to wire fraud conspiracy and aggravated identity theft after he sold the identities of American citizens to North Korean IT workers who subsequently obtained employment at more than 40 companies. As part of the plea bargain, he agreed to forfeit $1.4 million.
Scope of the Infiltration Across 136 U.S. Companies
American companies had what the Justice Department described on Thursday as a collective moment of doubt and ended up inadvertently contributing about $1.28 million to salaries for these so-called employees, with the majority of that money flowing to operatives outside their home countries. Officials said they had frozen and seized some $15 million in cryptocurrency linked to North Korean hacking crews — evidence that payroll fraud, identity crime and cybertheft have become overlapping revenue streams for a heavily sanctioned state.
U.S. agencies have warned for years that North Korean IT workers carry assumed personas, frequently with glossy resumes, credible GitHub portfolios and references cooked up through broker networks. Public advisories from the F.B.I., CISA and the Treasury Department outline tactics including beefed-up identity fraud, the use of residential proxies or “laptop mules” to spoof locations where applications are launched, and coordinated interview coaching to defeat vetting.
Why Remote I.T. Jobs Became a Strategic Target for Pyongyang
Distributed work also made it easier for bad actors to hide their true location of residence and work. Many companies depend on third-party staffing firms, remote onboarding and automated checks that prize velocity over due diligence. That leaves room for suave fakes who are able to procure stolen identity documents, disguise U.S. internet footprints and practice technical interviews. For North Korea, the benefit is strategic: steady hard-currency earnings with relatively low operational risk compared with high-profile hacks.

U.N. and independent security analysts have documented how salaries from IT work can be taxed, coerced or otherwise captured by the state. In addition to the headline-prominent thefts of entire networks by groups like Lazarus, this whispering wage stream is a dependable sanctions-evasion vehicle that mixes into normal corporate processes.
Red Flags Companies Missed in Remote Hiring and Payroll Security
Cases like these reveal repeated failings:
- Identity proofing confined to document scans
- Inconsistent IP geolocation checks
- The unchecked use of remote-access tools
- A willingness to accept candidates who refuse video or in-person verifications
Employers also report oddities like:
- Strange work hours across time zones
- Requests to have pay rerouted to third parties
- The same resumes traveling under different names
Experts advise a layered approach:
- High-assurance identity verification in line with NIST guidance
- Device geofencing and telemetry that alerts on repeated VPN or proxy use
- Continuous user-behavior analytics
- More rigorous contractor onboarding with in-person or supervised verification, whenever possible
Here are a number of tips that payroll and vendor management teams can use to screen against OFAC’s list of sanctioned entities and monitor for rapid banking information, phone numbers or physical address changes.
Legal and Security Risks for Employers and Their Contractors
In addition to the fraud losses, companies are at risk of sanctions exposure if funds or services go to designated entities, even inadvertently. The DOJ indicated that coordination will continue between criminal, sanctions and civil recovery actions — which means indictments, asset forfeiture and cryptocurrency seizures will run in parallel. The warning message from prosecutors is stark: facilitating disguised North Korean labor, whether intentionally or through negligence, carries genuine legal risk.
For boards and security leaders, the conclusion is to consider workforce integrity as a cyber risk. Code signing, endpoint security and vendor access should be the same standard as governance, identity proofing and the controls around remote work. The infiltration of 136 companies was not a one-time proposition; it’s a playbook that can be repeated. The faster companies close these gaps, the less appealing they are to state-sponsored fraud networks.

